Protect IT Gear with Anti-Theft Asset Tags
Learn how anti-theft asset tags secure laptops, monitors, and office gear, helping IT teams reduce loss and improve asset management.
Every IT team has faced the challenge of keeping track of company laptops, monitors, or printers. A device goes missing, and suddenly there’s a gap in inventory, a user left waiting, and sometimes even sensitive data at risk. Replacing the hardware is costly, but the bigger issue is the disruption it creates across the business.
This is why many organizations turn to anti-theft asset tags. By tagging IT and office equipment with unique, tamper-resistant labels, IT teams can monitor devices more effectively, discourage theft, and make audits less of a headache. It’s a practical step that improves both security and accountability across the workplace.
What Are Anti-Theft Asset Tags?
Anti-theft asset tags are small but powerful tools for protecting business equipment. At first glance, they may look like simple labels or stickers, but they are designed to do much more. These tags are made with tamper-resistant material, so if someone tries to peel them off, they leave behind a clear mark that shows the device has been tampered with.
Many anti-theft tags also come with barcodes, QR codes, or RFID chips. This means IT teams can scan them to instantly pull up details about the device, like who it belongs to, when it was issued, and where it should be. In other words, they help with both security and record-keeping.
For employees, the tag acts as a reminder that the device is tracked and accounted for. For IT teams, it’s an easy way to connect physical equipment to digital asset records, making audits and inventory checks faster and more accurate.
Why IT Gear Needs Anti-Theft Protection
IT equipment plays a central role in keeping a business running. From laptops and desktops to printers and servers, every device supports daily operations. Losing even one piece of equipment can cause delays, add costs, and put sensitive data at risk. This is why theft prevention and tracking are critical for IT teams.
High Value of IT Assets
Laptops, monitors, and servers often represent a large share of a company’s IT budget. Replacing them is expensive, and the sudden loss can strain resources. Beyond the purchase price, businesses also face the cost of downtime while waiting for replacements.
Data Security Risks
When IT devices are lost or stolen, the risk isn’t limited to hardware. A laptop can contain sensitive company files, customer information, or login credentials. If that data ends up in the wrong hands, it can lead to compliance issues, financial penalties, or reputational damage.
Portability Increases Risk
Devices that move around — like laptops, tablets, or projectors — are especially vulnerable. They are easy to carry, use outside the office, and, unfortunately, easier to steal. Even shared office equipment, such as printers or monitors, can disappear because they are simple to resell.
Extra Burden on IT Teams
When equipment goes missing, IT teams must update records, investigate the issue, and sometimes deal with security follow-ups. This creates unnecessary workload and can delay other projects. Anti-theft measures like asset tags help reduce these problems by keeping assets visible and accountable.
How Anti-Theft Asset Tags Work
Anti-theft asset tags do more than stick onto devices — they bring structure and accountability to how IT equipment is tracked and managed. Here’s a closer look at how they help IT teams in practice:
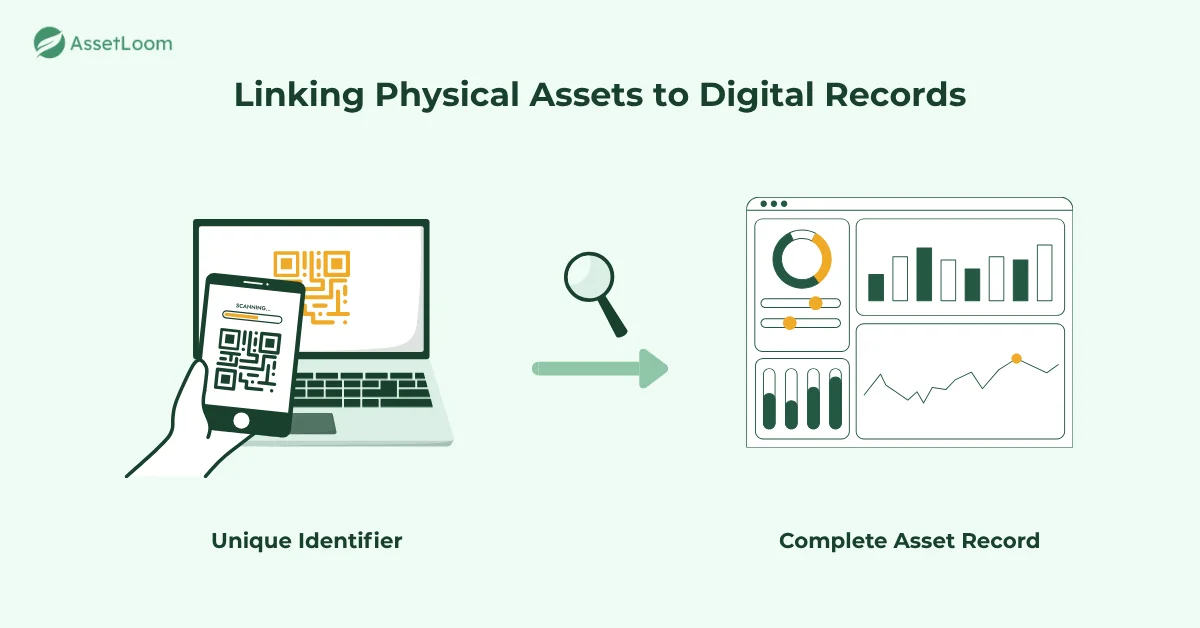
Linking Physical Assets to Digital Records
Each tag carries a unique identifier — usually a QR, barcode, or RFID chip — that connects directly to a company’s asset database. When IT staff scan a laptop tag, they don’t just see the serial number. They can also view who the laptop is assigned to, its purchase date, warranty details, and service history. This creates a complete digital trail for every device.
Detecting and Deterring Unauthorized Removal
Anti-theft tags are tamper-evident by design. If someone tries to peel one off, it leaves behind a clear mark or breaks apart, making it obvious that the device has been tampered with. In environments like schools, co-working spaces, or shared offices, this simple feature discourages casual theft and protects against unnoticed equipment swaps.
Simplifying Audits and Compliance Checks
For IT teams, one of the most time-consuming tasks is verifying that the inventory list matches the physical devices in use. Tags make this process easier. By scanning devices during audits, teams can instantly confirm location, user assignment, and compliance with licensing or security requirements — reducing the chance of errors in reporting.
Supporting Broader IT Asset Management
When integrated with IT asset tracking software, tags become part of a bigger system. IT teams can monitor the full lifecycle of equipment — from purchase to deployment, maintenance, and retirement — with minimal manual work. This integration also helps detect missing devices faster, reducing financial and security risks.
Example: A mid-sized marketing agency added tamper-proof tags to all employee laptops and linked them to its IT asset tracking software. Before tagging, year-end audits took weeks of manual checks. With the new system, the IT team scanned each device during routine check-ins, cutting audit time by more than half while also reducing cases of misplaced laptops.
Benefits of Anti-Theft Asset Tags for IT Teams
For IT teams, managing equipment is more than just keeping devices in order — it’s about saving time, reducing risks, and keeping the business running smoothly. Anti-theft asset tags provide several practical benefits that support these goals:
- Faster inventory management: Tags can be scanned quickly, making it easier to check assets during audits or routine inspections. This saves IT teams from the time-consuming task of manually recording serial numbers and ensures asset records stay accurate.
- Lower risk of theft and loss: Because anti-theft tags are tamper-evident, they make devices less attractive to steal. If a device does go missing, the unique tag ID makes it easier to identify and recover, reducing both replacement costs and downtime.
- Better compliance support: Many industries require strict asset tracking for data security and regulatory reasons. Asset tags linked to IT records give teams reliable proof that devices are accounted for, helping them pass audits and avoid fines.
- Improved accountability: Assigning tagged devices to employees makes responsibilities clearer. Staff are more careful when they know equipment is tracked, which helps reduce cases of missing or misplaced assets.
- Lifecycle visibility: When used with IT asset tracking software, tags give IT teams a clear view of each device’s history — from purchase to maintenance and eventual retirement. This visibility helps with budgeting, forecasting, and making smarter replacement decisions.
In short, anti-theft asset tags give IT teams the tools they need to protect equipment, improve efficiency, and keep assets under control throughout their entire lifecycle.
Implementation Tips for Anti-Theft Asset Tags
Rolling out anti-theft asset tags effectively takes more than just sticking labels on devices. To get the most value, IT teams should approach tagging as part of a structured asset management process. Here are some advanced tips to consider:
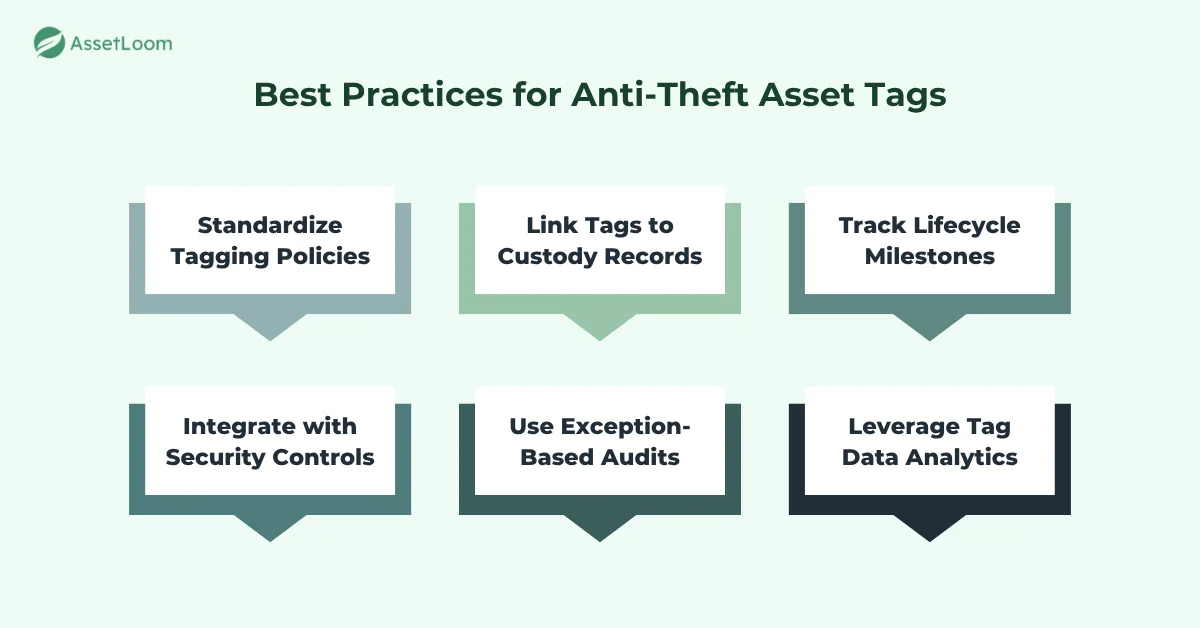
1. Standardize Tagging Policies Across All Asset Types
Don’t leave it up to individual IT staff to decide how and where to apply tags. Create a policy that defines tag type, placement, and data fields for every asset category — laptops, desktops, servers, peripherals, and even accessories. This consistency reduces confusion and speeds up audits.
2. Pair Tags with Ownership and Custody Records
A tag alone won’t stop a laptop from being lost, but when tied to a custody log, it creates accountability. Every time an asset changes hands — whether it’s assigned to a new employee or moved to another office — it requires a scan and update in the IT asset tracking software. This builds a clear trail of responsibility.
3. Use Tags to Enforce Asset Lifecycle Milestones
Instead of only scanning tags during audits, use them at key points in the hardware lifecycle: deployment, maintenance, and retirement. For example, when a laptop comes in for repair, scanning the tag can automatically log the service. At the end-of-life, scanning confirms the device was decommissioned securely.
4. Align Tagging with Security and Access Controls
Go beyond inventory by linking tagged devices to security policies. For instance, ensure that any untagged laptop is automatically flagged in your system and restricted from connecting to the company network until properly registered. This prevents “shadow devices” from slipping into use.
5. Audit by Exception Instead of Full Sweeps
Once tags are in place, IT teams don’t need to do painful full audits as often. Instead, use exception-based auditing: flag devices that haven’t been scanned in a set period or appear in unusual locations. This saves time and focuses attention on assets most likely to be missing or misused.
6. Combine Physical Tags with Analytics
Don’t treat tags as just stickers — treat them as data points. By analyzing scan data, IT teams can spot patterns such as departments with higher rates of equipment loss or employees who frequently request replacements. These insights help improve policies and cut down on recurring problems.
Real-World Scenarios for Anti-Theft Asset Tags
Anti-theft asset tags prove their value in many different environments. Here are a few examples of how they solve everyday challenges:
In education, schools and universities often issue laptops or tablets to students. At the end of the year, collecting them all can be difficult. Tags make it easier to scan devices on return, reduce unreported losses, and cut replacement costs.
In healthcare, mobile devices like tablets and diagnostic equipment constantly move between departments. Losing track of them can slow down care and put patient information at risk. Tamper-resistant tags provide visibility and discourage theft, ensuring equipment stays where it should.
In corporate offices, hybrid work means laptops and monitors often move between home and office. Tags make it easier for IT teams to maintain accountability, so devices aren’t forgotten or misplaced during transitions.
In retail and warehousing, scanners, tablets, and point-of-sale systems change hands many times a day. Misplaced equipment can cause delays on the shop floor. Anti-theft tags help keep this high-use gear tracked and available when needed.
Conclusion
Protecting IT equipment is about more than replacing lost hardware — it’s about preventing disruption, avoiding extra costs, and keeping work moving. Anti-theft asset tags offer a simple but effective way to achieve this. They make devices easier to track, discourage theft, and strengthen accountability across the organization.
For IT teams managing a wide range of laptops, monitors, and shared devices, anti-theft asset tags are a small investment that delivers lasting value.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox

