Computer Hardware Asset Management: Stop Losing Track of Your IT Assets
Computer Hardware Asset Management helps businesses track, manage, and optimize IT assets to prevent loss, reduce costs, and improve security.
Losing track of IT hardware is more common than you think. Laptops disappear, servers sit unused, and devices go missing without anyone noticing until it’s too late. Every untracked asset is money wasted and a security risk waiting to happen.
Imagine an employee leaves without returning their company laptop. No record, no tracking just gone. Now multiply that across an entire business. The cost adds up fast, and so do the risks.
Computer Hardware Asset Management is the key to stopping the chaos, cutting losses, and protecting your IT investments. In this blog, we’ll break down why businesses lose track of IT hardware and how you can take control before it costs you more.
Why Businesses Lose Track of IT Hardware Assets
IT hardware doesn’t disappear on its own, but without a proper tracking system, it might as well. Businesses frequently lose track of devices due to poor visibility, outdated tracking methods, and lack of accountability. The result? Wasted budgets, security risks, and operational inefficiencies that add up over time.
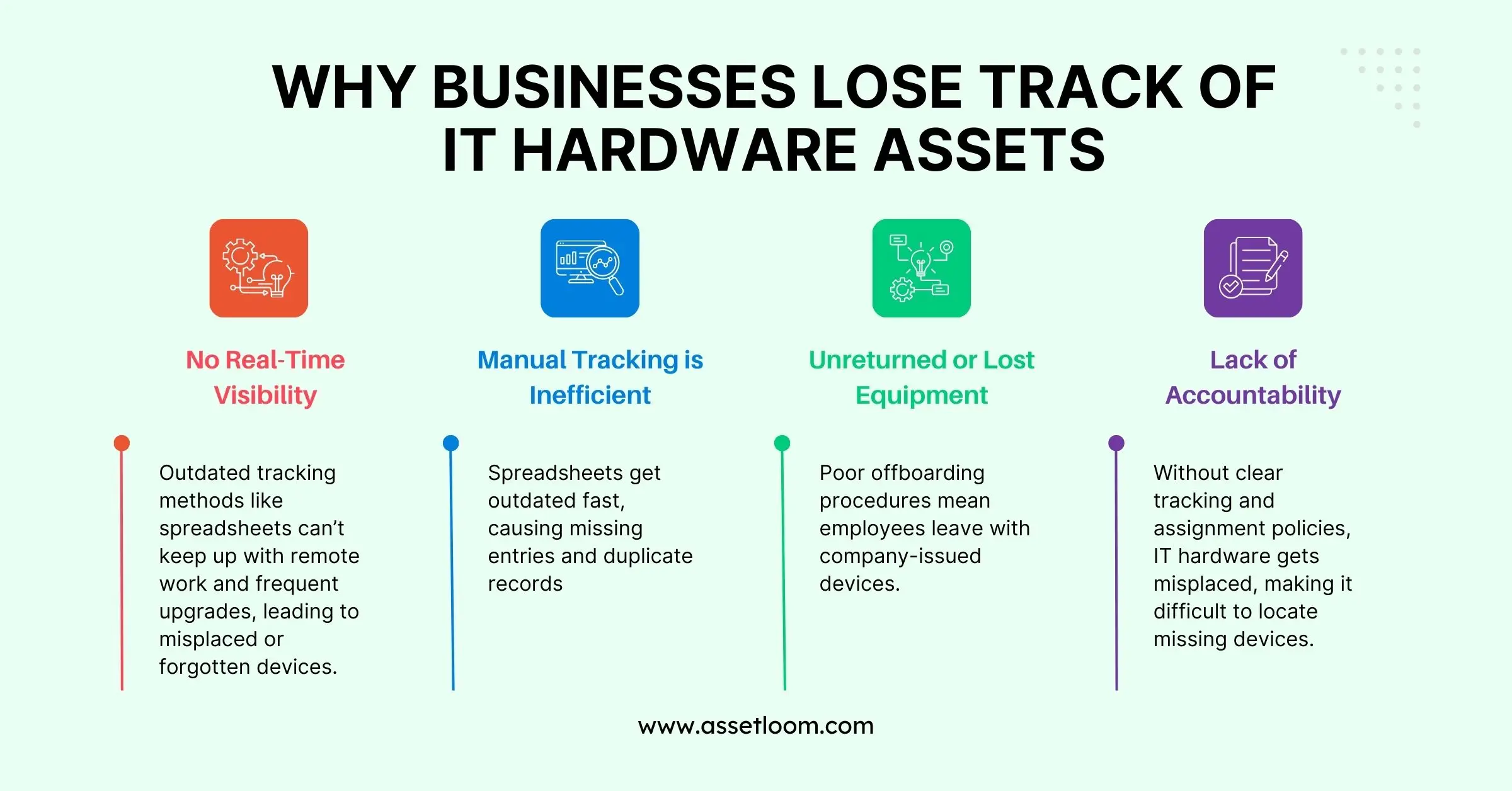
No Real-Time Visibility
Many companies rely on outdated asset management methods, such as spreadsheets or manual logs. These systems can’t keep up with remote work, multiple office locations, and frequent hardware upgrades. Without real-time tracking, devices are easily misplaced, forgotten in storage, or left unaccounted for when employees leave.
Manual Tracking is Inefficient
Managing IT assets manually is prone to errors. Spreadsheets get outdated fast, and human oversight leads to missing entries or duplicate records. According to a study, 43% of small businesses fail to track assets properly, leading to lost or underutilized equipment [ProfileTree]. Without automated systems, businesses struggle to keep up with what hardware they own, where it is, and who is using it.
Unreturned or Lost Equipment
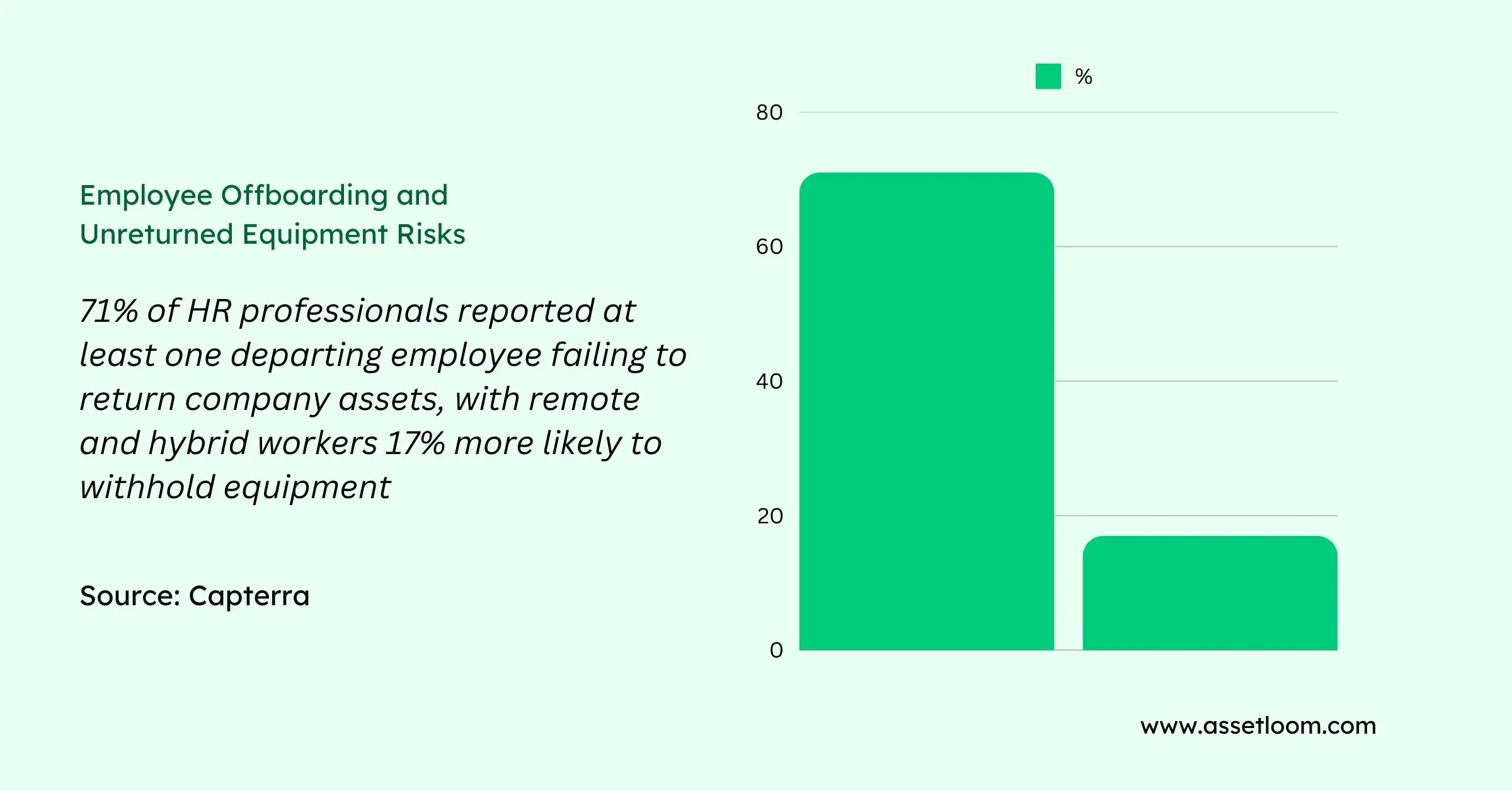
A major reason businesses lose track of hardware is poor offboarding procedures. Employees leave, but their company-issued laptops, tablets, and other devices don’t always make it back. Without strict return policies, companies lose thousands of dollars in missing hardware every year. One survey found that 71% of HR professionals reported at least one departing employee failing to return company equipment Teqtivity.
Lack of Accountability
When no one is held responsible for tracking IT assets, hardware easily gets misplaced. Businesses that don’t enforce proper assignment, tracking, and return policies often find themselves struggling to locate missing devices.
The Impact of Poor Computer Hardware Asset Management
When IT hardware isn’t properly tracked, the consequences extend beyond misplaced devices. Businesses lose money, face security threats, and struggle with inefficiencies that directly affect their bottom line.
1. Financial Losses
Every lost, stolen, or unreturned device is a direct financial hit. Without proper tracking, businesses overspend on unnecessary replacements and duplicate purchases—often without realizing it.
2. Security Risks
Untracked hardware isn’t just a financial burden—it’s a major security risk. Every lost or stolen laptop, hard drive, or server could contain sensitive data, exposing businesses to cyber threats.
Key Risks:
- Data Breaches – A misplaced laptop with no remote security measures could lead to unauthorized access.
- Regulatory Fines – Non-compliance with GDPR, HIPAA, or ISO 27001 due to lost or unsecured hardware.
- Intellectual Property Theft – Stolen company data could end up in the wrong hands, putting competitive advantages at risk.
"60% of businesses that experience a data breach due to lost devices face significant financial losses and reputation damage." – Ponemon Institute
3. Operational Inefficiency
Poor hardware tracking slows down IT teams, leading to delayed troubleshooting, prolonged downtime, and inefficient asset allocation. Without clear records, IT teams waste time locating devices, managing repairs, or updating outdated records manually. Employees also face disruptions when they don’t receive the right hardware on time, affecting overall productivity.
4. Compliance & Legal Risks
Many industries have strict regulations requiring businesses to track, secure, and properly dispose of IT assets. Without a structured asset management system, companies struggle to prove compliance with GDPR, HIPAA, or ISO 27001 standards. Missing audit records or untracked devices can result in fines, failed audits, and reputational damage.
Best Practices for Effective Computer Hardware Asset Management
To stop IT hardware from getting lost, businesses need a structured Hardware Asset Management strategy.
1. Implement a Centralized Asset Tracking System
Tracking IT hardware without a centralized system is like managing finances without a budget—things get lost, records become outdated, and costs pile up fast. A structured Computer Hardware Asset Management system ensures that every device is accounted for, tracked, and managed efficiently.
To track IT hardware effectively, businesses need IT Asset Management (ITAM) software that provides real-time inventory updates. Every device should be tagged with barcodes, QR codes, or RFID labels to ensure accurate tracking. IT teams should also establish clear asset assignment policies, making it easy to track which employee or department is responsible for each device.
Regular updates and audits keep the system accurate. Businesses should monitor asset movement, ensure records are up to date, and automate notifications for hardware nearing replacement or maintenance. Role-based access ensures only authorized users can modify asset records, preventing accidental data loss or tampering.
A centralized asset tracking system eliminates guesswork, prevents IT hardware from going missing, and ensures companies use their assets efficiently. Businesses that invest in a structured tracking process cut costs, improve security, and gain full control over their IT infrastructure.
2. Automate Asset Discovery and Monitoring
Manually tracking IT hardware is time-consuming, prone to errors, and impossible to scale as businesses grow. Automation takes the guesswork out of asset management by ensuring that every device is detected, monitored, and updated in real time.
With IT Asset Management (ITAM) software, businesses can automatically detect and track all network-connected devices. As soon as a new device connects, the system logs it, preventing assets from being overlooked. Real-time monitoring provides up-to-date location, usage, and performance data, helping IT teams identify inactive or aging devices that need reassignment or replacement.
Automated alerts notify IT staff when a device goes offline, moves to a different location, or reaches end-of-life. This prevents unexpected downtime and ensures hardware is replaced before performance declines. AI-driven monitoring can also detect unusual activity or unauthorized access, enhancing security.
Automating asset discovery and monitoring eliminates manual tracking errors, improves security, and optimizes IT hardware usage. Businesses that invest in automation gain full visibility into their assets, reduce losses, and ensure their IT infrastructure runs smoothly.
3. Establish a Clear Asset Lifecycle Process
IT hardware isn’t meant to last forever. Without a structured asset lifecycle process, businesses end up holding onto outdated devices, overspending on replacements, or exposing themselves to security risks. A well-defined lifecycle strategy ensures that every device is tracked from procurement to retirement, optimizing performance and cost efficiency.
Managing IT hardware efficiently means tracking assets through every stage of their IT Asset lifecycle Management. It begins with procurement, where businesses select hardware based on budget, performance needs, and compatibility. Once deployed, assets should be assigned to specific users or departments and recorded in an IT asset management system to ensure accountability.
Regular maintenance and performance monitoring help extend hardware lifespan, while timely upgrades and reassignments ensure that devices remain efficient. As equipment nears the end of its lifecycle, businesses must enforce secure decommissioning practices, including data wiping and responsible recycling, to prevent security risks.
A clear asset lifecycle process helps businesses extend IT hardware lifespan, reduce unnecessary spending, and maintain security. By tracking each stage—from procurement to disposal—companies gain better control over IT hardware, reduce waste, and improve operational efficiency.
4. Enforce IT Security and Device Return Policies
Untracked or unreturned IT hardware isn't just a financial burden—it’s a security risk. When employees leave or devices go missing, sensitive company data can remain on those devices, increasing the chances of breaches, data leaks, or unauthorized access. Enforcing strict security measures and return policies ensures that IT assets remain protected throughout their lifecycle.
To prevent lost devices and security threats, businesses must enforce strict device management policies. Employees should sign hardware responsibility agreements, confirming accountability for company-issued devices. IT teams should implement remote tracking, locking, and wiping features to protect data in case a device is lost or stolen. A structured offboarding process ensures that all IT equipment is collected before an employee’s departure.
Automating return reminders and implementing secure authentication measures also help maintain visibility over active devices. IT teams should conduct periodic security audits to detect unauthorized devices still connected to company systems.
Enforcing IT security and return policies helps businesses prevent asset losses, enhance security, and maintain compliance. With strict device tracking and secure offboarding procedures, companies can protect their IT assets, reduce risks, and prevent unnecessary losses.
5. Conduct Regular Hardware Audits
Tracking IT hardware isn’t a one-time task—it requires ongoing monitoring and verification to ensure accuracy. Without regular audits, businesses risk losing devices, overspending on unnecessary replacements, and failing compliance checks. Conducting scheduled hardware audits helps maintain a complete and accurate inventory while identifying missing, outdated, or underutilized assets.
Regular audits help businesses verify that their asset records match actual inventory. IT teams should compare physical assets with digital records to detect discrepancies. Using barcode or RFID scanning speeds up the process, ensuring accurate updates. Audits should also focus on identifying and removing ghost assets, ensuring that records reflect real, usable hardware.
Establishing a routine audit schedule—whether quarterly or annually—helps businesses stay ahead of asset loss. High-risk devices, such as laptops, mobile devices, and external storage hardware, should be audited more frequently due to their higher likelihood of being misplaced or stolen.
Regular hardware audits help businesses detect and recover missing assets, maintain accurate inventory records, and stay compliant with industry regulations. By making hardware audits a routine process, companies gain greater control over IT assets, reduce waste, and minimize security risks.
How IT Asset Management Software Improves Hardware Tracking
Keeping track of IT hardware manually is slow, error-prone, and hard to scale. IT Asset Management (ITAM) software simplifies the process by automating tracking, improving accuracy, and enhancing security. With the right ITAM system, businesses can see where every device is, who’s using it, and when it needs maintenance or replacement—all in real time.
With an ITAM system in place, companies can automatically detect and track devices, monitor real-time usage, and receive alerts when hardware is lost, underused, or due for upgrades. Instead of manually updating spreadsheets, businesses can use barcodes or RFID tags to scan and instantly update asset records. IT teams gain a complete view of each device’s lifecycle, helping them optimize hardware use, plan upgrades, and securely retire outdated equipment.
A large company struggling with misplaced laptops and high IT costs saw instant improvements after switching to ITAM software. Within a year, they recovered 20% of lost devices, cut IT spending by 30%, and improved compliance with real-time asset tracking.
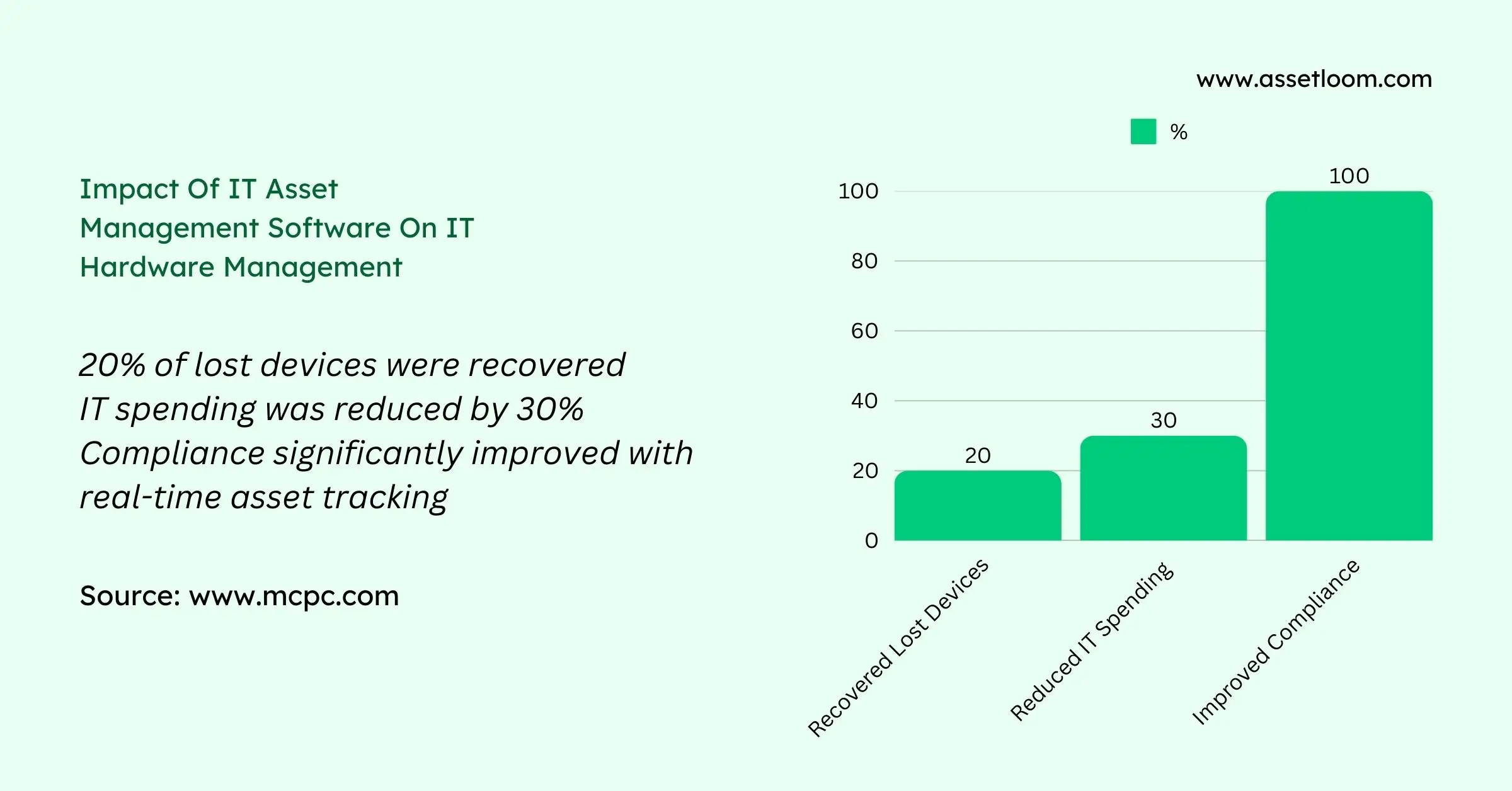
By automating hardware tracking, ITAM software eliminates guesswork, reduces losses, and ensures businesses get the most out of their IT assets. Investing in the right system means better efficiency, lower costs, and stronger security for IT hardware management.
Conclusion
Losing track of IT hardware doesn’t just waste money—it creates security risks, operational slowdowns, and compliance issues. Without a structured approach to Computer Hardware Asset Management, businesses risk overspending on unnecessary replacements, failing audits, and leaving company data vulnerable on lost or unreturned devices.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


