Laptop Inventory Policies Every Company Should Have
Discover essential laptop inventory policies that prevent loss, improve security, and ensure compliance, plus tools like barcode scanning for enforcement.
Laptops go missing more often than most companies realize. Sometimes it’s an honest mistake, an employee leaves it in a café or forgets to return it after a project. Other times, it’s a security risk when sensitive data ends up in the wrong hands.
The common thread in these situations? A lack of clear laptop inventory policies. Having laptops is easy. Managing them responsibly is where companies often struggle.
In this blog, we’ll look at the essential policies every company should have in place, and how simple tools like barcode scanners can help keep track of devices with less effort.
Why Laptop Inventory Policies Are Essential
Laptops are valuable assets. They carry sensitive data, travel with employees, and represent a significant cost to the business. Without clear policies, laptops can be lost, misused, or left unprotected.
Here’s why laptop inventory policies matter:
- Prevent loss and theft: Every laptop is logged, tagged, and assigned, making it easier to notice when one goes missing.
- Protect company data: A laptop isn’t just hardware; it often contains confidential files. Policies on encryption, reporting lost devices, and remote wiping protect against data breaches.
- Ensure compliance: Regulated industries like healthcare and finance require strict device control. Policies make audits smoother and reduce the risk of penalties.
- Control IT costs: Laptops are expensive to replace. IT asset lifecycle management and maintenance policies extend device use and help plan upgrades instead of reacting to failures.
- Standardize processes: Without policies, different teams may track laptops in different ways. Standard rules ensure consistency across the organization.
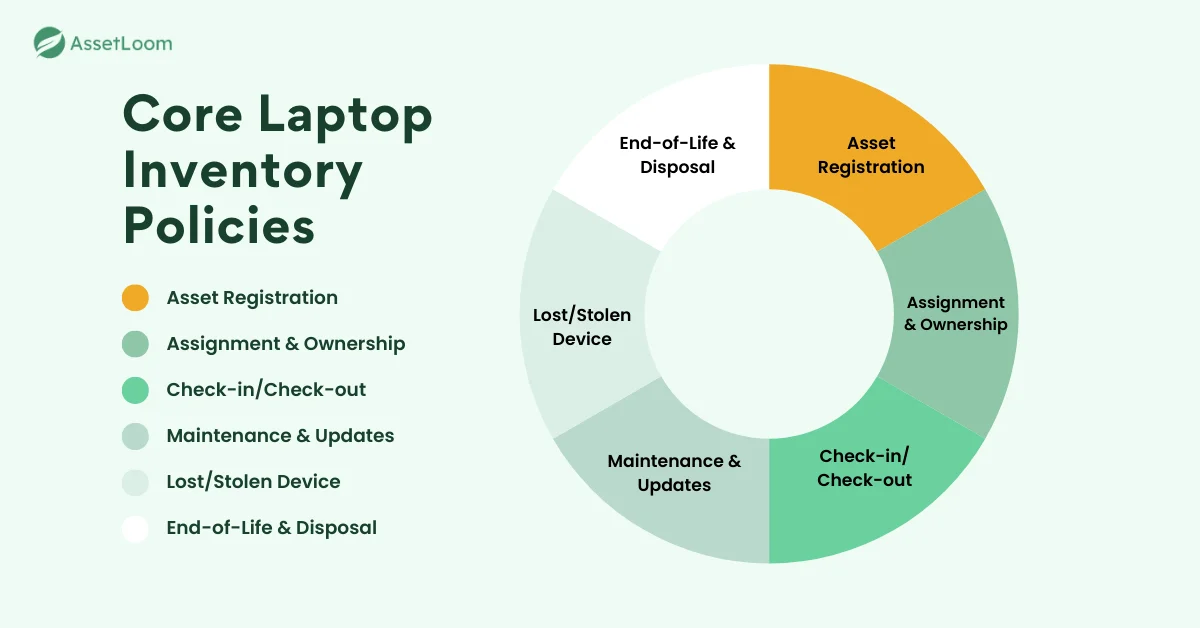
Core Laptop Inventory Policies Companies Should Enforce
1. Asset Registration Policy
The first step in laptop inventory management is registration. If laptops aren’t logged as soon as they arrive, IT teams can lose track of them before they’re even handed out. Registration creates the foundation of accountability. It tells you what assets exist, who they belong to, and where they are. Without it, you risk having laptops in circulation that no one can trace, making audits and troubleshooting much harder.
What to record:
- Brand, model, and serial number
- Purchase date and cost
- Warranty details
- Department and assigned user
- Storage or office location
Example: When IT receives 20 new laptops, they log all details into the system right away. Even the laptops still in storage are visible, so nothing goes “off the books.”
Tip: Use IT asset management tools for consistency. Spreadsheets may work for very small teams, but they quickly become messy as the number of devices grows.
2. Assignment and Ownership Policy
Once a laptop is issued, accountability must be clear. An assignment policy ensures that every laptop has a designated owner, so responsibility is never in question. This reduces the chances of devices being misplaced or shared informally and sets expectations for how employees should care for company property.
Key points:
- Each laptop is assigned to one user or role
- Users are responsible for keeping the laptop secure
- Employees must report problems or loss right away
- Laptops must be returned when staff leave or change roles
Example: Employees sign an acceptance form when they receive a laptop. This form explains their responsibilities and stays on file in HR.
Tip: Digitize the process so you don’t rely on paper forms. Keep assignment records linked to HR or IT systems for easy tracking.
3. Check-in and Check-out Policy
Some laptops are not permanently assigned but kept in a pool for contractors, interns, or temporary staff. Without a clear check-in/check-out policy, these devices can easily vanish or sit forgotten in drawers. This policy ensures that even short-term users are accountable and that IT always knows where each laptop is.
How it works:
- Each loaner laptop has a unique ID or barcode
- IT records the user’s name, date, and expected return
- When the laptop comes back, IT checks its condition and updates the system
Example: During the summer, interns check out laptops from IT. When the program ends, all laptops are returned, wiped, and reassigned.
Tip: Add barcodes or QR codes to laptops. Scanning is faster and less error-prone than typing details into a spreadsheet.
4. Maintenance and Update Policy
Over time, laptops slow down, wear out, or become vulnerable to cyber threats if not updated. A maintenance policy ensures devices stay secure, reliable, and productive. It also extends their usable life, reducing costs for replacements. This is not just about installing updates; it’s about making sure laptops remain fit for daily work.
What to cover:
- Regular software and security updates
- Hardware checks (battery, hard drive, etc.)
- Diagnostics and performance monitoring
- Firmware and driver updates
Example: IT schedules a quarterly “laptop health day.” Employees drop off laptops for updates and quick checks before heading back to work.
Tip: Automate software updates with endpoint tools. Pair this with reminders for physical checks to reduce interruptions.
5. Lost or Stolen Device Policy
When a laptop goes missing, the damage can be far greater than the cost of replacing it. Data leaks, compliance failures, and security risks can all follow. A lost or stolen device policy tells employees exactly what to do, so IT can act fast to protect the company. Without this, delays in reporting can make recovery or data protection impossible.
Policy basics:
- Report lost devices immediately
- IT locks or wipes the laptop remotely
- Security or HR logs the case for compliance and insurance
- Replacement requests follow an approval process
Example: A salesperson loses a laptop on a trip. She reports it right away, IT wipes it remotely, and a replacement is issued within 48 hours.
Tip: Enable device tracking features and pair them with endpoint management tools for faster recovery.
6. End-of-Life and Disposal Policy
No laptop lasts forever. When devices are old or no longer meet performance standards, companies need a structured way to retire them. An end-of-life policy makes sure laptops are removed from circulation safely, sensitive data is destroyed, and disposal meets environmental and compliance standards.
Steps:
- Identify laptops due for replacement
- Back up important files
- Wipe or destroy the hard drive
- Remove asset tags and mark as retired in records
- Recycle, resell, or donate safely
Example: A company replaces laptops every four years. Old devices are securely wiped, then sold to a certified refurbisher. The income goes back into the IT budget.
Tip: Set reminders in your IT asset system to flag laptops that are nearing end-of-life. This gives you time to budget and plan replacements.
Enforcing Laptop Inventory Policies with Technology
Writing policies is only half the job. If employees forget to follow them, or if IT can’t keep up with manual tracking, the rules quickly lose their value. Enforcement ensures that policies aren’t just words on paper but part of everyday practice.
Barcode scanners for everyday tracking
One of the simplest ways to enforce policies is with barcode or QR codes. By tagging each laptop, IT can scan devices in and out quickly, update records instantly, and avoid mistakes from manual entry.
Imagine an employee borrowing a laptop for a project. Instead of filling out a paper form, IT scans both the laptop and the employee’s ID badge. The system records who has the device, the date it was checked out, and the expected return. If the laptop isn’t returned on time, an automatic reminder goes out. This creates accountability without adding extra work.
![]()
Automating updates and compliance
Enforcement isn’t just about tracking movement. Policies like maintenance and security updates also need support from technology. Endpoint management tools can push patches and updates to all laptops at once, ensuring devices stay secure. A good laptop asset tracking system can also flag devices nearing end-of-life, helping IT plan replacements before problems occur.
Start small and grow
The key is to make technology serve the policy, not complicate it. Start with simple steps like labeling laptops and scanning them during check-in/check-out. Once that process runs smoothly, add automation for updates, audits, and lifecycle tracking. This phased approach ensures employees adapt easily and IT doesn’t get overwhelmed.
Challenges in Laptop Inventory Policy Implementation
Even well-designed laptop inventory policies can face hurdles when put into practice. The most common challenges include:
- Employee non-compliance: Staff may forget to log laptops, delay reporting lost devices, or skip updates, especially if processes are inconvenient.
- Department silos: Different teams may use separate methods to track laptops, leading to inconsistent or conflicting records.
- Remote and hybrid work: With devices spread across multiple locations, IT has less visibility and fewer opportunities to check laptops physically.
- Limited IT resources: Small IT teams often struggle to enforce policies while also handling daily support requests, leaving gaps in inventory accuracy.
These challenges aren’t impossible to overcome. With the right approach, companies can make policies easier to follow and maintain consistent control.
Best Practices for Effective Laptop Inventory Policy Enforcement
Laptop inventory policies only work if they’re easy to follow and consistently applied. The key is to reduce friction for employees while giving IT the tools to monitor and enforce rules effectively. Here are some proven practices:
- Automate where possible: Manual tracking is prone to errors. A good asset tracking system, combined with barcode scanning or endpoint management tools, ensures records are updated in real time. Automation also makes tasks like software updates and warranty tracking much easier to manage.
- Train employees early: Policies are most effective when they’re introduced from day one. During onboarding, explain how laptops are assigned, what responsibilities employees have, and the process for reporting issues. Clear expectations prevent confusion later.
- Keep processes simple: Complicated steps discourage compliance. For example, scanning a barcode takes seconds, while filling out a form may take minutes and often gets skipped. Simple, quick processes help employees do the right thing without extra effort.
- Schedule regular audits: Even with automation, mistakes happen. Quarterly or semi-annual audits allow IT to confirm laptops are where they should be, records are accurate, and no devices are unaccounted for. Audits also prepare the company for external inspections.
- Set clear accountability: Every laptop should have a named owner or team responsible for it. When responsibility is shared, devices tend to fall through the cracks. Clear ownership ensures someone is always accountable for reporting problems or returning equipment.
- Review policies annually: Work habits, security risks, and technology standards change quickly. A yearly review keeps policies up-to-date, ensures they align with compliance requirements, and adapts them to new challenges like remote or hybrid work.
By combining automation, training, and regular reviews, companies can turn policies into daily habits. This ensures laptops stay secure, records stay accurate, and IT teams stay in control without being buried in manual tasks.
Conclusion
Laptops are vital assets, but without clear policies, they’re easy to lose track of. Strong laptop inventory policies, supported by tools like barcode scanners and a good tracking system, help companies manage devices securely and efficiently.
With the right approach, policies turn into everyday practices that reduce costs, improve accountability, and protect data, ultimately ensuring smooth IT operations and long-term savings.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.

