Why ITAM Is Critical for Zero Trust Security
Zero Trust can’t work without visibility, where IT Asset Management (ITAM) becomes essential. Every Zero Trust pillar depends on having a complete, up-to-date view of your assets.
Zero Trust isn’t just a security strategy. It’s a mindset. But it starts with knowing what you actually have.
If you don’t know which devices are on your network, what software is running, or where your data lives, you can’t protect any of it. That’s where IT Asset Management (ITAM) comes in. Think of it as the foundation that every smart security decision is built on.
Zero Trust means never assuming anything is safe. Every user, device, and app must be verified before access is granted. But verification depends on visibility. And visibility starts with asset management.
In this post, we’ll cover:
- Why ITAM is critical to making Zero Trust work
- How ITAM helps reduce risk and meet compliance goals
- Practical ways to improve your asset inventory and close security gaps
Let’s start with a clear look at what ITAM really is and why it matters more than you might think.
What Is ITAM, Really? (And Why It’s More Than a Spreadsheet)
IT Asset Management, or ITAM, is the practice of tracking and managing all the technology assets your organization owns, uses, or connects to. That includes laptops and desktops, servers, mobile devices, software licenses, cloud subscriptions, and even virtual machines or containers.
Think of ITAM as your single source of truth for what’s in your environment. It helps you answer questions like:
- What assets do we have?
- Where are they?
- Who’s using them?
- Are they secure, supported, and compliant?
Many teams still rely on spreadsheets, static CMDB, or fragmented systems to manage this data. The result? Incomplete inventories, outdated records, and missed risks.
But ITAM isn’t just recordkeeping. It’s operational awareness. It's knowing the difference between a managed device and a mystery guest on your network. And it's how you lay the groundwork for stronger security, faster incident response, and smarter decision-making.
The Zero Trust Model: Trust Nothing, Verify Everything
Zero Trust is a security philosophy built on the principle that no one, whether inside or outside your network, should be trusted by default. Instead, every request for access, every device, and every user is verified and validated continuously.
With the modern landscape of remote work, hybrid infrastructure, BYOD (bring your own device), and cloud-first environments, the traditional perimeter is no longer enough to protect sensitive data. That’s why Zero Trust is so crucial.
Core pillars of Zero Trust include:
- Verify identities: Ensuring users and devices are who they claim to be.
- Validate devices: Checking the security status of devices before granting access.
- Limit access: Only allowing users and devices the least amount of access they need.
- Monitor continuously: Ongoing monitoring to spot and stop suspicious activities in real time.
For Example: Imagine an employee tries to access sensitive data from their personal smartphone. With Zero Trust, the device would be verified, and if it’s not registered or secure, access would be denied. Without visibility into your assets, you wouldn’t be able to make that decision.
But here’s the catch, Zero Trust can’t work without visibility. You can’t enforce strict access controls, continuously monitor threats, or validate devices if you don’t know what devices or software are in your environment in the first place.
And that’s where IT Asset Management (ITAM) becomes essential. Every Zero Trust pillar depends on having a complete, up-to-date view of your assets. Without it, you’re trying to protect your network with blind spots.
5 Ways ITAM Directly Supports Zero Trust
When you implement a Zero Trust security model, the goal is clear: don’t trust anything automatically, and always verify. But achieving Zero Trust isn't possible without knowing exactly what you're trying to protect. This is where IT Asset Management (ITAM) plays a critical role. By giving you a clear and up-to-date inventory of all your devices, software, and digital assets, ITAM provides the visibility needed to enforce Zero Trust policies effectively.
Here are five specific ways ITAM directly supports and strengthens your Zero Trust approach:
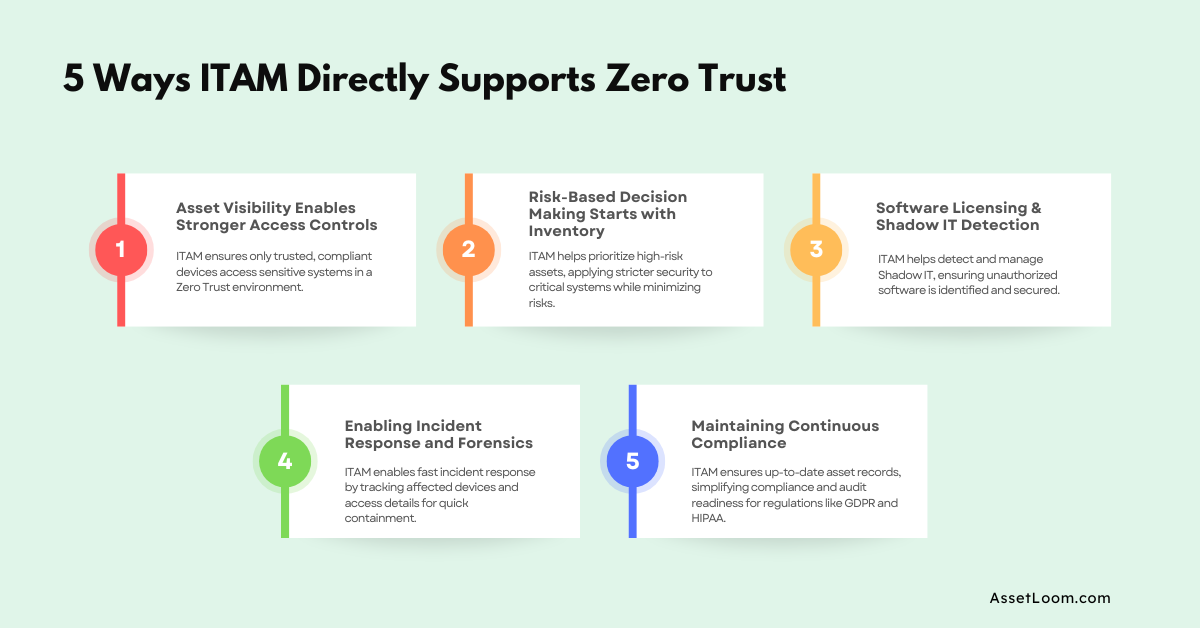
1. Asset Visibility Enables Stronger Access Controls
In a Zero Trust environment, access control is a critical piece of the puzzle. You can’t decide who should have access to what if you don’t know what devices or software are connected to your network. This is where IT Asset Management (ITAM) plays a key role.
By having a full view of all devices and software in use, you can ensure that only trusted, compliant devices are allowed to connect to sensitive systems, effectively preventing unauthorized access.
Example: If an employee tries to use their personal laptop to access company files, you need to know if that device is approved and secure. ITAM helps you track every device, so you can stop unapproved ones from connecting to your network.
2. Risk-Based Decision Making Starts with Inventory
One of the key principles of Zero Trust is ensuring that users and devices only have access to the minimum resources they need. But how do you know which devices or systems are more critical? That’s where ITAM can help you prioritize your resources based on risk.
As a result, with ITAM, you can easily identify high-risk assets, such as servers containing sensitive data, and apply the most stringent security measures to them while focusing less on low-risk assets, like that printer.
3. Software Licensing & Shadow IT Detection
One of the most common risks in modern IT environments is Shadow IT; when employees or departments use software or devices that aren't officially approved by IT. Shadow IT can bypass your security policies and could even introduce security gaps in your Zero Trust model.
ITAM enables you to monitor and manage the software in use across your entire organization. With proper inventory management, you can spot unapproved tools (Shadow IT) quickly, ensuring they’re either brought into your secure environment or removed entirely.
Example: A marketing team might start using a cloud-based design tool without telling IT because it’s easier than going through the approval process. While the tool may seem harmless, it could store sensitive customer data or have weak security protocols that put the company at risk. Without ITAM, this kind of "hidden" software could remain undetected for months.
By tracking all software licenses and usage, ITAM keeps your network safe from unexpected, unmanaged risks that could compromise your Zero Trust policies.
4. Enabling Incident Response and Forensics
When a security incident happens, you need to respond quickly. ITAM helps by providing real-time information on which devices are affected and who had access to them, making your incident response more efficient.
The faster you can figure out which assets were compromised, the faster you can contain the threat. ITAM helps you isolate and address issues before they spread.
Example: After a breach, ITAM shows you which device was compromised and when it last accessed sensitive data. With this information, your team can act fast to contain the issue.
5. Maintaining Continuous Compliance
For many businesses, compliance with regulations like GDPR, HIPAA, or NIST is essential. ITAM ensures your asset records are always up to date, making it easier to stay compliant.
Regulatory audits require accurate asset records. ITAM keeps your inventory current, so you’re always ready for an audit without scrambling at the last minute.
Example: When it’s time for an audit, ITAM quickly provides a list of all software licenses and hardware, ensuring you meet regulatory requirements without stress.
Common Challenges and How to Start Fixing Them
If you’re struggling with asset management, you’re not behind; you’re normal.
Most organizations face challenges when trying to keep track of their IT assets. It’s not just about buying the right tool or setting up a spreadsheet. It’s about building a process that keeps up with constant change: new devices, new apps, remote workers, cloud services, and everything in between.
Here are four of the most common challenges, why they’re a problem for Zero Trust, and some practical steps to start fixing them.
1. Outdated asset inventory
If your inventory is only updated every few months (or only during audits), you’re likely missing key information. Devices go missing. Software gets installed and forgotten. Cloud services appear and vanish without notice.
In a Zero Trust environment, every decision relies on accurate, real-time information. If you don’t know a device exists, you can’t verify or protect it.
How to fix it: Start by using automated asset discovery tools. These can scan your network to find devices and services you might not even know are there. From there, connect your inventory to your change management process so updates happen automatically as assets come and go.
2. Shadow IT and rogue devices
Shadow IT happens when teams or individuals use software, tools, or devices that haven’t gone through your IT or security review. It’s usually not malicious; someone just needed to get something done quickly. But it creates risk.
These unmanaged tools and devices don’t follow your security policies. That makes them easy entry points for attackers and blind spots for your security team.
How to fix it: Combine regular network and cloud scans with friendly user education. Let teams know why it matters to go through the right channels. Make it easy for them to request tools so they’re not tempted to work around the process.
3. Siloed asset data across departments
In many organizations, different teams track assets in different systems. IT has one list, security has another, and procurement might have something else entirely. That leads to mismatched data, confusion during incidents, and inconsistent security policies.
If your Zero Trust model is going to work, everyone needs to be working from the same source of truth.
How to fix it: Bring your asset data into one shared platform. It doesn’t need to be perfect from day one, but start consolidating what you have. Involve stakeholders from security, compliance, and IT so you’re building a system everyone can rely on.
4. Manual tracking methods (like Excel)
Spreadsheets are fine for short-term tracking or small environments, but they don’t scale. They’re easy to break, hard to update, and nearly impossible to keep in sync with real-world changes.
Relying on manual methods makes it much harder to respond quickly to threats or stay compliant with regulations.
How to fix it: Invest in a modern ITAM platform that can automatically update your inventory, integrate with your other tools, and help you stay audit-ready. Start small if needed; the goal is to save time and reduce human error.
Final Thoughts
You can’t protect what you don’t know about. And in a Zero Trust world, that’s not just inconvenient; it’s dangerous.
Every part of a Zero Trust strategy depends on visibility. That means knowing what devices are connected, what software is running, and where your data lives. IT Asset Management gives you that visibility. Without it, you’re guessing. With it, you’re in control.
Let’s recap:
- Zero Trust is about verifying everything, not trusting by default
- ITAM provides the foundation by showing you what you’re working with
- Strong asset management reduces risk, improves compliance, and speeds up incident response
- You don’t need to fix everything at once even small improvements can make a real impact

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


