7 Common Mistakes When Using an IT Asset Management System
Avoid costly errors with your IT Asset Management System! Discover the 7 most common mistakes businesses make and learn how to fix them for better efficiency, security, and cost savings.
An IT Asset Management System (ITAM) helps businesses track, manage, and organize their IT assets like hardware, software, and cloud services. It keeps everything in one place, making it easier to control costs, improve security, and ensure assets are being used efficiently.
But, many companies struggle to use their ITAM system correctly. Common mistakes can lead to wasted money, security risks, compliance issues, and poor productivity. The good news is that these mistakes are avoidable.
Here are 7 mistakes businesses often make with their IT Asset Management System and simple ways to fix them.

1. Not Keeping IT Asset Records Up to Date
Keeping IT asset records updated is essential for smooth operations, cost savings, and security. Yet, many businesses fail to maintain accurate data, leading to lost equipment, duplicate purchases, compliance risks, and inefficient resource allocation.
Why This Is a Problem
Lost or Unaccounted Assets
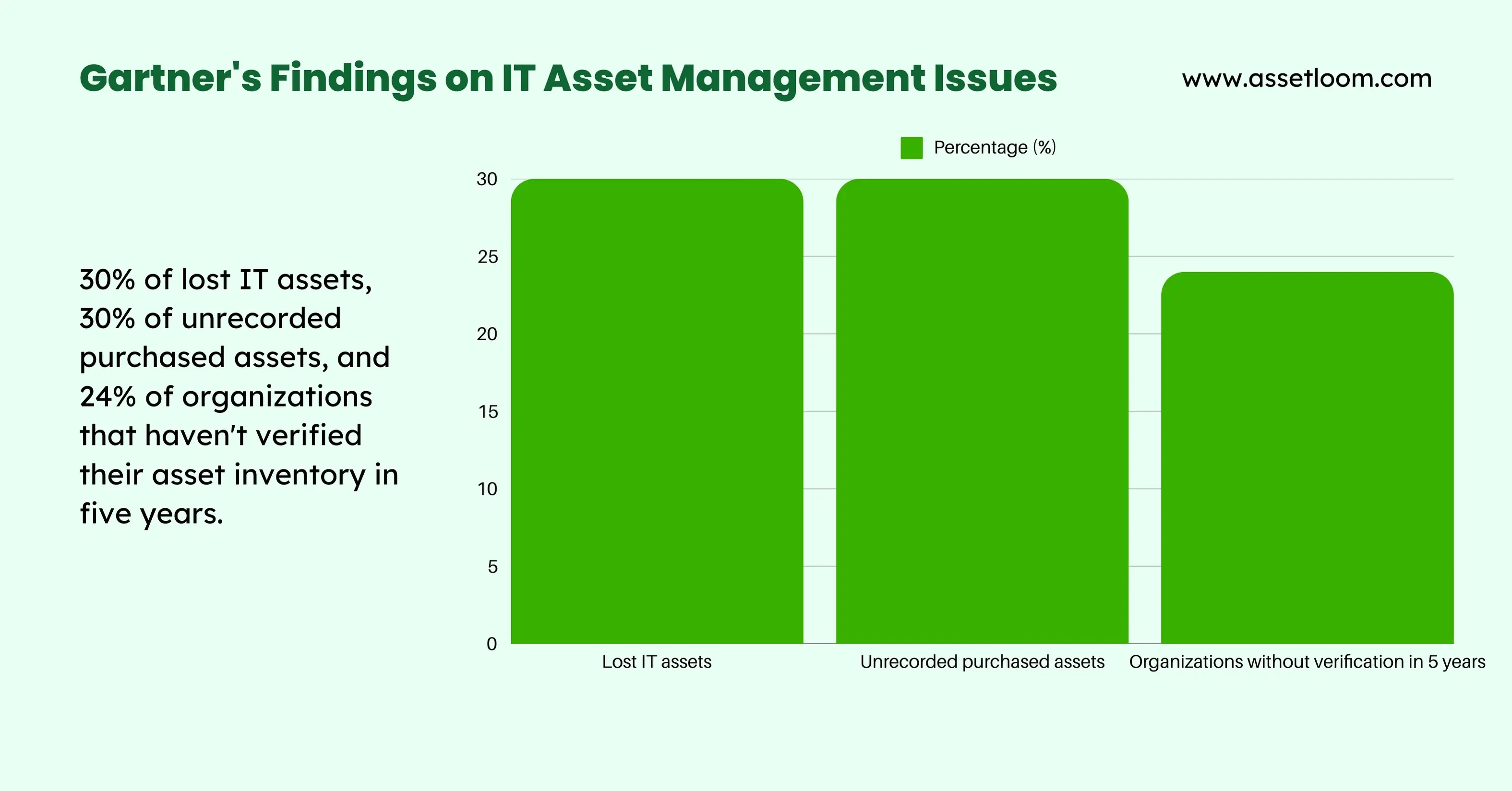
When IT asset records are outdated, businesses lose track of equipment, making it difficult to determine who is using which devices or where they are located. This issue is particularly common in remote work environments, where employees use company-issued laptops and mobile devices. 30% of IT assets go missing due to poor tracking, leading to financial and operational losses. Retire-IT
Wasted Budget on Unnecessary Purchases
If asset records are inaccurate, IT teams might unintentionally purchase hardware or software they already own but fail to utilize properly. 38% of IT spending is wasted due to underutilized or duplicate purchases. Flexera State of ITAM
Companies can save thousands of dollars annually by maintaining a centralized, real-time IT asset inventory.
Compliance and Security Risks
Industry regulations such as ISO 27001, GDPR, HIPAA, and SOX require businesses to keep accurate IT asset records. Failure to do so can result in:
- Fines and legal penalties for non-compliance.
- Data breaches from untracked devices containing sensitive information.
- Operational downtime when expired or unsupported software isn’t properly managed.
Businesses that fail to maintain proper asset tracking risk non-compliance penalties ranging from $50,000 to millions of dollars. (GDPR EU)
Difficulty During IT Audits
Without updated records, IT teams struggle during internal or external audits. If an auditor asks for proof of compliance, but there’s no clear documentation of who has access to which assets, it can result in compliance failures or lost productivity.
88% of organizations struggle with IT audits due to missing or outdated asset records. (IAITAM)
How to Fix It
To prevent lost assets, unnecessary expenses, and compliance risks, businesses must ensure their IT asset records are always up to date. Here are the best strategies to fix this issue:
Use an Automated IT Asset Management System
Manual tracking using spreadsheets or outdated systems leads to errors and missing records. Implementing an IT Asset Management System (ITAM) ensures real-time updates and accurate tracking of all assets.
Recommended ITAM tools:
- AssetLoom – Provides cloud-based IT asset tracking with mobile access.
- ServiceNow IT Asset Management – Offers automation, lifecycle tracking, and real-time reporting.
- Lansweeper – Ideal for discovering and tracking assets across a network.
Tip: Choose an ITAM system with barcode or RFID scanning for easy tracking of hardware assets.
Schedule Regular IT Asset Audits
Even with automation, it’s important to verify asset records manually through scheduled audits. Audits help identify:
- Missing or misplaced devices
- Underutilized or duplicate assets
- Security vulnerabilities in outdated hardware or software
Best practice: Audit at least 10-20% of IT assets every quarter to keep records accurate. (IAITAM)
Assign Ownership for Every IT Asset
Every asset should have a designated owner or department responsible for keeping records updated. This ensures accountability and prevents assets from going missing.
How to implement it:
- Use asset tagging systems to track ownership.
- Require employees to sign off on IT equipment assigned to them.
- Set role-based permissions in ITAM software to prevent unauthorized changes.
Set Alerts for Maintenance and Updates
Many businesses forget to update records when assets are repaired, replaced, or disposed of. ITAM tools allow businesses to set automated reminders for: Maintenance schedules (to avoid asset failure) License renewals (to prevent compliance issues) End-of-life replacements (to prevent security risks from outdated hardware)
Example: TechTarget suggests setting alerts 30-60 days before an asset's renewal or maintenance deadline.
Integrate IT Asset Management with Other IT Systems
To ensure seamless tracking, businesses should integrate ITAM with: IT Service Management (ITSM) tools (e.g., ServiceNow ITSM) Cybersecurity tools to monitor asset vulnerabilities Finance tools to track asset costs and depreciation
Why this helps: It eliminates data silos, ensuring all teams have access to real-time IT asset information.
2. Ignoring Software License Management
Software plays a vital role in business operations, but many companies fail to track and manage their licenses properly. This can lead to unnecessary expenses, security risks, and legal penalties. Poor license management often results in paying for unused software, non-compliance with vendor agreements, and exposure to cybersecurity threats.
Why This Is a Problem
Paying for Unused or Extra Licenses
Many businesses spend money on software that isn’t fully used. Some continue to renew licenses for outdated applications, while others purchase more licenses than needed to avoid shortages. Without a clear system in place, it becomes difficult to track usage, leading to wasteful spending.
Non-Compliance with Software Agreements
Software vendors regularly audit companies to ensure compliance with licensing agreements. If a business is using more licenses than purchased, they may face costly fines. On the other hand, failure to renew or maintain licenses properly can also lead to legal trouble. Without a structured process for tracking licenses, companies risk unexpected compliance issues.
Security and Operational Risks
Expired or unmonitored software creates serious security threats. Unsupported software no longer receives security updates, making it a target for hackers. Cybercriminals often exploit outdated applications to steal sensitive business data.
Unmanaged licenses can also cause software conflicts. Employees may use different versions of the same software, leading to workflow disruptions and compatibility issues. This slows down productivity and creates unnecessary IT problems.
How to Fix It
Use a Software Asset Management (SAM) System
A Software Asset Management (SAM) system helps businesses track all software licenses, monitor usage, and ensure compliance. This reduces the risk of overspending, unauthorized software use, and non-compliance fines.
Conduct Regular Software Audits
Running quarterly or annual software audits helps businesses:
- Identify unused or duplicate software to reduce costs.
- Ensure that license usage matches purchases.
- Keep track of upcoming renewals to prevent interruptions.
By reviewing software usage regularly, businesses can eliminate waste and improve IT efficiency.
Remove Unused Licenses
Many employees have access to software they no longer need. IT teams should monitor usage and revoke licenses from inactive users. This frees up available licenses for employees who actually need them, reducing unnecessary purchases.
A simple policy can be to deactivate licenses for users who haven’t used an application in the last six months. This prevents software from sitting unused while still being paid for.
Set Automatic Renewal Alerts
One common mistake is forgetting to renew software licenses on time. When an important application suddenly stops working, it can disrupt business operations.
To prevent this, IT teams should set automatic reminders 30 to 60 days before expiration. This allows time to review the renewal, approve payments, or cancel unnecessary licenses.
Control Software Access to Prevent Shadow IT
Employees often download and install software without IT approval, which can lead to security risks and compliance violations. This is known as shadow IT and can cause serious problems for businesses.
To prevent this:
- Restrict administrative privileges so only authorized users can install software.
- Create a software request system where employees can submit requests for needed applications.
- Regularly scan devices for unauthorized software and remove unapproved installations.
3. Failing to Automate IT Asset Tracking
Many businesses still rely on spreadsheets or manual tracking to manage their IT assets. This outdated approach often leads to errors, lost equipment, unnecessary purchases, and security risks. Automating IT asset tracking helps businesses keep accurate records, improve efficiency, and reduce costs.
Why This Is a Problem
Lost or Misplaced Assets
Without automation, tracking IT assets manually makes it easy for devices to go missing. Employees may move laptops, printers, or mobile devices between departments without updating records. Over time, businesses lose track of who has what, leading to misplaced or unaccounted assets.
When assets are lost, companies may spend thousands of dollars replacing equipment that already exists but cannot be located.
Time-Consuming and Prone to Human Error
Manual tracking relies on employees updating spreadsheets, which is time-consuming and prone to mistakes. Data entry errors, forgotten updates, and missing details create unreliable records.
Without automation, IT teams must conduct lengthy physical audits to verify inventory, taking valuable time away from other essential tasks.
Wasted IT Budget on Unnecessary Purchases
When asset records are outdated or inaccurate, businesses may purchase new equipment unnecessarily. If an employee needs a new laptop, but there’s an unused one available, outdated records may not show it. This leads to duplicate purchases and higher IT costs.
Security and Compliance Risks
Untracked devices pose security threats, especially if they store sensitive company data. Lost or stolen assets that are not properly recorded increase the risk of data breaches.
Additionally, businesses in regulated industries must maintain an accurate asset inventory for compliance with standards like ISO 27001, HIPAA, and GDPR. Without automation, proving compliance becomes difficult and may result in penalties.
How to Fix It
Use an IT Asset Management (ITAM) System
An IT Asset Management (ITAM) system automates asset tracking by maintaining real-time records of all hardware and software assets. These systems can:
- Automatically update asset locations and ownership when assigned to employees.
- Track the entire asset lifecycle from procurement to retirement.
- Send alerts for maintenance, renewals, and replacements.
Automating IT asset tracking ensures that businesses always know where their assets are and how they are being used.
Implement Barcode, RFID, or GPS Tracking
Manual tracking methods are unreliable, but businesses can automate asset tracking using barcodes, RFID tags, or GPS. These technologies help IT teams:
- Scan and update asset details instantly using barcode readers.
- Track equipment movement within offices using RFID tags.
- Monitor remote and field assets using GPS tracking.
By tagging each IT asset, businesses can quickly locate devices, update records automatically, and reduce the chances of lost or stolen equipment.
Integrate IT Asset Tracking with Other Systems
For better efficiency, businesses should connect IT asset tracking tools with other IT systems like:
- IT Service Management (ITSM) – Helps IT teams quickly find assets linked to support tickets.
- Cybersecurity Systems – Ensures unregistered devices do not access sensitive company networks.
- Finance and Procurement Tools – Provides accurate cost tracking and budgeting for IT purchases.
Integration ensures seamless data sharing, making IT asset tracking part of a larger, more efficient IT management strategy.
Set Up Automated Alerts and Maintenance Reminders
Automated systems can send notifications when assets require updates, repairs, or replacements. This prevents downtime and ensures hardware is always in working condition.
For example:
- Aging laptops can be flagged for replacement before they fail.
- License renewals can be scheduled in advance to avoid software expiration.
- Inactive devices can be flagged for reassignment to reduce unnecessary spending.
4. Overlooking Security and Access Controls
IT assets hold sensitive company data, making them a prime target for cyber threats. Many businesses fail to implement proper security and access controls, leaving their IT infrastructure vulnerable to data breaches, insider threats, and compliance violations.
Why This Is a Problem
Unauthorized Access to IT Assets
Without strict access control policies, employees, third parties, or even former staff may still have access to IT systems and sensitive data. This can lead to:
- Data leaks from former employees who were not properly offboarded.
- Accidental or intentional data theft by unauthorized users.
- Increased risk of malware or ransomware attacks from unprotected devices.
Unrestricted access increases the chances of security breaches, making it difficult to track who is responsible when an incident occurs.
Lack of Encryption and Endpoint Security
Many businesses fail to encrypt sensitive data on their IT assets. Laptops, external drives, and mobile devices often contain confidential company data but lack encryption, making them easy targets for hackers.
Devices without endpoint security solutions are also vulnerable to cyber threats. If antivirus, firewall, and threat detection systems are not enforced across all IT assets, businesses risk exposing their networks to cyberattacks.
Weak or Shared Passwords
Employees often reuse passwords across multiple accounts or share login credentials with colleagues. This makes it easier for hackers to gain access to critical IT systems using stolen or guessed passwords.
Without proper security policies, businesses also fail to:
- Enforce multi-factor authentication (MFA) for sensitive systems.
- Regularly update passwords to prevent unauthorized access.
- Limit administrative privileges to only those who need them.
Failure to Comply with Security Regulations
Regulations such as ISO 27001, HIPAA, and GDPR require businesses to secure their IT assets and control access to sensitive data. Without a strong security framework, organizations risk fines, legal penalties, and reputational damage.
How to Fix It
Implement Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) ensures that employees only have access to the systems and data they need for their jobs. IT teams should:
- Assign access levels based on job roles to limit exposure to sensitive information.
- Regularly review and update access permissions as employees change roles or leave the company.
- Restrict administrative privileges to IT staff only.
By using RBAC, businesses reduce the risk of unauthorized access and insider threats.
Enforce Multi-Factor Authentication (MFA) and Strong Passwords
To strengthen security, businesses should require employees to use multi-factor authentication (MFA) when accessing critical systems. This adds an extra layer of protection, making it harder for hackers to breach accounts even if passwords are compromised.
Other best practices include:
- Requiring complex passwords that include numbers, symbols, and uppercase/lowercase letters.
- Setting automatic password expiration policies to force regular updates.
- Using password managers to generate and store secure passwords.
Encrypt IT Assets and Use Endpoint Security
Businesses should encrypt sensitive data stored on:
- Laptops, desktops, and mobile devices
- External drives and USB storage
- Cloud storage and backup servers
Encryption ensures that even if a device is lost or stolen, data remains protected from unauthorized access.
Additionally, IT teams should install endpoint security software to:
- Detect and block malware, ransomware, and phishing attacks.
- Prevent unauthorized software installations.
- Monitor and log all access attempts to sensitive data.
Automate Security Policies with IT Asset Management (ITAM) Systems
Many IT Asset Management (ITAM) systems come with built-in security features that help enforce policies. Businesses should integrate ITAM with:
- Identity and Access Management (IAM) solutions to automate user provisioning and deactivation.
- Security Information and Event Management (SIEM) systems to monitor access logs and detect suspicious behavior.
- Remote device management tools to wipe data from lost or stolen devices.
Conduct Regular Security Audits and Compliance Checks
Security policies should be reviewed regularly to ensure they align with industry best practices and regulatory requirements. Businesses should:
- Perform quarterly access control reviews to remove inactive users.
- Conduct penetration testing and vulnerability assessments to identify weak points.
- Train employees on cybersecurity best practices to prevent phishing and social engineering attacks.
5. Not Having a Defined IT Asset Lifecycle Strategy
One of the biggest mistakes when using an IT Asset Management System is failing to establish a clear IT asset lifecycle strategy. Many businesses track assets when they are purchased but lack a structured plan for managing them throughout their entire lifecycle.
Why This Is a Problem
Uncontrolled IT Spending
Without a well-defined asset lifecycle strategy, businesses overspend on IT equipment. Assets may be replaced too soon, even when they are still functional, or too late, leading to emergency purchases and downtime.
Increased Downtime and Maintenance Costs
When assets are not tracked for performance and maintenance, businesses react to failures instead of preventing them. Unplanned downtime can disrupt operations, while last-minute repairs add unexpected costs.
Security and Compliance Risks
Outdated hardware and software pose security threats if they are not replaced or decommissioned at the right time. End-of-life (EOL) assets that no longer receive updates can become entry points for cyberattacks.
Additionally, regulations like GDPR, HIPAA, and ISO 27001 require proper asset disposal to prevent data breaches. Businesses without a structured disposal process risk compliance violations and financial penalties.
Poor Asset Tracking and Visibility
IT teams often struggle to track:
- Which assets are active, outdated, or in need of upgrades.
- Who is responsible for each asset.
- When assets should be replaced or retired.
Without a structured lifecycle strategy, businesses lose control over their IT infrastructure, leading to inefficiencies and unnecessary costs.
How to Fix It
Define the IT Asset Lifecycle Stages
A well-structured IT asset lifecycle should include:
- Procurement – Purchase assets based on business needs.
- Deployment – Assign assets to employees and ensure proper setup.
- Usage & Maintenance – Track asset health, schedule updates, and perform routine maintenance.
- Upgrade or Redeployment – Repurpose or upgrade assets to extend their lifespan.
- Retirement & Disposal – Securely decommission outdated assets and ensure proper data wiping.
Defining clear lifecycle stages allows businesses to maximize asset value and reduce security risks.
Use an IT Asset Management (ITAM) System for Tracking
A modern IT Asset Management System helps track IT assets through every stage of their lifecycle. Businesses should:
- Monitor asset age, condition, and usage.
- Set alerts for maintenance, upgrades, and replacements.
- Automate asset retirement and disposal workflows.
With proper lifecycle tracking, IT teams can plan purchases better, avoid unnecessary spending, and prevent unexpected failures.
Implement Scheduled Maintenance and Upgrades
Regular hardware and software maintenance extends the lifespan of IT assets and reduces downtime. Businesses should:
- Schedule firmware updates, battery replacements, and hardware inspections.
- Identify and upgrade aging devices before they become a liability.
- Ensure security patches are applied regularly to minimize cyber risks.
A proactive maintenance plan prevents expensive emergency repairs and keeps IT operations running smoothly.
Develop a Secure IT Asset Disposal Policy
Businesses must securely retire IT assets to prevent security and compliance risks. A structured disposal process should include:
- Secure data wiping before reselling, recycling, or donating assets.
- Proper disposal documentation for audit and compliance records.
- Environmental responsibility through e-waste recycling initiatives.
By following best practices for asset disposal, businesses protect sensitive data, stay compliant, and reduce environmental impact.
Use Data Analytics for Smarter IT Planning
Analyzing asset performance and usage trends helps businesses plan IT budgets and optimize asset purchases. Companies should:
- Track frequent failures and underutilized devices.
- Forecast future IT needs based on asset usage data.
- Identify cost-saving opportunities by repurposing assets instead of buying new ones.
With data-driven asset planning, businesses can reduce IT costs and ensure smarter decision-making.
6. Neglecting Integration with Other IT Systems
A common mistake when using an IT Asset Management System is failing to integrate it with other IT tools and platforms. When ITAM operates in isolation, businesses miss out on automation, data accuracy, and operational efficiency.
Why This Is a Problem
Data Silos and Inaccurate Information
When IT asset data is scattered across different systems, IT teams lack a single source of truth. Asset records become outdated, incomplete, or inconsistent, making it difficult to track hardware, software, and licensing details.
Disconnected systems lead to:
- Duplicate data entries, increasing human errors.
- Misalignment between asset records and actual IT usage.
- Inability to quickly access accurate asset information.
Without integration, ITAM fails to provide real-time insights, leading to poor asset planning and inefficiencies.
Limited Automation and Increased Workload
A stand-alone ITAM system forces IT teams to perform manual updates, increasing workload and reducing productivity. For example:
- Manually updating asset records when employees receive new equipment.
- Tracking software usage separately, rather than syncing with software asset management (SAM) tools.
- Re-entering data for financial reporting, causing inefficiencies and delays.
Without automation, IT teams spend more time on administrative tasks instead of focusing on strategic IT initiatives.
Security and Compliance Risks
Neglecting integration makes it difficult to enforce security policies and meet compliance standards. If ITAM is not connected to security tools:
- Unmonitored devices can access company networks, increasing cyber risks.
- Unauthorized software installations go undetected, leading to compliance violations.
- IT teams cannot track missing or stolen devices, posing data breach risks.
Without integration, businesses struggle to enforce IT policies, increasing the risk of security incidents and non-compliance penalties.
Inefficient IT Support and Incident Management
When ITAM is disconnected from IT Service Management (ITSM) tools, IT teams lack visibility into asset-related issues.
- Helpdesk teams waste time tracking down asset details before resolving support tickets.
- IT staff may deploy the wrong fixes, leading to longer resolution times.
- Businesses fail to optimize asset performance, causing unnecessary downtime.
An integrated system ensures faster troubleshooting, better asset utilization, and improved IT support.
How to Fix It
Integrate ITAM with IT Service Management (ITSM)
Connecting IT Asset Management with ITSM platforms like ServiceNow, Jira Service Management, or Freshservice allows IT teams to:
- Track asset-related incidents and resolve issues faster.
- Automatically update asset records when support tickets are processed.
- Improve IT support workflows, ensuring quick access to asset data.
Integration ensures faster ticket resolution, better visibility into asset health, and improved user experience.
Sync ITAM with Software Asset Management (SAM) Tools
By integrating ITAM with SAM platforms, businesses can:
- Track software usage in real-time, preventing overspending on unused licenses.
- Automate compliance reporting, reducing the risk of audits and fines.
- Ensure software updates and patches are applied, improving cybersecurity.
This integration ensures that hardware and software assets are managed together, improving efficiency and cost control.
Connect ITAM with Endpoint Security and Compliance Tools
IT assets should be integrated with security platforms like Microsoft Intune, CrowdStrike, or SentinelOne to:
- Track devices that access company networks, preventing unauthorized use.
- Enforce encryption, antivirus, and firewall policies to enhance security.
- Remotely wipe lost or stolen devices to protect sensitive data.
A security-integrated ITAM system reduces risks, improves compliance, and ensures all assets are protected.
Automate Financial Reporting by Integrating ITAM with ERP Systems
IT assets impact financial planning, budgeting, and procurement. Businesses should connect ITAM with Enterprise Resource Planning (ERP) tools like SAP, Oracle, or NetSuite to:
- Track asset depreciation and costs for accurate financial reporting.
- Streamline IT procurement processes, reducing delays and errors.
- Ensure IT investments align with business goals, improving decision-making.
This integration eliminates manual financial data entry and helps businesses plan IT budgets more effectively.
Use a Centralized IT Management Platform
Instead of managing separate integrations, businesses can adopt an IT management platform that combines ITAM, ITSM, security, and financial reporting. This creates a unified system where all IT data is connected and accessible in one place.
Platforms like ServiceNow, Ivanti, and ManageEngine provide end-to-end IT management, ensuring ITAM is seamlessly connected to all critical business functions.
7. Skipping Regular IT Asset Audits
T assets constantly change—new devices are added, old ones are retired, and software licenses are updated. Without audits, businesses lose track of their assets, increase security risks, and struggle with compliance.
Why This Is a Problem
Inaccurate Asset Records
IT asset databases become outdated over time. Employees may receive new laptops, servers may be decommissioned, and software licenses may expire—all without being properly updated in the system.
Without audits, businesses struggle to maintain an accurate asset inventory, leading to:
- Lost or untracked devices that continue to incur costs.
- Duplicate or unnecessary purchases due to incomplete records.
- Licensing issues, where software is either overused (risking fines) or underused (wasting money).
Increased Security Risks
Unmonitored IT assets pose serious security threats. Outdated devices, unpatched software, and unauthorized installations create vulnerabilities that hackers can exploit.
Skipping audits allows:
- Former employees to retain access to company assets, increasing data breach risks.
- Unsupported software to remain active, exposing the network to cyber threats.
- Lost or stolen devices to go unnoticed, leading to potential data leaks.
Compliance Failures and Financial Penalties
Regulatory frameworks like GDPR, HIPAA, and ISO 27001 require businesses to maintain an up-to-date IT asset inventory. If an audit finds missing records or mismanaged assets, companies risk fines and legal consequences.
Non-compliance can result in:
- Hefty financial penalties for failing to track and protect IT assets.
- Loss of certifications required to operate in certain industries.
- Damaged business reputation due to poor IT governance.
Wasted IT Budget and Unnecessary Expenses
Without regular audits, businesses often fail to retire or repurpose underutilized assets. This leads to:
- Spending on new devices when existing ones could be reassigned.
- Paying for unused software licenses that could be canceled.
- Failing to track warranty or service contracts, resulting in missed cost-saving opportunities.
Skipping audits directly impacts the bottom line, leading to unnecessary IT expenditures.
How to Fix It
Schedule Routine IT Asset Audits
Businesses should set a fixed schedule for IT asset audits—quarterly, biannually, or annually, depending on company size and industry requirements.
Regular audits help:
- Verify asset locations and conditions.
- Ensure all devices comply with security policies.
- Check for underutilized assets that can be reassigned.
Use IT Asset Management (ITAM) Software for Automated Audits
A modern IT Asset Management System (ITAM) simplifies audits by automating asset tracking and generating real-time reports. ITAM tools:
- Detect all hardware and software assets in the network, reducing manual work.
- Generate compliance reports, making it easier to meet regulatory standards.
- Highlight missing, outdated, or inactive assets, ensuring accuracy.
Automation removes human error, speeds up audits, and keeps records up to date.
Cross-Check Physical and Digital Inventory
Audits should not rely solely on digital records. IT teams must physically verify:
- Hardware assets, ensuring they are present and assigned correctly.
- Software installations, ensuring compliance with licensing agreements.
- Security settings, ensuring encryption, access controls, and updates are enforced.
A combination of digital tracking and physical validation ensures accurate and complete asset records.
Establish Clear Audit Policies and Responsibilities
To ensure consistency, businesses should create standardized audit procedures, including:
- Who is responsible for audits (IT teams, finance, compliance officers).
- What data needs to be collected (serial numbers, user assignments, license usage).
- How frequently audits should be conducted.
A clear audit framework ensures accountability and makes audits a regular business practice.
Use AI and Analytics for Proactive IT Audits
Advanced ITAM systems leverage AI-driven analytics to predict risks and optimize audits. Businesses can use:
- Machine learning models to identify patterns in asset failures.
- Predictive analytics to flag devices approaching end-of-life.
- Automated alerts to notify IT teams of compliance gaps.
AI-enhanced audits reduce manual effort and improve decision-making.
Conclusion
An IT Asset Management System is a powerful tool for managing IT assets efficiently, but common mistakes can reduce its effectiveness. Failing to track assets, neglecting security, skipping audits, and not integrating ITAM with other systems can lead to higher costs, security risks, and compliance failures.
AssetLoom is Now on GoodFirm !
We’re excited to share that AssetLoom is listed on GoodFirms as a trusted IT asset management solution. Check us out on GoodFirms to learn more!

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


