10 Tips for an Effective Software Asset Inventory for US Agencies
US agencies: Boost security and slash waste with 10 powerful tips for your software asset inventory.
Your agency runs on software – every critical system, every daily tool. It's a massive, powerful digital backbone. But here’s the catch: if you don’t truly know what you have, this powerhouse can quickly drain budgets and create surprising security risks.
Imagine managing a huge warehouse of supplies without knowing what’s in stock. You’d waste money and miss critical items. Many U.S. agencies face this with their software. With tight budgets, daily cyber threats, and strict rules, simply "having" software isn't enough. You need to know your software.
This is where a solid software asset inventory truly shines. It’s more than a list; it’s your agency’s strategic tool for smarter spending, ironclad security, and seamless compliance. It’s the map that turns chaos into control. We'll show you how to build and maintain one that works, offering 10 practical tips.
Tip 1: Create a Formal SAM Policy
Ready to take charge of your software? The first step is to formalize the process with a Software Asset Management (SAM) policy. Think of this as your agency’s playbook for handling software.
Why it matters: Without an official SAM policy, you're left with uncertainty. Who can request new software? How do you track it? What happens when an employee leaves the agency? Without clear guidelines, you risk duplicate purchases, unexpected costs, and even security gaps. A formal policy creates structure, accountability, and ensures that everyone is on the same page.
How to make it happen:
- Team Up: Don’t go it alone. Assemble a small, focused team with representatives from IT, procurement, legal, and cybersecurity. This way, you’ll get a holistic view and everyone will feel invested in the policy’s success.
- Define the "Who": Clearly outline who’s responsible for what. Who approves software purchases? Who deploys it? And who’s in charge of decommissioning outdated software? Defining roles avoids confusion and streamlines the entire process.
- Integrate It: Your SAM policy shouldn’t be a standalone document. It needs to align with your agency’s broader IT governance and cybersecurity frameworks. This is about creating a cohesive, secure, and efficient digital ecosystem, not just managing software.
Tip 2: Automate Software Discovery
Now that your SAM policy is in place, the next step is figuring out what software is actually on your agency’s devices. Trying to do this manually with spreadsheets and checklists is like counting grains of sand on a beach—impossible, especially with large government networks.
Why it matters: Manual inventories are often inaccurate, incomplete, and outdated. Software is constantly being installed, updated, or removed, so you need a solution that gives you a real-time, accurate picture of your software. Automation can save your team hours of work and ensure your inventory is always up to date, which is critical for both security and compliance.
How to make it happen:
- Use Smart Tools: Invest in specialized discovery tools. These tools go beyond simple scanning – they dig deep into your systems (servers, desktops, laptops, even cloud environments) and identify exactly what software is installed. Many of these tools use “agents,” small programs that run on each device to report back regularly.
- Look Beyond the Name: Don’t just track the software title. You also need to know the version number and patch level. This information is vital for cybersecurity, as older versions may have known vulnerabilities that need patching.
- Schedule Regular Scans: Automate scans to run on a regular basis – daily, weekly, or even continuously. This ensures your inventory stays fresh and up to date, so you can catch changes as they happen. Think of it as having a dedicated team constantly watching your digital inventory.
Tip 3: Create a Central Repository for Your Data
You’ve automated software discovery – great work! But what happens if all that data is spread across multiple spreadsheets or different departmental systems? It’s like having several lists for the same giant warehouse – confusing and prone to mistakes. Now, it's time to bring everything together in one place.
Why it matters: A central repository for all your software assets is a must for U.S. agencies. It eliminates data silos, reduces discrepancies, and provides everyone – from IT to procurement to security – with a unified, accurate view of your software. This consolidated view is essential for making informed decisions and ensuring smooth audits.
How to make it happen:
- Bring It All Together: Gather all your discovered software data into one central Software Asset Management (SAM) database or dedicated SAM tool. This system will become your single source of truth for every piece of software your agency uses or owns.
- Speak the Same Language: Data normalization is crucial. Ensure that software titles, publishers, and versions are standardized – for example, "Adobe Acrobat Pro" should only appear one way. While this may take a bit of time, it will significantly clean up your data, making it much easier to use and report on.
- Connect the Dots: Link your inventory data with procurement records and license entitlements. This allows you to quickly see not just what software is installed, but who owns the licenses and if you’re in compliance. It’s like matching each book in your library to its purchase receipt.
Tip 4: Link Your Inventory to Cybersecurity
In today’s federal landscape, your software inventory isn’t just about cost management – it’s a critical tool for cybersecurity. With mandates like the Executive Order on Improving the Nation’s Cybersecurity, agencies are under increasing pressure to know exactly what software they have to defend.
Why it matters: If you don’t know what software you have, you can’t protect it. Outdated or unpatched software is a prime target for cyber attackers. Your software inventory becomes your first line of defense, helping you spot vulnerabilities before they escalate.
How to make it happen:
- Demand a Software Bill of Materials (SBOM): For critical applications, especially those used in sensitive operations, request an SBOM from your vendors. This is essentially a full ingredient list for your software, helping you identify its components and any potential risks in the supply chain.
- Cross-Reference for Weaknesses: Regularly compare your software inventory against major vulnerability databases, like the National Vulnerability Database (NVD). This helps flag outdated or unsupported software with known security flaws, giving you a head start on patching.
- Prioritize Patching: Use your inventory to focus patching efforts on the software that’s unauthorized, unsupported, or has high-severity vulnerabilities. This approach ensures you're being proactive, not just reactive.
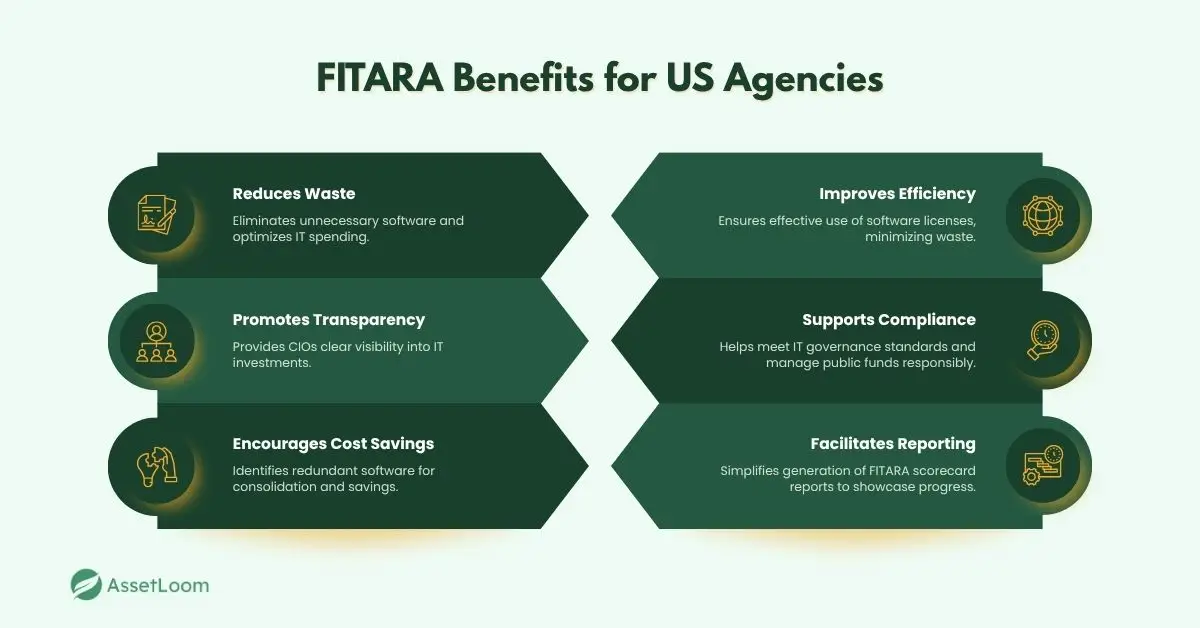
Tip 5: Boost FITARA Compliance and Save Taxpayer Dollars
For U.S. agencies, the Federal Information Technology Acquisition Reform Act (FITARA) is a key driver in smarter IT spending. A comprehensive software inventory isn’t just helpful – it’s essential for compliance and demonstrating responsible use of public funds.
Why it matters: FITARA encourages agencies to eliminate waste, reduce redundancy, and give CIOs clear visibility into IT investments. Your software inventory provides the transparency needed to meet these goals by helping you identify where to cut costs and operate more efficiently.
How to make it happen:
- Spot the Duplicates: Use your software inventory to identify redundant applications. For example, are different departments paying for separate versions of the same collaboration tool? Your inventory will highlight these overlaps, allowing for consolidation and cost savings.
- Reclaim "Shelfware": Analyze software usage data. If you’ve purchased hundreds of licenses for a program but only a few are ever used, that’s “shelfware” – software sitting unused and wasting resources. Reclaim unused licenses and reassign them, avoiding unnecessary purchases.
- Generate FITARA Reports: A well-managed SAM system can easily generate reports needed for the FITARA scorecard requirements. This streamlines the process of demonstrating your agency's efficiency and commitment to managing taxpayer dollars wisely.
Tip 6: Conduct Regular Reconciliations
Think of your software licenses like money in a bank account. You wouldn’t assume your balance is correct without checking it, right? The same principle applies to your software. Regularly comparing what’s installed to what you're licensed for is essential.
Why it matters: Regular reconciliations are your best defense against non-compliance fines and costly “true-up” fees from software vendors. It also helps manage costs by ensuring you’re not over-licensed, keeping you prepared for any vendor audit, and avoiding unexpected issues.
How to make it happen:
- Schedule Regular Check-Ins: Set a regular schedule, like quarterly, to reconcile your software inventory with procurement and license records. This isn’t a one-time task – it’s an ongoing process that should be built into your routine.
- "True-Up" Discrepancies: If you find discrepancies – like having more software installed than you’re licensed for, or vice versa – address them right away. This “true-up” process involves either removing excess software or purchasing additional licenses to stay compliant.
- Build Your License Library: Create a secure, centralized library for all your license agreements, purchase orders, contracts, and proofs of purchase. This will be your go-to reference for every software entitlement, making audits and reconciliations much easier.
Tip 7: Categorize and Classify Your Software
Not all software is created equal in an agency. For example, a sensitive defense application needs a different approach than a basic office tool. Organizing your inventory beyond just a list helps you prioritize what needs attention and apply the right level of security.
Why it matters: Categorizing your software helps your team focus on what to manage closely, which updates to prioritize, and what security controls to apply. This ensures critical systems receive the attention they need while identifying software that could pose unnecessary risks.
How to make it happen:
- Authorized vs. Unauthorized: Label software in your inventory as either “Authorized” (approved by your agency) or “Unauthorized” (e.g., shadow IT, potentially risky). This helps you quickly spot unapproved software installations.
- Function and Criticality: Classify software by its function (e.g., operating system, database, specialized mapping software) and its importance to your agency’s mission. Knowing something is “Mission Critical” immediately elevates its priority.
- Flag End-of-Life (EOL) Software: Identify and mark any software nearing or past its End-of-Life (EOL) or End-of-Service (EOS) date. This software is typically unsupported and can pose significant security risks that need to be addressed.
Tip 8: Manage the Full Software Lifecycle
An effective software inventory isn’t just a snapshot of what’s installed right now. It’s about tracking software from the moment it’s requested, through its active use, and all the way to its retirement. Think of it as knowing the full “life story” of every piece of software.
Why it matters: Managing the entire lifecycle helps your agency optimize costs, ensure compliance, and reduce security risks at every stage. It prevents software from lingering unused or becoming a security liability once it’s no longer needed.
How to make it happen:
- Standardize Requests: Implement a clear, agency-wide process for employees to request new software. This ensures proper approvals, budget checks, and correct license allocation before any software is installed.
- Smart Offboarding: When employees leave, have a documented process for uninstalling agency-licensed software from their devices (both agency-owned and, if applicable, personal ones). This helps free up licenses and protects agency data.
- Secure Decommissioning: When software is no longer needed, don’t just delete the icon. Ensure there’s a secure, documented process for decommissioning the software, terminating maintenance contracts, and properly disposing of any associated data or systems.
Tip 9: Train Your Team on SAM Policies
Your agency's employees are often the first line of defense—or, sometimes unknowingly, the first point of risk when it comes to software. Having policies in place isn’t enough; your team needs to understand them and why they matter.
Why it matters: An informed workforce is a compliant and secure workforce. Employees who understand the agency’s software rules are less likely to install unauthorized applications, reducing security risks and ensuring license compliance.
How to make it happen:
- Regular, Clear Training: Offer training sessions on your agency’s software policy for new hires and regular refreshers for current employees. Don't just present the rules; explain why they matter, highlighting the security, compliance, and budget impact.
- Communicate the Risks: Clearly explain the dangers of installing unapproved software. Discuss risks like malware, data breaches, and how non-compliance could affect the agency—and possibly individual careers.
- Make It Easy to Comply: Provide an accessible, user-friendly software catalog or portal. When employees know which software is approved and how to request new titles easily, they’re more likely to follow the rules.
Tip 10: Set KPIs and Measure Success
You've built a solid software asset inventory. Now, use Key Performance Indicators (KPIs) to demonstrate its value. Effective IT inventory management helps track key metrics that highlight the program’s impact on leadership.
Why it matters: KPIs help prove the value of your SAM program to agency leadership, justify continued investment, and identify areas for improvement. It’s about showing tangible results and becoming more efficient over time.
How to make it happen:
- Track Key Metrics: Begin tracking important metrics, such as the percentage of software under active management, the reduction of unauthorized software instances, the cost savings from optimizing licenses, and improvements in audit readiness.
- Report to Leadership: Regularly present these KPIs to your leadership team. Highlight the progress made, cost savings achieved, and how the program is strengthening security and compliance. This builds trust and ensures continued support.
- Iterate and Improve: Don’t just track numbers—use the insights from your KPIs to refine your SAM processes, update your tools, and adapt to your agency’s evolving needs. Continuous improvement ensures your inventory remains effective and valuable over the long term.
Conclusion
Managing your agency’s software assets isn’t just about tracking licenses—it’s about creating a smarter, more secure, and more cost-effective operation. By following these 10 essential tips, you’ll not only improve compliance but also empower your team, optimize spending, and reduce security risks.
A well-managed software inventory is the foundation of a more efficient agency that’s ready to face tomorrow’s challenges today. Start transforming your approach to software asset management now, and turn every tool you use into a strategic advantage.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.

