Android Device Management: How to Manage Android Devices
What Android Device Management is, its challenges, key features, and how AssetLoom helps manage Android devices as part of your IT inventory.
Phones and tablets get added, replaced, or passed around, and before long, it’s unclear who has what or if security settings are being followed. Lost devices, forgotten updates, and unmonitored apps can quickly turn into real problems for both employees and IT teams. Many companies try to manage this with spreadsheets or manual lists, but that usually leads to mistakes and missed details. When a device goes missing or an audit comes up, IT is left scrambling to pull the right information.
Good device management isn’t just about keeping gadgets in order—it’s also part of IT Asset Management. By treating Android devices as important assets, businesses can reduce risks, make support easier, and ensure the right tools are always ready for employees.
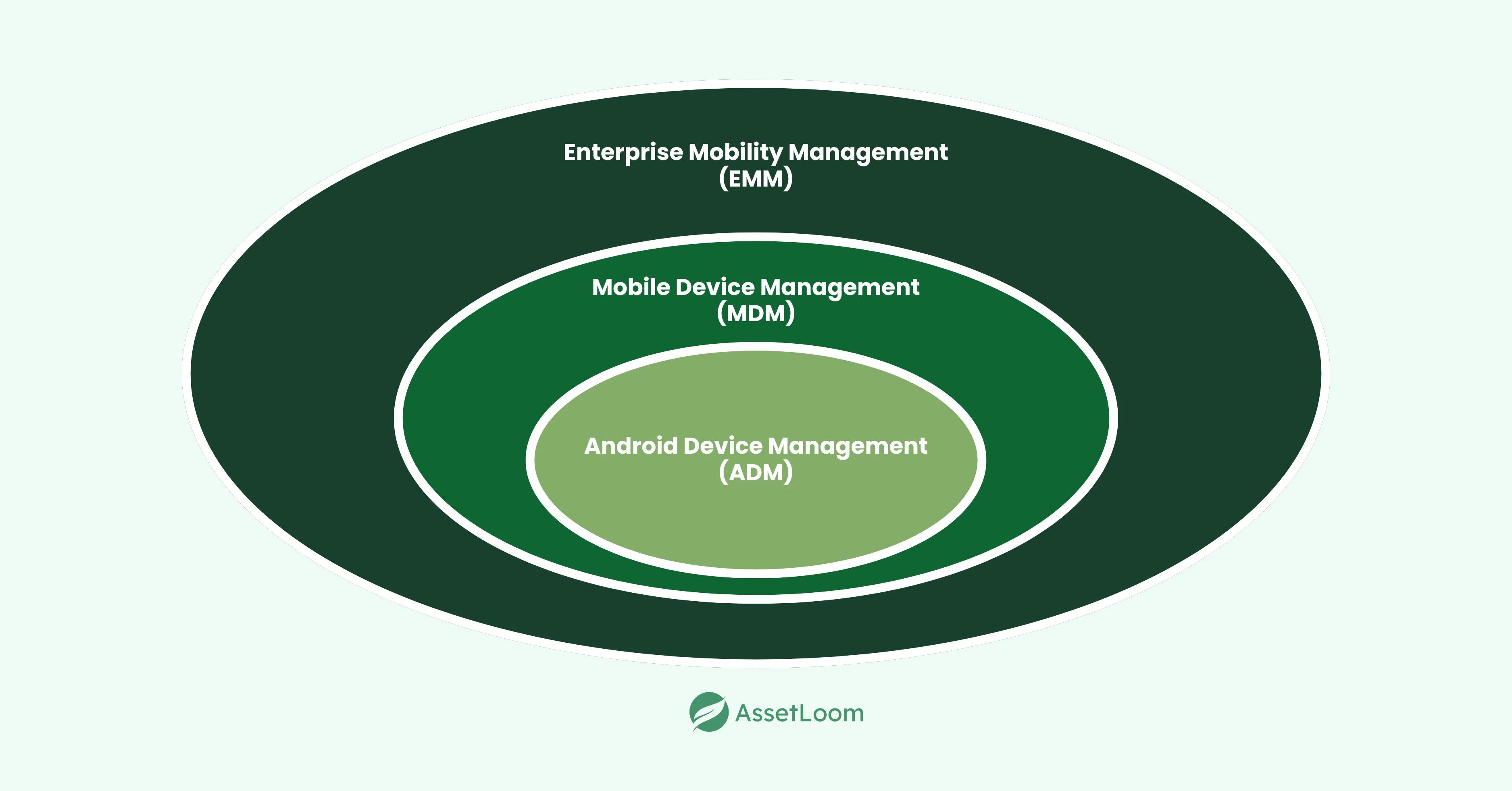
What is Android Device Management?
Android Device Management is the process of controlling and overseeing Android phones and tablets that are used for work. It helps IT teams set rules, protect data, and make sure devices are being used the right way.
Think of it like managing a set of office keys. If everyone has their own key, you need a system to know who has one, make sure they return it, and replace it if it’s lost. Android devices work the same way. They give people access to company data, so there has to be a way to keep track, apply security, and remove access if needed.
With Android Device Management, companies can:
- Set security policies like passwords and screen locks
- Install or block apps across devices
- Push updates to keep systems secure
- Track devices in case they are lost or stolen
- Wipe company data remotely if needed
Instead of handling each device separately, everything can be managed from one place.
What is Mobile Device Management (MDM)?
Mobile Device Management (MDM) is a system that allows companies to control and secure mobile devices like smartphones and tablets from a central place. Instead of IT teams having to configure each device one by one, MDM makes it possible to set rules and apply them to all devices at once.
For example, imagine a company with 200 employees, each using an Android phone for work. Instead of checking every phone manually, MDM lets IT:
- Enforce password and lock screen rules
- Install or update business apps on all devices
- Block apps that shouldn’t be used for work
- Track devices in case they are lost or stolen
- Wipe data remotely if a device goes missing
The main goal of MDM is to keep company data safe while making sure employees can still do their jobs effectively.
What is Enterprise Mobility Management (EMM)?
Enterprise Mobility Management (EMM) is a broader approach to managing mobile devices. While MDM focuses mostly on the devices themselves, EMM looks at the bigger picture—devices, apps, data, and how employees use them for work.
Think of it as the next step after MDM. Instead of just controlling phones and tablets, EMM also manages:
- Applications: deciding which apps can be installed, and pushing business apps to devices
- Content: making sure files and documents are shared securely
- Identity: controlling who can access certain apps or data
- Devices: handling security settings, updates, and remote actions
For example, if an employee needs to access sensitive documents from their phone, EMM ensures not only that the device is secure, but also that the right app is being used and only the right person can log in.
The goal of EMM is to give businesses a safe and flexible way to support mobile work while protecting company data from risks.
Challenges of Managing Android Devices Manually
Managing Android devices by hand may work for a small team, but it quickly runs into limits as the number of devices and users grows. Fragmentation across Android models, operating system versions, and manufacturer customizations makes it difficult to enforce consistent policies or keep devices secure.
Here are the main challenges:
Security and Compliance Challenges
Fragmented Android OS
The wide range of Android manufacturers, models, and customized systems creates an inconsistent environment. This makes it hard to apply uniform security policies or roll out updates on time.
Data Leakage and Unauthorized Access
When devices aren’t monitored in real time, sensitive company data can be at risk—especially if a phone is lost, stolen, or accessed by someone who shouldn’t have it.
Malware and Vulnerabilities
Manual methods often miss updates or patching schedules. This increases the chance of malware infections and security breaches that can lead to compliance violations.
Operational and Scalability Challenges
Inefficient Device Onboarding
Setting up each device for employees one by one is slow and prone to mistakes. This delays productivity and creates extra work for IT teams.
Lack of Device Control
Without centralized management, it’s difficult to limit devices to work-related apps and settings. This often leads to misuse, unauthorized app installs, and lower productivity.
Poor Remote Support
Helping employees with issues remotely is difficult when devices are managed manually. Problems take longer to resolve, leading to downtime and higher support costs.
Scalability Issues
As the number of devices increases, manual tracking quickly becomes unsustainable. Costs rise, and IT teams struggle to keep up.
Lack of Visibility and Monitoring
Inadequate Device Tracking
IT teams often don’t have accurate insights into device location, activity, or inventory. This makes it harder to monitor compliance and respond to incidents quickly.
Difficulty in Monitoring Usage
Keeping an eye on how devices are used, ensuring they remain productive, and spotting early signs of problems is nearly impossible without automated tools.
Key Features of Android Device Management
Android Device Management provides tools that help IT teams control, secure, and monitor devices more efficiently. Instead of handling each phone or tablet manually, everything can be managed from a central platform.
Device Enrollment and Provisioning
Getting new devices ready for employees can take a lot of time if each one has to be set up manually. Android Device Management simplifies this by allowing IT teams to enroll and configure multiple devices at once.
Key points:
- Bulk enrollment: add dozens or even hundreds of devices in a single process.
- Preconfigured profiles: settings, apps, and security policies can be applied automatically during setup.
- Zero-touch enrollment: devices are ready for use as soon as employees turn them on, no extra steps required.
- Consistency: every device follows the same rules, reducing errors and gaps in security.
This approach not only saves time but also ensures that employees receive devices that are secure and work-ready from day one.
Remote Lock, Wipe, and Reset
When a device is lost, stolen, or no longer in use, quick action is needed to protect company data. Android Device Management gives IT teams the ability to secure or reset devices remotely.
Key points:
- Remote lock: instantly lock a device so no one else can use it.
- Data wipe: remove company data if the device is lost or stolen.
- Factory reset: return a device to its original state before reassigning it to another employee.
- Role changes: wipe or reset devices easily when employees leave or move to new positions.
These features help prevent data leaks and ensure devices can be reused safely.
Application Management
Managing apps across multiple Android devices can be challenging if done manually. Android Device Management makes it easier to distribute, update, and control applications from a central platform.
Key points:
- Centralized app installation: deploy business apps to all devices at once.
- Automatic updates: keep apps up to date without relying on employees to do it.
- App restrictions: block unauthorized or risky apps that could harm security or productivity.
- Preconfigured settings: push app configurations so employees can start using them immediately.
This ensures that employees have the right tools while reducing the risk of unapproved apps creating security gaps.
Policy Enforcement and Compliance
Consistent security policies are critical when managing a large number of Android devices. Android Device Management makes it possible to apply and enforce rules across all devices, ensuring compliance and reducing risks.
Key points:
- Password policies: require strong passwords, PINs, or biometric authentication.
- Encryption enforcement: make sure data stored on devices is encrypted.
- Compliance checks: monitor devices to confirm they meet company and industry standards.
- Automatic enforcement: apply rules instantly across all devices instead of relying on manual updates.
With these controls, IT teams can maintain a secure environment and reduce the chance of overlooked vulnerabilities.
Location Tracking and Monitoring
Knowing where devices are and how they are being used helps IT teams protect company assets and respond quickly to problems. Android Device Management provides tools for real-time tracking and monitoring.
Key points:
- Device location: track devices to recover lost or stolen equipment.
- Usage monitoring: see how devices are being used and detect unusual activity.
- Compliance alerts: get notified when a device falls out of compliance with security policies.
- Geofencing: set boundaries so devices can only be used in approved locations.
These features give IT teams better visibility and help reduce risks tied to lost devices or unauthorized use.
Reporting and Analytics
Managing devices effectively requires more than just controls—it also needs insights. Android Device Management provides reporting and analytics tools to help IT teams understand device usage and make better decisions.
Key points:
- Compliance reports: check which devices meet security requirements and which do not.
- Device health: monitor battery status, storage, and overall performance.
- App usage: see which apps are being used, underused, or need updates.
- Inventory insights: identify inactive or underutilized devices to reduce costs.
These insights give IT teams the information they need to improve planning, catch risks early, and optimize resources.
How AssetLoom Can Help Manage Android Devices
Android devices are part of a company’s wider IT inventory, alongside laptops, desktops, servers, and software licenses. Tracking them separately or with manual tools often leads to gaps, devices get lost, policies aren’t followed, and IT teams waste time chasing information.
AssetLoom, as IT Asset Management software, is designed to centralize IT inventory management. Android devices become part of the same system used to manage all IT assets, giving IT teams complete visibility and control.
With AssetLoom, companies can:
- Keep an accurate inventory: know exactly how many Android devices exist, who is using them, and where they are.
- Simplify onboarding: bulk enrollment and zero-touch setup make new devices ready faster.
- Apply security consistently: enforce password rules, app restrictions, and encryption across all devices.
- Use insights to plan: run reports to identify unused or underutilized devices, avoid over-purchasing, and optimize budgets.
By managing Android devices as part of the overall IT inventory, AssetLoom reduces risks, cuts down manual work, and ensures every device is accounted for throughout its lifecycle.
Conclusion
Android devices are now a core part of every company’s IT inventory. If they aren’t managed properly, they can lead to security risks, compliance issues, and wasted costs.
Android Device Management provides the tools to keep them secure and productive. With AssetLoom, these devices are managed alongside all other IT assets, giving IT teams one place to track, control, and optimize their inventory.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


