IT Security Risk and IT Asset Management: What Every IT Leader Must Know
IT Security Risk and IT Asset Management are closely linked. Poor visibility increases threats. Strong ITAM boosts security and compliance.
Here’s the problem: most IT teams don’t have a full picture of what assets they actually have. Old laptops sitting in storage, forgotten software licenses, cloud tools no one’s using anymore, these unmanaged or unknown assets are more than just clutter. They are risks. Big ones.
Every untracked device or outdated app creates an open door for cyber threats. And in a world where security breaches are more common and more expensive than ever, that’s a serious problem.
The truth is, you can’t protect what you don’t know exists. That’s where IT Asset Management (ITAM) comes in, and why it matters much more to your security than most people think.
What Is IT Security Risk? Why Should IT Leaders Care?
An IT security risk is the possibility that your organization’s data, systems, or operations could be exposed or disrupted due to a cyber threat. These risks often come from gaps you didn’t know existed, like unmonitored devices, outdated software, or cloud environments that were set up and forgotten.
As IT leaders, you're expected not just to manage infrastructure but also to protect it. And here's the uncomfortable truth: most security risks start with poor visibility.
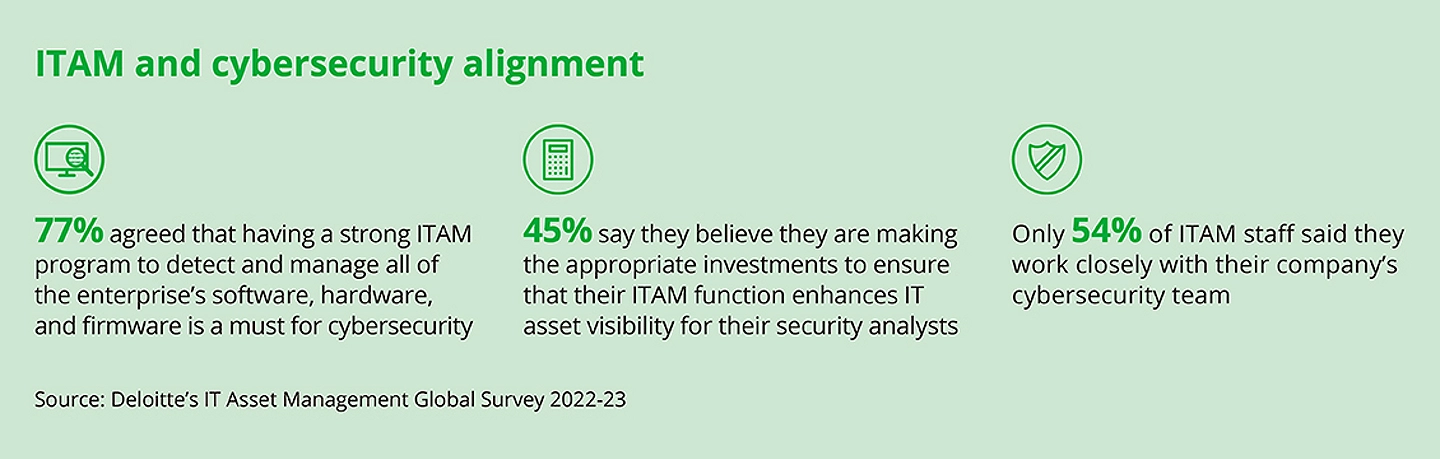
According to Deloitte’s 2022–23 Global IT Asset Management Survey, 77% of IT professionals agree that having a strong ITAM program is essential for cybersecurity. But fewer than half (only 45%) believe their organization is making the right investments in ITAM to help their security teams see and manage threats.
The survey also found:
- Just over half (54%) of ITAM staff say they work closely with cybersecurity teams.
- A lack of collaboration between ITAM and security is now a top concern for many organizations.
- And as companies adopt more technologies and expand into multiple cloud environments, data and devices become harder to track and easier to attack.
Regulators are also catching up. New and updated security standards are starting to emphasize the need for full visibility of IT assets, making ITAM a growing part of compliance.
So why should IT leaders care? Because you can’t secure what you can’t see. And without proper IT asset management, you’re leaving the door wide open to cyber threats.
IT Asset Management (ITAM) and Cybersecurity
IT Asset Management (ITAM) isn’t just about tracking hardware and software anymore. It’s about building a foundation of visibility and control that supports everything from operations to security and compliance.
At its core, ITAM is the practice of identifying, tracking, and managing all of your IT assets, like laptops, servers, applications, cloud instances, mobile devices, and even firmware throughout their lifecycle.
So, where does cybersecurity come in?
Simple: Security teams need to know what exists in order to protect it.
Cybersecurity teams depend on ITAM to:
- Get a full inventory of devices and systems connected to the network
- Spot unauthorized or unknown assets that may pose a hidden risk
- Track software versions and update status to avoid unpatched vulnerabilities
- Ensure only approved and compliant tools are being used across the organization
- Quickly locate and assess impacted assets during a security incident
Trying to secure your environment without a full asset inventory is like guarding a building and ignoring the side doors and windows that were never mapped.
And yet, as Deloitte’s survey revealed, many organizations still treat ITAM and cybersecurity as separate functions. That lack of connection creates blind spots, delays, and higher risk.
Bringing ITAM and cybersecurity together creates a stronger, smarter, and more responsive IT environment. One that’s better equipped to detect threats early, close vulnerabilities fast, and stay ahead of compliance requirements.
How Poor ITAM Practices Increase Security Risk
When IT asset management is weak or neglected, it leaves gaps that cyber threats can easily exploit. These gaps aren’t always obvious, but they often become the entry points for attacks.
Real-World Example: The Forgotten Laptop That Opened the Door
Picture this: an employee leaves your company, but their laptop is never collected or removed from the system. Months later, the device connects to the network. It's still using saved credentials and hasn’t received a single security update. That outdated machine becomes an open door and an easy target for attackers. And because no one even knows it's still out there, the threat goes undetected until it’s too late.
This kind of scenario is more common than you might think.
Common Ways Poor ITAM Leads to Risk
- Outdated or unpatched systems stay online and vulnerable to known exploits.
- Shadow IT devices or apps set up without IT’s knowledge don’t follow security standards and can’t be monitored.
- Leftover accounts and unused licenses often go unnoticed after people leave or projects end, but they may still have access to critical systems.
- Delays during incidents happen when security teams don’t have up-to-date information about what assets exist, where they are, and who owns them.
- Regulatory non-compliance becomes a real concern when asset data is incomplete or inaccurate, especially in industries like healthcare, finance, or government.
Every unknown or unmanaged asset increases the risk of a breach. Whether it’s a forgotten device, an outdated server, or an unapproved app, poor ITAM creates blind spots. And in cybersecurity, blind spots are dangerous.
How ITAM Helps Reduce IT Security Risk
A well-structured IT Asset Management (ITAM) system doesn’t just organize your tech inventory. It actively helps reduce your exposure to cyber threats. The more accurately and efficiently you manage your assets, the fewer places attackers have to hide.
1. Real-Time Asset Discovery Prevents Blind Spots
A company deploys automatic asset discovery tools that scan the network daily. One morning, the system detects a personal device connected to the corporate Wi-Fi running unauthorized software.
Impact: The security team is alerted immediately and blocks the device before it can access sensitive data.
Why It Matters: Unknown or unmanaged devices can’t be secured. Real-time asset tracking helps identify rogue connections and shadow IT before they create risk.
2. Software Version & Patch Tracking Closes Vulnerabilities
A patch for a major vulnerability in a popular remote desktop tool (e.g. AnyDesk or TeamViewer) is released. The ITAM system instantly shows which 12 endpoints still have the vulnerable version installed.
Impact: IT can deploy the patch to just those systems within hours—without wasting time scanning everything manually.
Why It Matters: Fast, targeted response keeps known vulnerabilities from being exploited.
3. ITAM-Driven Alerts Catch Risky Behavior Early
A user installs an outdated, non-compliant file-sharing app. The ITAM platform flags the unauthorized software and sends an alert to IT security.
Impact: The device is quarantined, and the user is notified. IT investigates and removes the app before it causes harm.
Why It Matters: Security risks often start with small actions—unauthorized apps, license violations, or unsupported tools. ITAM helps detect and respond in real time.
4. Faster, More Accurate Incident Response
A threat detection system flags suspicious activity coming from an IP tied to a company-issued tablet. Using the ITAM database, the security team pulls up details: it belongs to a remote contractor who was offboarded last week.
Impact: Access is shut down immediately. The ITAM record shows the asset was never returned or wiped, prompting a review of offboarding procedures.
Why It Matters: Fast access to asset metadata (owner, location, software, usage) is critical for containing and investigating threats.
5. Audit-Ready Documentation Supports Security Compliance
Use Case: During a security audit for ISO 27001, an auditor requests proof of how all endpoints are managed and monitored.
Impact: IT generates a full asset report from the ITAM platform within minutes, showing compliance across all tracked devices.
Why It Matters: Security standards increasingly require full visibility. A reliable ITAM platform keeps you compliant and ready for any audit.
What Every IT Leader Needs to Do
Security risks tied to unmanaged assets aren’t just a technical issue; they’re a leadership responsibility. IT leaders play a key role in bridging the gap between asset visibility and cybersecurity protection. That starts with turning ITAM from a background process into a core part of your security strategy.
1. Make ITAM a Shared Responsibility Between IT and Security
Break down silos between IT operations and cybersecurity. Align both teams around a shared goal: full visibility and control over all assets. Encourage joint planning, shared tools, and regular syncs.
Tip: Appoint an asset management lead who works closely with your CISO or security team.
2. Invest in Automation for Asset Discovery and Monitoring
Manual asset tracking is outdated and error-prone. Use ITAM platforms that automatically discover, classify, and update assets across your network—including on-prem, remote, mobile, and cloud environments.
Look for: Tools that integrate with security systems like SIEM, endpoint protection, and vulnerability scanners.
3. Implement Clear Lifecycle Processes
Every asset should have a defined lifecycle from purchase to decommission. Set policies for how devices and software are onboarded, monitored, updated, reassigned, and retired.
Example: Ensure offboarding checklists include asset return, wipe, and removal from inventory.
4. Monitor Software Usage and License Compliance
Unlicensed or outdated software often goes unnoticed and unpatched. Track all software assets, their usage, and update status. This improves security and reduces costs.
Pro tip: Build reports that flag unauthorized or unused software monthly.
5. Use Asset Data to Drive Security Metrics
Treat ITAM data as a source of insight. Use it to track:
- Percentage of assets unpatched
- Number of unauthorized devices detected
- Average time to isolate risky endpoints
- Asset compliance score by department
Why it matters: These metrics help prove the value of ITAM to leadership and justify future investments.
6. Prepare for Regulations That Expect Full Asset Visibility
Compliance standards are shifting. Frameworks like ISO 27001, NIST, HIPAA, and GDPR increasingly expect organizations to demonstrate complete knowledge of their IT environments.
Action step: Map your current ITAM process against any regulatory frameworks relevant to your industry.
Conclusion
The connection between IT Asset Management and IT security risk is no longer optional; it’s essential.
Every device you don’t track, every piece of software you don’t manage, and every asset that falls through the cracks adds risk. Real risk. And in today’s complex environments, asset blind spots are one of the biggest threats to your cybersecurity posture.
The good news? IT leaders have the power to change that.
By treating ITAM as a core part of your security strategy, not just an inventory checklist, you gain visibility, control, and speed. You reduce vulnerabilities before they’re exploited. You respond to threats with clarity. And you prepare your organization for both compliance and growth.
ITAM is not just about what you own. It’s about what you protect.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


