How to Manage Different Types of IT Hardware in Asset Management?
Learn how to manage different types of IT hardware in asset management and key strategies for optimizing your assets efficiently.
IT hardware is a critical part of business operations, but tracking and maintaining all the devices can be overwhelming. From servers to laptops to printers, each piece of equipment needs attention. Failing to organize and track these devices can lead to inefficiencies, security risks, and unexpected costs.
A clear system for managing IT hardware ensures that each device is used effectively, stays secure, and works as intended. In this blog, we’ll explore how to handle different types of IT hardware in it asset management, offering practical tips for tracking, maintaining, and optimizing your devices to improve efficiency and reduce costs. Let’s dive in.
Understanding IT Hardware Types
IT hardware can be divided into functional categories based on the role they play in a system. These categories help in organizing and managing the equipment efficiently. Here are the key types of IT hardware you need to know:
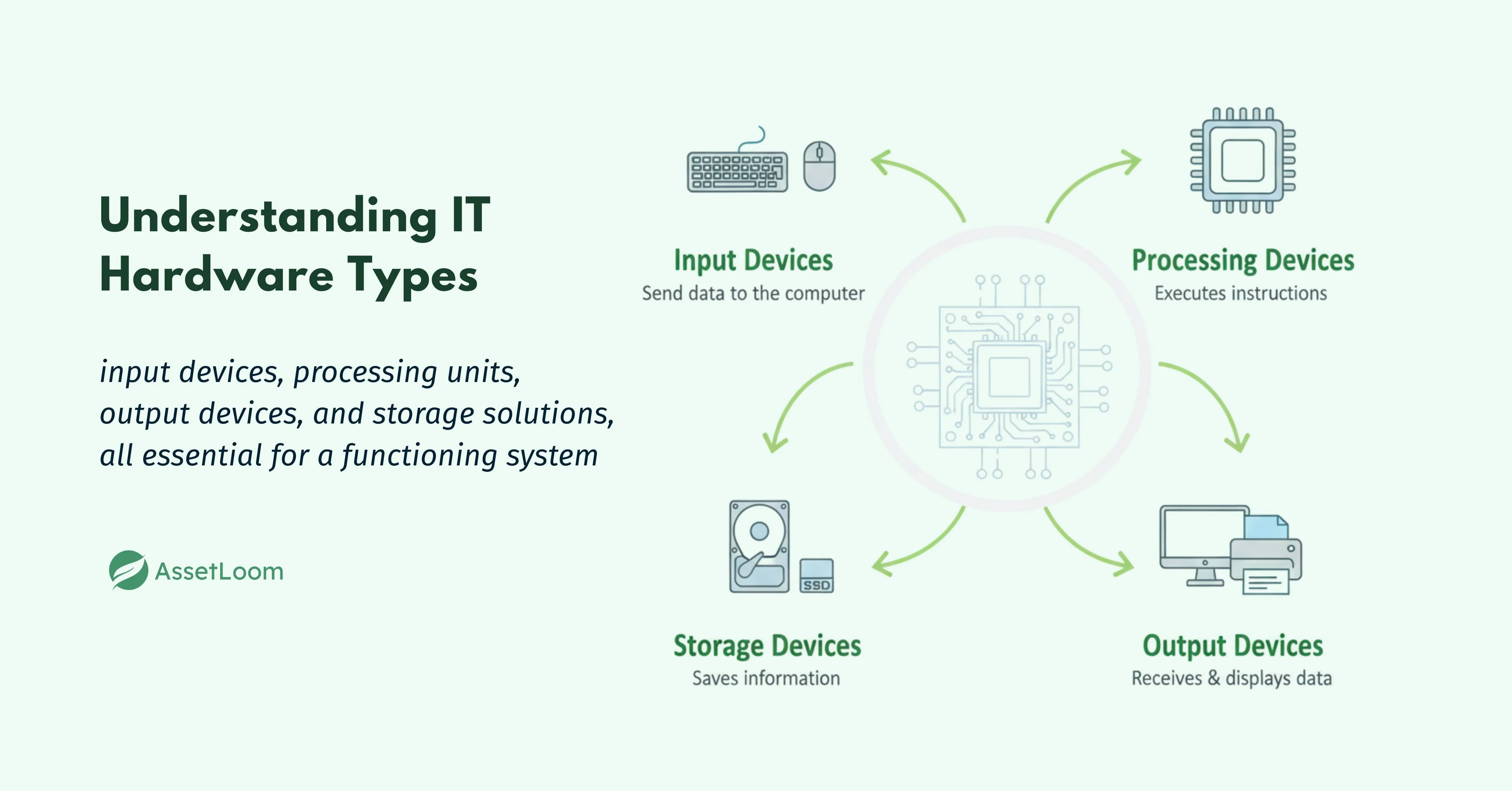
1. Input Devices
Input devices are tools that allow users to interact with a computer or system by providing data and commands. These devices send information to the system for processing, making them essential for user input. Here are some common examples:
- Keyboards: Used to input text and commands into the computer. Keyboards come in various styles, including wired, wireless, mechanical, and membrane, depending on the system’s needs.
- Mice: A pointing device used to move a cursor on the screen and interact with the system’s graphical user interface (GUI). Mice can be wired, wireless, or even have specialized features such as additional buttons or optical sensors.
- Scanners: Devices that convert physical documents, images, or text into digital formats, which can then be processed, stored, or edited by the computer.
- Cameras: Cameras are used for capturing visual data, such as images or videos, and can also serve as input devices for video calls, security systems, or document scanning.
2. Processing Devices
Processing devices are the core components responsible for interpreting, executing instructions, and processing data in a computer system. These devices are essential for the functionality of any computing environment, as they handle all the operations required for running applications and performing calculations.
Examples:
- CPU (Central Processing Unit): The CPU is often referred to as the "brain" of the computer. It processes instructions from programs and handles the system's overall functioning.
- GPU (Graphics Processing Unit): A GPU is a specialized processor designed to handle graphics rendering and visual data. It is primarily used for rendering images, videos, and animations, making it essential for gaming, video editing, and 3D modeling.
- Motherboard: The motherboard is a critical component that connects all internal hardware and allows communication between the CPU, GPU, RAM, and other components. It serves as the main circuit board that facilitates data transfer and ensures all parts work together.
These processing devices work together to ensure smooth operation, high performance, and responsiveness of the system. Proper management of processing hardware is essential for maintaining system speed, stability, and the ability to handle complex tasks.
3. Output Devices
Output devices present processed data from the computer in a form that users can understand. These devices convert digital signals into visual, printed, or audible formats. Here are some examples:
- Monitors: Display visual information, allowing interaction with the system through graphical interfaces.
- Printers: Convert digital files into physical copies (e.g., documents, images).
- Speakers: Output audio, providing sound for media, calls, or notifications.
- Headphones: Offer personal audio output for focused listening or private communication.
These devices are essential for user interaction with processed data, ensuring that information is accessible and usable.
4. Storage Devices
Storage devices are used to store and retrieve data for later use. These devices provide both short-term and long-term storage for files, programs, and system data. Here are some examples:
- Hard Disk Drives (HDDs): Traditional storage devices that use spinning disks to read/write data. They offer large storage capacity but slower speeds compared to newer technologies.
- Solid-State Drives (SSDs): Faster and more reliable than HDDs, SSDs use flash memory to store data, offering quicker access times and better durability with no moving parts.
- RAM (Random Access Memory): A type of temporary, fast-access storage used by the CPU for actively running programs and data. It is wiped clean when the system shuts down.
Internal vs. External Hardware
IT hardware can be categorized into internal and external components based on their location and function within a system.
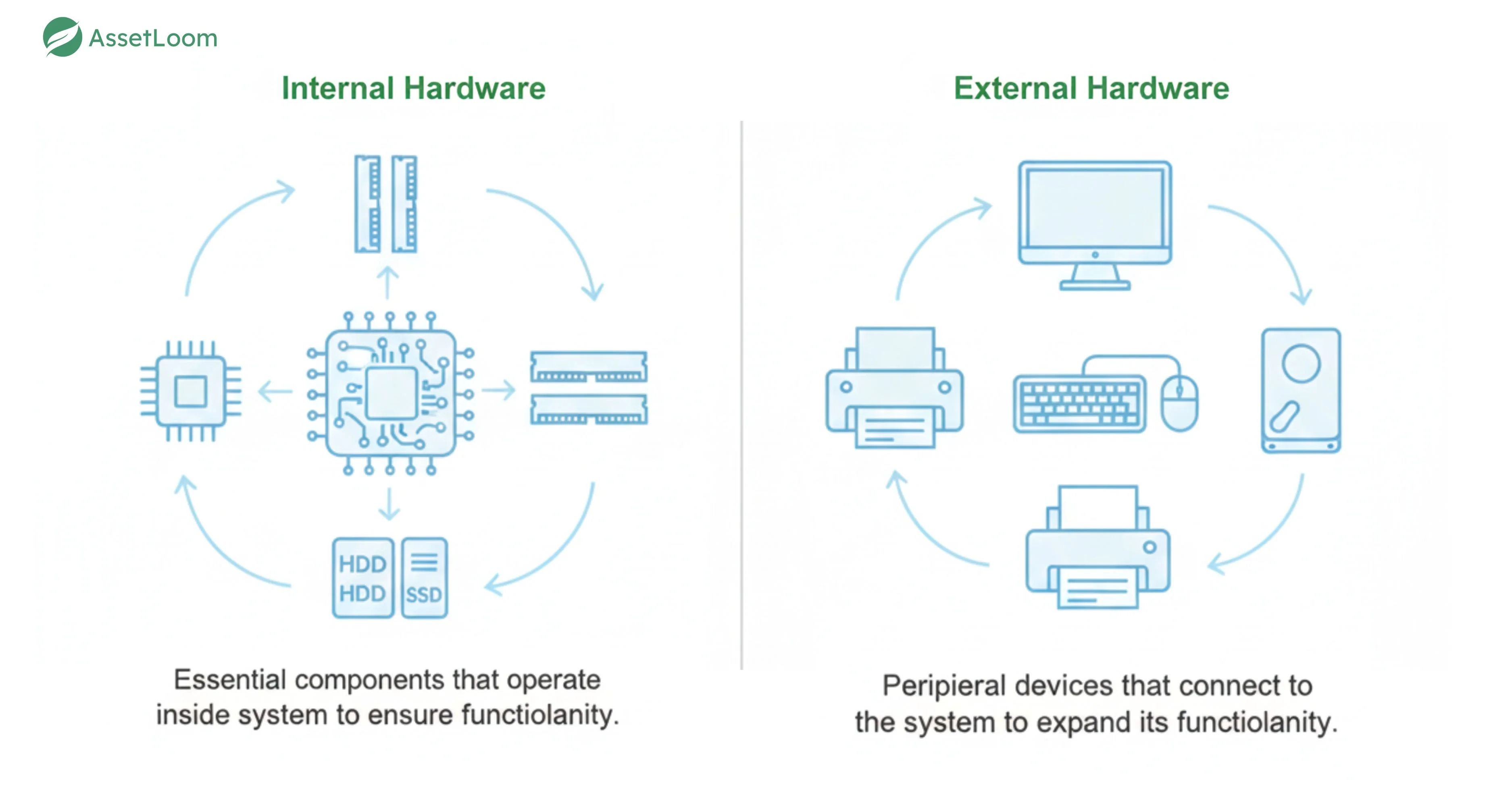
Internal Hardware
Internal hardware is integrated within the computer or system and is necessary for its core functionality. These components are housed inside the system case and typically handle essential operations.
Examples:
- Motherboard: The central circuit board that connects all internal components.
- CPU (Central Processing Unit): The processor that executes instructions and performs calculations.
- RAM (Random Access Memory): Temporary storage that helps the CPU process data quickly.
- Internal Storage (HDD/SSD): Devices for long-term storage of data, programs, and the operating system.
External Hardware (Peripheral Devices)
External hardware connects to the system from the outside, usually through ports like USB, HDMI, or Bluetooth. These devices enhance the functionality of the computer but are not essential for its basic operation.
Examples:
- External Monitors: Displays used for extended or additional screen space.
- Keyboards and Mice: Input devices used for interaction with the system.
- External Hard Drives: Provide additional storage capacity or backup options.
- Printers and Scanners: Used for document output and digitizing physical documents.
Both internal and external hardware are vital for ensuring a system operates effectively, with internal components handling core functions and external devices offering enhanced usability.
Key IT Hardware Components
The key components of IT hardware are the building blocks that power and support a computer system. Here’s a breakdown of the most essential hardware components:
1. Motherboard
The motherboard is the central circuit board that connects all internal components and allows them to communicate with each other. It holds the CPU, RAM, and other crucial parts while providing ports for peripheral devices.
2. CPU (Central Processing Unit)
The CPU is the "brain" of the computer, responsible for executing instructions, performing calculations, and managing data flow between other hardware components. It plays a key role in determining system speed and performance.
3. RAM (Random Access Memory)
RAM is temporary, fast-access storage that the CPU uses to store data and instructions for active processes. It enables quick retrieval and smooth execution of tasks. The more RAM a system has, the more programs it can handle simultaneously.
4. Storage Drives (HDD/SSD)
Storage devices are used to save data for long-term use.
- HDD (Hard Disk Drive): Traditional storage devices that use spinning disks. They offer high capacity at a lower cost but slower speeds.
- SSD (Solid-State Drive): Faster and more durable than HDDs, SSDs use flash memory for quicker data access, making them ideal for speed and reliability.
5. GPU (Graphics Processing Unit)
The GPU handles rendering images, videos, and animations. It processes graphical data and outputs it to the display. A powerful GPU is essential for tasks like gaming, video editing, and 3D modeling.
These key IT hardware components work together to ensure a system operates efficiently, handles data smoothly, and provides a great user experience. Proper management and maintenance of these components help extend the lifespan and performance of the entire system.
Best Practices for Managing Different Types of IT Hardware
Effectively managing IT hardware involves more than just keeping track of devices. It requires a clear strategy and processes to ensure that hardware is utilized efficiently, remains secure, and operates at optimal performance throughout its lifecycle. Here are some best practices for managing different types of IT hardware:
1. Tracking and Labeling Hardware
![]()
Tracking and labeling hardware is essential for managing IT assets efficiently. By keeping accurate records of where each device is and how it’s being used, businesses can prevent loss, ensure devices are properly allocated, and streamline the management process. Here’s how to effectively track and label your IT hardware:
Use Asset Tags or Barcodes
- Asset Tags: Attach a unique asset tag to each device to assign it a unique identifier. These tags can include barcodes, QR codes, or RFID chips to make identification easier.
- Barcodes/QR Codes: Use barcode scanners or mobile devices to quickly scan and track hardware. QR codes can be linked to an online inventory system for easy updates.
Centralized Inventory System
- Cloud-Based or On-Premises Systems: Implement a centralized inventory management system (such as an IT asset management software) that stores data about each device, including its location, user, status, and maintenance history.
- Real-Time Updates: Ensure that the system is updated in real-time whenever hardware is moved, serviced, or decommissioned, so the information is always accurate.
Track Hardware Lifecycle
- Monitor Device Status: Keep track of each hardware’s condition, performance, and usage over time. This allows you to know when devices are due for maintenance, upgrades, or replacement.
- Location Tracking: For devices that move between departments or locations (e.g., laptops or mobile devices), use GPS tracking or internal labels to ensure the device’s whereabouts are always known.
Maintain Detailed Documentation
- Record Device Information: For each device, document essential information such as the make, model, serial number, purchase date, warranty details, and current user or department.
- Keep Maintenance Logs: Track any repairs, upgrades, or software installations, along with dates, to maintain a comprehensive record of the device’s lifecycle.
2. Regular Audits and Updates
Regular audits and updates are key to maintaining accurate records and ensuring that your IT hardware remains secure and functional throughout its lifecycle. Here’s how to implement effective audits and keep your devices up to date:
Periodic Audits
- Conduct Routine Audits: Perform regular physical checks on all IT hardware. This helps verify the condition of the devices and ensures they are being used properly. It also ensures that any discrepancies in your asset records are caught early.
- Audit Frequency: Depending on the size of your hardware inventory, audits can be performed monthly, quarterly, or annually. For high-value or critical devices, consider more frequent audits.
- Inventory Reconciliation: Compare physical assets with records in your asset management system. Ensure that devices are in the right location, being used by the correct employees or departments, and are functioning properly.
Firmware and Software Updates
- Keep Hardware Updated: Regularly update firmware and software to ensure that all devices are running the latest versions. Updates can address security vulnerabilities, improve performance, and add new features.
- Automate Updates: Use centralized management tools that allow you to automate software updates, patches, and firmware upgrades. This helps ensure that devices are always up to date, without requiring manual intervention.
- Test Updates: Before applying updates across your entire hardware inventory, test them on a smaller batch of devices to avoid widespread issues.
Track Warranty and Support Information
- Monitor Expiring Warranties: Keep track of warranty periods for all hardware and ensure that repairs or replacements are covered. Proactively plan for devices whose warranties are about to expire.
- Support Contracts: Ensure that you have active support contracts for critical devices. Track expiration dates and renewal terms to ensure you have ongoing access to manufacturer support.
Manage Device Health
- Monitor Performance: Regularly check the performance of hardware devices to identify any issues that could be addressed early. This can include tracking CPU usage, memory, storage capacity, and hardware errors.
- Preventative Maintenance: Set up scheduled maintenance for devices, such as cleaning, checking for hardware wear, and ensuring there’s no accumulation of dust or other factors that might impact performance.
3. Lifecycle Management
Lifecycle management is the process of managing an IT hardware device from its acquisition to its retirement. A structured approach ensures that hardware is efficiently utilized, properly maintained, and securely decommissioned. Here’s how to manage the lifecycle of IT hardware:
Procurement and Deployment
- Plan for Device Acquisition: During the procurement phase, choose hardware that meets the needs of your organization and fits within your budget. Consider factors such as scalability, performance, and compatibility with existing systems.
- Proper Deployment: Ensure that each device is properly set up and configured to integrate with your network. This includes installing necessary software, performing security checks, and verifying the device is ready for use.
Maintenance and Usage
- Scheduled Maintenance: Implement a routine maintenance schedule to keep devices in top working condition. This could include cleaning, updating software, replacing parts, or addressing any hardware issues.
- Monitor Device Performance: Continuously monitor devices for issues like overheating, software crashes, or excessive wear and tear. Regular performance reviews help identify potential problems early, allowing you to take preventive action.
- Asset Usage Tracking: Track how each device is being used, and monitor for underutilization. This helps to optimize the deployment of assets and identify devices that may no longer be necessary or need replacing.
Upgrades and Repairs
- Upgrade Hardware as Needed: As technology evolves, certain components like memory or storage may need to be upgraded. Rather than replacing entire devices, upgrading key components can extend the life of hardware and improve performance.
- Repair and Replace Faulty Devices: Address issues promptly through repair or replacement. Keep a system for tracking which devices are undergoing repairs, the types of issues being fixed, and when the devices are back in service.
Retirement and Disposal
- Secure Decommissioning: When devices reach the end of their useful life, ensure they are decommissioned properly. This involves wiping data securely to prevent any sensitive information from being exposed.
- Recycling and Disposal: Follow environmentally responsible recycling practices for outdated devices. Many hardware components can be recycled, helping to reduce e-waste and comply with regulations.
- Data Destruction: Before disposing of or selling old hardware, ensure all data is wiped according to industry standards (e.g., NIST guidelines) to prevent data breaches.
4. Maintenance and Proactive Monitoring
Regular maintenance and proactive monitoring are essential to ensuring the longevity and reliability of IT hardware. By addressing potential issues before they lead to failures, businesses can minimize downtime and extend the lifespan of their devices. Here’s how to implement effective maintenance and monitoring strategies:
Preventive Maintenance
- Schedule Routine Checkups: Regular maintenance checks, such as cleaning internal components and inspecting cables, can prevent issues like overheating, dust buildup, and hardware wear. Scheduling these checks at regular intervals (e.g., quarterly) helps maintain the health of devices.
- Replace Worn Components: Over time, hardware components like hard drives, batteries, or cooling fans may degrade. By identifying and replacing these parts early, you can avoid complete system failures and ensure devices continue to perform optimally.
- Calibration and Upgrades: Some devices, such as printers or servers, may require periodic calibration to ensure accurate functioning. Additionally, upgrading components (e.g., adding more RAM or upgrading storage) helps keep hardware aligned with business needs.
Proactive Monitoring
- Monitor Performance Metrics: Use monitoring tools to track key performance indicators (KPIs) like CPU usage, memory load, disk health, and network bandwidth. Regularly check these metrics to identify any irregularities or performance bottlenecks.
- Set Alerts for Issues: Proactively set up alerts to notify IT staff when devices are underperforming, nearing capacity, or encountering errors. Early detection through alerts can help address issues before they cause major disruptions.
- Real-Time Tracking: Implement real-time monitoring tools that track the health of your devices. This allows for immediate identification of any problems, such as overheating, hardware malfunctions, or slow response times, enabling prompt corrective action.
Automated Diagnostics and Updates
- Automate Diagnostics: Use diagnostic tools that run automated checks on hardware, identifying common issues and reporting them without requiring manual inspection. These tools can alert technicians to potential hardware failures, reducing downtime.
- Regular Software and Firmware Updates: Ensure that hardware is kept up to date with the latest software and firmware updates. These updates can enhance security, improve performance, and fix bugs, so scheduling them regularly helps avoid vulnerabilities and ensures smooth operations.
Tracking Device Health
- Conduct Health Checks: Regular health checks of IT devices can detect issues such as memory degradation, failing hard drives, or outdated firmware. Documenting the health status of devices over time helps track trends and predict when devices may need to be replaced or upgraded.
- Track Warranty and Support: Keep an eye on warranties for devices and ensure that support contracts are up to date. This ensures that repairs or replacements are covered under warranty, reducing unexpected costs.
5. Documentation and Reporting
Proper documentation and reporting are crucial to maintaining an organized IT hardware management system. Detailed records ensure that you have full visibility of your assets, their performance, and any changes or issues that arise over time. Here’s how to manage documentation and create effective reports:
Keep Detailed Records
- Device Information: Record essential details for each piece of hardware, including the make, model, serial number, purchase date, and warranty status. This information helps track the device’s lifecycle and manage its maintenance effectively.
- Usage and Ownership: Maintain records of who is using the device, the department it’s assigned to, and its current status (e.g., active, in repair, or decommissioned). This helps in resource allocation and tracking.
- Maintenance and Repair History: Document all maintenance activities, repairs, and upgrades. This includes dates, types of issues, and actions taken. A complete history makes it easier to predict when a device may need replacing or further repairs.
Generate Regular Reports
- Asset Inventory Reports: Create regular inventory reports that provide an up-to-date view of all IT hardware assets. These reports should include details like device status, location, and maintenance history.
- Performance Reports: Regularly generate performance reports to track how devices are performing over time. This helps in identifying underperforming hardware and planning for necessary upgrades or replacements.
- Cost and Depreciation Reports: Track the costs associated with each device, including purchase price, repair costs, and maintenance fees. These reports help you assess the total cost of ownership and the depreciation of assets, which is important for budgeting and future planning.
Audit Trails
- Track Changes and Updates: Keep a record of any changes made to devices, such as software updates, hardware upgrades, or shifts in ownership. This audit trail helps maintain accuracy in asset management and ensures accountability.
- Compliance Audits: Regular audits help ensure that your hardware is compliant with industry regulations and company policies. Audits also provide a clear picture of your organization’s hardware health, helping to identify any gaps or risks in your asset management practices.
Documentation for Data Security
- Data Wiping and Disposal Logs: When retiring or disposing of devices, ensure that all sensitive data is securely wiped. Keep detailed logs of the disposal process, including data destruction methods and confirmation of compliance with relevant security standards.
- Warranty and Support Documentation: Track the details of warranties and support contracts for each device. Having this information readily available ensures that you can act quickly when hardware issues arise and stay on top of support renewal dates.
Utilize IT Asset Management Software
- Centralized Management System: Use asset management software to store all documentation and generate reports automatically. This system centralizes your records and makes it easier to update, track, and retrieve information about your IT hardware.
Tools and Software for IT Hardware Asset Management
To manage IT hardware effectively, businesses need the right tools for tracking, maintaining, and optimizing assets. One such tool is AssetLoom, an intuitive IT asset management solution designed to help organizations efficiently track and manage their hardware. AssetLoom allows businesses to monitor their devices, track usage and performance, and streamline the lifecycle management process—from procurement to retirement. With its easy-to-use interface and powerful tracking features, AssetLoom ensures that IT hardware is optimized, secure, and well-maintained throughout its lifecycle.
Conclusion
Managing different types of IT hardware is essential for ensuring the smooth operation of any business. From tracking assets with labels and tags to performing regular audits and updates, effective hardware management helps reduce downtime, minimize costs, and extend the lifespan of devices. Implementing strong lifecycle management, proactive maintenance, and using the right tools like AssetLoom for asset tracking can significantly improve operational efficiency and security.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


