IT Hardware Asset Management Best Practices for Lifecycle Tracking
IT Hardware Asset Management Best Practices for Lifecycle Tracking help you optimize asset discovery, automate updates, monitor performance, and integrate with ITSM workflows to boost efficiency and control costs across your IT infrastructure.
IT hardware asset management best practices help teams take control of devices from the moment they're planned to the time they're retired. Laptops, desktops, servers, and other equipment often get overlooked once deployed. Over time, this leads to unused hardware, outdated systems, and unexpected costs.
Tracking the full lifecycle of hardware keeps things organized. It gives IT teams better visibility into what they own, how it’s used, when it needs maintenance, and when it’s time to replace it.
This blog covers how hardware asset management fits into the larger IT asset picture, outlines the five key stages of the hardware lifecycle, and breaks down the steps for managing assets effectively. It also includes best practices, how to choose the right software, and three tools worth considering.
How HAM Relates to ITAM?
IT hardware asset management (HAM) is one part of a larger framework known as IT asset management (ITAM). While HAM focuses specifically on physical equipment like laptops, monitors, and network gear, ITAM includes everything an organization uses—hardware, software, licenses, cloud subscriptions, and even mobile apps.
Think of HAM as the hands-on side of ITAM. It deals with what’s physically deployed in offices, server rooms, or remote work setups. ITAM goes a step further by tracking how hardware connects with software, who has access to which tools, and whether everything complies with company policy and legal requirements.
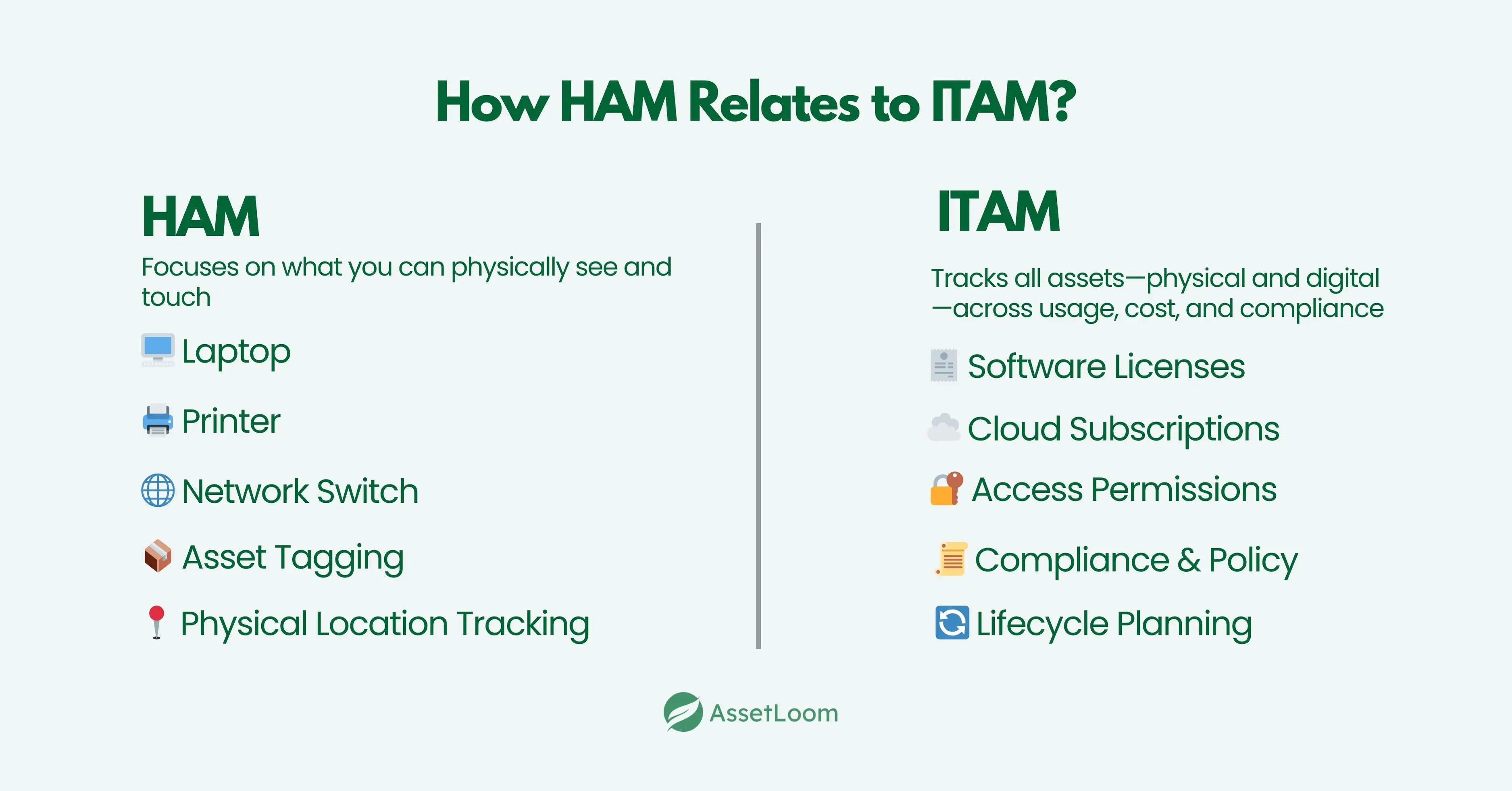
For example, managing a company-issued laptop involves HAM for the device itself and ITAM for the software licenses installed on it, the security protocols it follows, and its role in the wider IT environment.
When HAM and ITAM work together, teams can make better decisions around procurement, usage, support, and replacement. They avoid waste, improve security, and support long-term planning.
The 5 Stages of the Hardware Asset Management Lifecycle
IT hardware asset management isn’t just about knowing where your equipment is. It’s about making sure every device supports the work it was bought for, from the day it’s requested to the day it’s retired. Missing a step along the way leads to unused gear, expired warranties, or even security risks that no one saw coming.
Here’s how the full lifecycle of a hardware asset plays out, using the example of a new enterprise server being added to a hybrid setup:
1. Procurement: Choosing the Right Equipment
Every hardware asset begins with a decision. Procurement isn’t just buying what’s available. It involves matching business needs with the right specs, staying within budget, and making sure the new asset fits the bigger IT plan.
Example: An IT team needs to expand on-prem capacity and settles on a Dell PowerEdge R750. Before ordering, they confirm hardware compatibility, licensing needs, and security requirements. Once approved through their ITSM system, the purchase is linked to vendor agreements and added to the inventory before it even arrives.
2. Deployment: Getting It Ready for Use
Once delivered, the device is tagged, logged, and configured. Deployment is where the asset officially enters the environment, and this step sets the stage for reliable tracking.
Example: The new server is assigned to a rack in the data center. The IT team installs VMware ESXi, sets up monitoring, applies network settings, and locks down security. It’s marked as “Active” in the system, with all details recorded—serial number, warranty, assigned location, and initial configuration.
3. Utilization: Monitoring and Compliance
Now the asset is in use. At this stage, HAM focuses on performance, usage, and making sure all compliance boxes are checked. It’s about keeping the asset productive while avoiding waste or risk.
Example: The server now runs Kubernetes workloads. Teams monitor resource usage through Datadog and review software licenses to avoid violations. If unauthorized tools appear, alerts are raised in the IT dashboard. Everything stays visible and traceable.
4. Maintenance: Keeping It in Good Shape
Over time, assets need updates, replacements, or repairs. Maintenance keeps things running and extends useful life while keeping risk low.
Example: Monitoring tools show that one of the SSDs is wearing out faster than expected. The IT team schedules a replacement before failure. They also apply firmware updates and confirm warranty coverage. These small actions prevent bigger problems.
5. Retirement: Secure, Documented Decommissioning
Every asset eventually hits the end of its life. When that time comes, the focus shifts to secure disposal, proper documentation, and clearing the way for the next upgrade.
Example: After four years, the server is retired. Workloads are moved to cloud infrastructure, the server is wiped using DoD standards, and it’s removed from the inventory. The team logs the disposal process for compliance and updates the asset status to “Retired.”
Read also: The 5 Stages of the Hardware Asset Management Lifecycle You Need to Know
Step-by-Step Strategy to Manage IT Hardware Assets
Managing IT hardware assets well takes more than just tracking devices. It means creating a clear, organized strategy that covers discovery, data accuracy, relationships, enrichment, and operational integration. Here’s a solid approach to making hardware asset management (HAM) effective:
1. Deploy a Lightweight Discovery Agent
Managing assets starts with knowing what you have. Deploy a lightweight agent that scans your hardware environment to gather detailed information like CPU, RAM, storage, network interfaces, and firmware versions. For containerized environments, use tools compatible with Kubernetes to discover hardware running inside clusters.
This agent feeds data continuously into your configuration management database (CMDB), providing a real-time, automatically updated inventory. This foundation ensures you’re managing actual assets instead of relying on outdated or incomplete spreadsheets.
2. Normalize Asset Classes and Data Fields
Raw discovery data can quickly become inconsistent and confusing. It’s important to organize assets into standardized classes such as PhysicalServer, NetworkSwitch, StorageArray, and so on.
For each class, define consistent data fields including model number, serial number, vendor, warranty status, lifecycle phase, and operational state. Enforcing this structure in your CMDB prevents duplicate or unclear entries and supports accurate reporting and decision-making.
3. Automate Mapping of Asset Relationships
Hardware doesn’t exist in isolation. Understanding how assets connect to each other and the services they support adds important context.
Use automated tools that identify logical and physical relationships—for example, which server runs a particular application or which switch connects to which devices. Visualizing these dependencies helps spot orphaned assets or gaps and improves both asset management and service management.
4. Enrich Asset Data with External Sources
A CMDB is most useful when it includes detailed, accurate information. Integrate external data sources such as vendor warranty APIs, software asset management tools, power consumption metrics, and security platforms.
Adding fields like warranty status, power usage, monthly costs, and compliance scores turns each hardware asset record into a rich source of insight. This enriched data supports planning, budgeting, and security audits.
5. Integrate Hardware Asset Management with ITSM Workflows
Asset management should not be siloed. Connect hardware asset data with IT service management (ITSM) processes for incident, change, and request management.
When an asset status changes—such as shifting from operational to warning—the ITSM system can automatically trigger alerts and workflows to ensure fast response. Bi-directional syncing between the CMDB and ITSM tools keeps data consistent and up to date across teams.
IT Hardware Asset Management Best Practices
Managing hardware assets effectively requires more than just tracking serial numbers. These best practices help you keep your hardware inventory accurate, actionable, and aligned with your business needs—especially when working across hybrid environments.
1. Enforce Consistent Tagging from the Start
Tagging assets early and consistently is critical. Make tagging a mandatory part of every provisioning or onboarding step. Typical tags include:
- Location (e.g., Data Center A, Office Floor 3)
- Environment (e.g., Production, Development, Testing)
- Application (which software or service the hardware supports)
- Lifecycle Stage (e.g., In Use, Maintenance, Retired)
For example, one organization integrated tag checks into their deployment approval process: if any asset was missing required tags, the deployment request was automatically rejected until tags were complete. This stopped untracked devices from entering their environment and kept their CMDB clean.
This practice reduces “rogue” devices and ensures your asset data is structured and reliable from day one.
2. Automate Lifecycle Data Updates
Hardware asset status isn’t static. Warranty expiration dates, support contracts, and patch statuses all change over time—and tracking these manually invites errors. Automate lifecycle updates by syncing your CMDB with vendor systems such as Dell or HPE.
For example, a company set up a monthly synchronization job that automatically updated warranty end dates and support tiers. This data powered dashboards alerting IT when assets approached end-of-life or support renewal dates, helping them plan budget and replacement cycles well in advance.
Automation removes the need for manual spreadsheet updates and ensures lifecycle data is always current, improving operational decisions.
3. Track Energy Usage Alongside Performance Metrics
Power consumption matters—not just CPU usage or disk activity. Collecting energy use data helps identify inefficiencies and reduce costs.
For instance, one client integrated smart power distribution units (PDUs) with their asset management system to track watts used by each server. They discovered that their development lab’s servers were drawing twice the power of production servers but running fewer workloads. Using this data, they consolidated hardware, saving thousands in energy costs annually and reducing their environmental footprint.
Including power metrics like PowerDrawWatts or MonthlyPowerCost in your asset records provides insight that CPU graphs alone won’t reveal.
4. Require Relationship Mapping Before Production Deployment
Hardware assets don’t operate in isolation. They support applications, connect to networks, and back up critical services. Mapping these relationships in your CMDB before deploying assets into production is essential.
For example, if a network switch supports the CRM application and a customer-facing website, you need to know this upfront. If the switch fails, the impact on those services is immediately clear, allowing faster incident response.
Some organizations enforce a rule that no hardware goes live without documented relationships like SupportsService, ConnectedTo, or RunsOn. This approach avoids blind spots and guesswork during outages.
5. Include Asset Data in Incident Postmortems
When hardware causes outages or incidents, reviewing the full asset record reveals important clues.
For example, a memory error in a server went unnoticed until a kernel panic crashed production weeks later. Post-incident analysis showed the error had occurred multiple times previously but was never connected to the crash. Including asset change history, firmware versions, and alert logs in postmortems helps identify recurring problems and prevents future downtime.
Making asset data a mandatory part of incident reviews ensures accountability and continuous improvement in hardware management.
Keeping IT Hardware Asset Management Effective Over Time
Implementing hardware asset management (HAM) isn’t a one-time project. It needs constant attention to stay accurate and valuable as your environment grows and changes. Here are some key ongoing practices to keep your HAM working well:
1. Regular Audits and Reconciliation
Schedule routine physical audits to verify the actual presence and condition of hardware against your CMDB records. Automated discovery tools like agents and network scans catch many assets, but nothing replaces a hands-on check every few months.
For example, an organization conducts quarterly audits where IT teams walk through data centers and office floors with barcode scanners to validate asset tags. Any discrepancies found—missing tags, retired equipment still listed as active—are updated immediately.
Reconciling data like this prevents “ghost assets” that inflate inventory counts and mislead capacity planning.
2. Continuous Data Quality Checks
Set up automated validations and alerts for data inconsistencies or missing fields. For instance, if a server is listed without a warranty expiration date or a network device is missing a model number, flag those records for review.
Data quality rules can include:
- Mandatory fields (e.g., serial number, location)
- Correct format checks (e.g., dates, IP addresses)
- Duplicate detection
This proactive approach keeps your CMDB clean and trustworthy, supporting accurate reporting and compliance audits.
3. Integrate with Change Management Processes
Hardware assets frequently change state—being moved, upgraded, repaired, or decommissioned. Integrate asset updates with your IT change management system to ensure every modification is tracked.
For example, when an asset is patched or replaced, the CMDB entry should update automatically, tied to the corresponding change ticket. This creates an audit trail linking hardware changes to business approvals and operational impact.
Such integration supports compliance and improves visibility into asset lifecycle events.
4. Use Analytics for Strategic Planning
Leverage hardware asset data to identify trends and forecast needs. Analytics can reveal when groups of devices are approaching end-of-life or which departments have excess capacity.
For instance, a business used historical warranty and usage data to build a 3-year hardware refresh plan. This plan aligned with budget cycles and minimized disruptions by staggering replacements.
Using asset data for planning turns HAM from reactive tracking into proactive management.
5. Train Teams and Foster Ownership
Asset management works best when everyone involved understands their role—from IT to finance to procurement.
Regular training sessions help teams:
- Use asset management tools correctly
- Understand tagging and documentation importance
- Know how to report issues or changes
Assign clear ownership for asset data quality and lifecycle decisions. When teams feel responsible, errors and oversights decrease.
Common Challenges in IT Hardware Asset Management and How to Address Them
Managing IT hardware assets at scale is never without hurdles. Recognizing the common pain points can help you prepare and avoid costly mistakes.
1. Incomplete or Inaccurate Inventory Data
One of the biggest challenges is ensuring your asset data is complete and up to date. Missing serial numbers, incorrect locations, or outdated status can cause operational headaches and misinformed decisions.
How to address it:
- Deploy automated discovery agents across all environments to capture real-time data.
- Enforce strict data entry standards and validations during provisioning and updates.
- Schedule regular audits to cross-check physical assets with digital records.
2. Lack of Integration Between Systems
Hardware asset data often lives in silos—spread across spreadsheets, procurement tools, monitoring platforms, and CMDBs. This fragmentation leads to gaps and duplication.
How to address it:
- Integrate your HAM system with procurement, monitoring, and ITSM platforms to enable seamless data flow.
- Use middleware or APIs to sync asset status, ownership, and lifecycle info automatically.
- Maintain a single source of truth, typically the CMDB, that reflects all relevant asset details.
3. Poor Relationship Mapping
Without clear relationships between hardware and services, understanding the impact of asset failures is difficult. This slows down incident response and risk management.
How to address it:
- Build automated relationship mapping during discovery—link servers to applications, switches to racks, storage to workloads.
- Use visualization tools to see dependencies and identify orphaned or unsupported assets.
- Regularly review and update these links as infrastructure evolves.
4. Resistance to Change and Lack of Ownership
Implementing or improving HAM requires process changes that can meet resistance. When no one owns asset data quality, errors persist.
How to address it:
- Assign dedicated roles for asset management ownership, including data stewardship and lifecycle decision-making.
- Provide training and clear communication on the benefits and responsibilities involved.
- Tie asset management metrics to team performance goals to encourage accountability.
5. Managing Hybrid and Cloud Environments
With infrastructure spread across on-premises, cloud, and edge, tracking hardware assets consistently becomes more complex.
How to address it:
- Use tools that support hybrid discovery and integrate cloud resource tracking with physical asset management.
- Maintain standardized naming, tagging, and classification across all environments.
- Automate lifecycle and compliance updates to keep pace with dynamic cloud resources.
How to Measure Success in IT Hardware Asset Management
Good hardware asset management isn’t just about tracking assets. It’s about making data-driven decisions that improve efficiency, reduce costs, and minimize risks. To know if your IT hardware asset management efforts are working, you need measurable indicators.
Key Metrics to Track
1. Inventory Accuracy Rate Measures how closely your asset records match the actual physical inventory. Example: Quarterly audits show 98% accuracy, meaning almost all assets are accounted for with correct details.
Why it matters: High accuracy means fewer surprises during incidents or audits.
2. Asset Utilization Shows the percentage of assets actively used versus idle or underused. Example: A report reveals 20% of servers in the data center run at under 10% CPU load, suggesting consolidation opportunities.
Why it matters: Helps optimize infrastructure spend and improve resource allocation.
3. Lifecycle Compliance Rate Tracks the percentage of assets within their supported lifecycle stages (e.g., under warranty, not end-of-life). Example: 95% of laptops are under warranty and compliant with replacement schedules.
Why it matters: Staying compliant reduces downtime and security risks.
4. Mean Time to Detect and Resolve Hardware Incidents Measures the average time from identifying a hardware issue to full resolution. Example: After integrating HAM with ITSM, mean time to resolve dropped from 48 hours to 12 hours.
Why it matters: Faster resolutions minimize business impact.
5. Cost Savings from Hardware Optimization Tracks financial benefits from asset management initiatives like decommissioning unused equipment or renegotiating vendor contracts. Example: Consolidation efforts saved $150,000 annually in power and maintenance costs.
Why it matters: Shows the direct business value of your HAM program.
Conclusion
Effective IT hardware asset management goes beyond just tracking equipment. It requires clear processes, consistent data, automation, and strong integration with your broader IT operations. By deploying discovery tools early, normalizing your asset data, mapping relationships, enriching your records, and linking hardware management to ITSM workflows, you create a system that is reliable, efficient, and audit-ready.
Following proven best practices like enforcing tagging, automating lifecycle updates, monitoring power usage, and thoroughly reviewing asset records after incidents helps prevent costly errors and keeps your infrastructure running smoothly.
Ultimately, strong hardware asset management is the foundation for smarter decision-making, better cost control, and improved service delivery across your entire IT environment.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


