How Can I Track a Stolen Laptop and Prevent Future Loss?
Lost your laptop? Learn how to track a stolen laptop, secure your data, and prevent future thefts with smart tools and hardware asset management strategies.
Losing a laptop can bring a major headache, considering the sensitive data at risk of being exposed. If you're wondering, "How can I track a stolen laptop?", you're not alone. A huge number of devices are stolen every day, with significant consequences, from data breaches to intellectual property loss.
Fortunately, there are ways to track a stolen laptop and increase the chance of recovering it. In this blog, we'll guide you through the actionable steps to track your laptop if it is stolen, as well as prevent future thefts and protect your valuable assets.
So, let’s dive into how you can not only track that laptop but also make sure it doesn’t happen again.
First Things First: What To Do Immediately After Your Laptop Is Stolen
It could be frustrating when your laptop is stolen. But rather than being panicked, you should immediately take action to minimize damage and hopefully track down your device. Here's a quick checklist of what you should do after realizing your laptop has been stolen:
1. Report the Theft
First things first: inform the appropriate parties of the incident. Don't count on things to work themselves out. Here's who you should get in touch with:
- Your Organization: If you are using the laptop for work, let your security team or IT department know. They will be equipped to remotely lock down your device or prevent access to business systems.
- The Police: Submit a police report. This is an important step to support legal reasons and authorities' efforts in tracking your laptop.
- Your Insurance Provider: If your laptop is insured, make sure to report the theft to your insurance company as soon as possible to start the claims process.
2. Lock the Device Remotely
If you’ve enabled remote tracking features (like Find My Device on Windows or Find My Mac on macOS), now is the time to use them. With these built-in features, you can lock your laptop remotely and even display an on-screen message (e.g., "This laptop has been stolen. Please contact me"). If your company uses Mobile Device Management (MDM) tools, it's also a good idea to activate them so that you can lock or wipe the device remotely.
This way, you can decrease the risk of your laptop's files, emails, and sensitive data being accessed by a thief.
3. Change Passwords for Important Accounts
It's time to secure your accounts after locking your device. Change the passwords for all important services that you can access from your laptop right away. These could consist of:
- Email accounts (especially work email, which could be the gateway to other sensitive company systems)
- VPN and company tools (access to internal networks or cloud storage)
- Financial accounts (online banking, payment services)
You may want to enable two-factor authentication (2FA) on these accounts for added security, ensuring that even if someone tries to break into your accounts, they won’t succeed.
4. Monitor Suspicious Activity
The criminal might try to sell your data on the black market or use your login credentials for bad purposes. Therefore, you should closely monitor your accounts in the days after the theft. Pay attention to any odd attempts to log in, strange devices gaining access to your accounts, or password-changing attempts. Besides, consider using a fraud alert or identity theft monitoring service to swiftly identify illegal activity.
How Can I Track a Stolen Laptop? Here’s What Works
With the right tools, you can definitely track your stolen laptop. While there’s no guarantee you’ll get it back, these laptop tracking solutions can raise your chance of recovering your device. Let’s explore the options:
1. Use Built-In Tracking Features
Both Windows and macOS offer built-in tools to help you track your laptop. These tools, when enabled, can be lifesavers in case of theft.
-
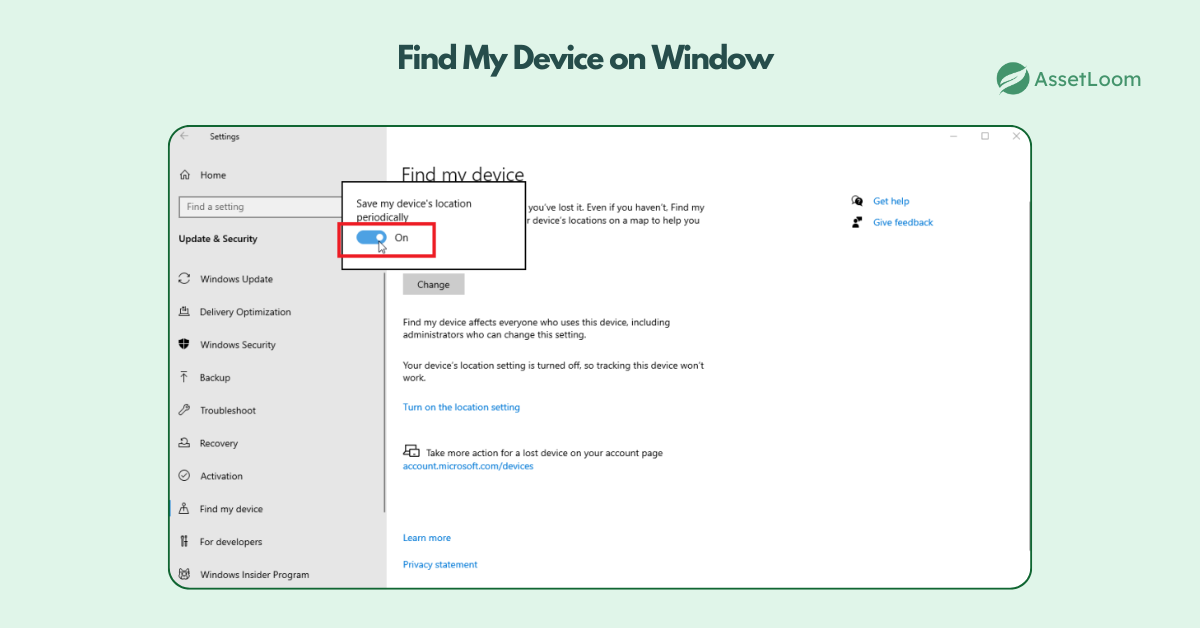
Windows (Find My Device): If you're using Windows 10 or later, make sure you’ve enabled the "Find My Device" feature. Once activated, you can log in to your Microsoft account and check the location of your laptop. You can also lock the device or remotely erase data.
-
To enable it beforehand: Go to Settings > Update & Security > Find My Device and toggle it on.
-
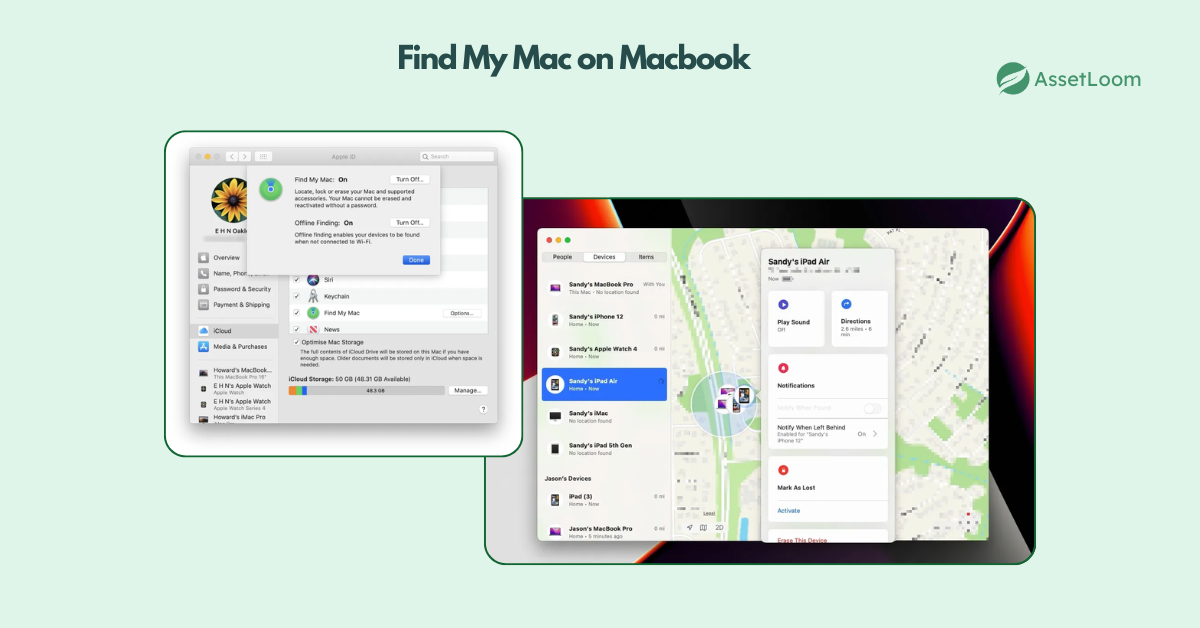
Mac (Find My Mac): For macOS users, Find My Mac allows you to track, lock, or erase your MacBook if it’s connected to the internet. You can access it through iCloud or the Find My app on another Apple device.
-
To enable it beforehand: Go to System Preferences > Apple ID > iCloud, and make sure Find My Mac is checked.
2. Use Third-Party Tracking Software
If you had third-party tracking software like Prey, Life360, or MoniMaster installed, you have access to additional tracking tools:
- To find the location of the device, use live GPS tracking.
- To protect your data, use remote locking and wiping.
- Webcam access to take pictures of the thief in action.
- Alerts that let you know when the laptop is moved or turned on.
Because these apps frequently operate in the background, it is more difficult for thieves to find or delete them.
3. Check Login Activity from Cloud Accounts
If the thief attempts to access apps like Google, Microsoft, or Dropbox, these services usually log:
- Last login time
- Device type
- IP address and approximate location
Log in to these services from another device to check the activity logs. This can provide valuable information for both you and law enforcement.
4. File a Police Report with Serial Number
File a police report right away using your laptop's serial number, which can be found on the box, invoice, or purchase history. In addition to being necessary for proving ownership, this number may be useful in the event that the device is sold or recovered. Remember to find out if stolen electronics are covered by your insurance.
5. Monitor Online Marketplaces
Frequently, stolen laptops wind up on websites that sell used electronics, such as Facebook Marketplace, Craigslist, or eBay. Look for listings on these websites that correspond to the model and specifications of your laptop. You can even configure alerts to notify you in the event that your device is put up for sale.
Enter Hardware Asset Management: Your Secret Weapon Against Laptop Loss
We've already discussed how to prevent your devices from becoming easy targets and what to do in the event that a laptop is stolen. Let's go a step further, though: what if you could monitor every laptop you own well in advance of any issues?
This is where hardware asset management (HAM) is useful.
So, What Is Hardware Asset Management?
At its core, HAM is the process of tracking and managing your organization’s physical IT assets, from purchase to retirement. It answers essential questions like:
- Who is currently using this device?
- Where was it last located?
- What software is installed?
- When was it last online or serviced?
Instead of relying on outdated spreadsheets or scattered notes, HAM centralizes this information, giving IT teams clarity and control over all their assets, especially laptops.
How It Helps You Stay in Control
Here’s what hardware asset management; especially when powered by a tool like AssetLoom, brings to the table:
- Complete Inventory Management: Keep a current inventory of all hardware assets, including their status and specifications.
- Accurate Location Tracking: Keep tabs on each device's location and movement across various areas.
- Comprehensive Ownership Records: Monitor the distribution of assets among staff members, guaranteeing responsibility.
- Proactive Maintenance Scheduling: Arrange routine maintenance to prolong the life of your device and avoid unplanned malfunctions.
- Automated Alerts: Get alerts when things like end-of-life, inactivity, or unauthorized movement occur.
HAM offers a digital trail that supports insurance claims and recovery efforts in theft or loss situations.
Real-World Scenario: From Panic to Plan
Imagine a situation where a remote worker reports that their laptop, which was provided by the company, has been stolen. AssetLoom allows you to:
- Review of Asset Assignment: Immediately determine which employee was given the laptop and confirm the assignment information.
- Last Known Activity: The device's last known IP address and activity prior to going offline are displayed in the access logs.
- Usage Analysis: Assist in evaluating possible data breaches by determining whether the device was accessed after theft.
- Detailed Reporting: Produce thorough reports to support law enforcement and expedite insurance procedures.
A potentially chaotic situation is turned into a manageable process by this proactive approach.
Final Thoughts
Although losing a laptop is never easy, it doesn't have to be a major catastrophe. You can locate a stolen device, reduce damage, and possibly even recover it if you have the correct information and tools.
Here's a brief summary:
- Quickly report the theft, secure the device, and change the passwords.
- Make use of tracking tools, both third-party and integrated.
- Utilize hardware asset management to maintain thorough records.
- Take preventative action by using tools like asset tagging and encryption.
The secret is to change your perspective; asset management is your first line of defense and not just an IT task. Platforms like AssetLoom can also make it much easier to stay secure, organized, and ahead of potential problems when you're managing a large number of devices.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.