8 Tips to Manage an Effective Incident Response Plan for Enterprise Cloud Security
Discover 8 tips to manage an effective incident response plan for enterprise cloud security, including roles, asset prioritization, and real-time monitoring.
Managing cloud security is no small task, especially when a breach, cyberattack, or system failure occurs. For businesses relying on the cloud, it's not a matter of if an incident will happen, but when. Without a solid incident response plan, your team can be left scrambling, struggling to contain damage, and facing delays in recovery.
This guide provides 8 actionable tips to help you manage an effective incident response plan for Enterprise Cloud Security. From defining roles to setting up real-time monitoring, these tips will help ensure your team is prepared to act quickly, minimize damage, and get your systems back on track with confidence.
1. Create a Cloud Incident Response Team
When a security incident hits, time is crucial. A well-defined Cloud Incident Response Team (CIRT) with clear roles ensures your team acts quickly and efficiently.
First, assign a Cloud Security Officer to lead the response. The Incident Manager will coordinate efforts to contain the issue. Cloud Engineers diagnose and resolve the problem, while the IT support team isolates affected systems. Legal and Compliance teams handle communications with regulators and customers.
For example, in the retail industry, the Cloud Security Officer focuses on securing payment systems, while Cloud Engineers address issues with the e-commerce platform. IT support isolates any compromised customer data.
To make things smoother, define roles in advance and use cloud asset management tools to quickly locate critical assets, minimizing downtime and damage during an incident.
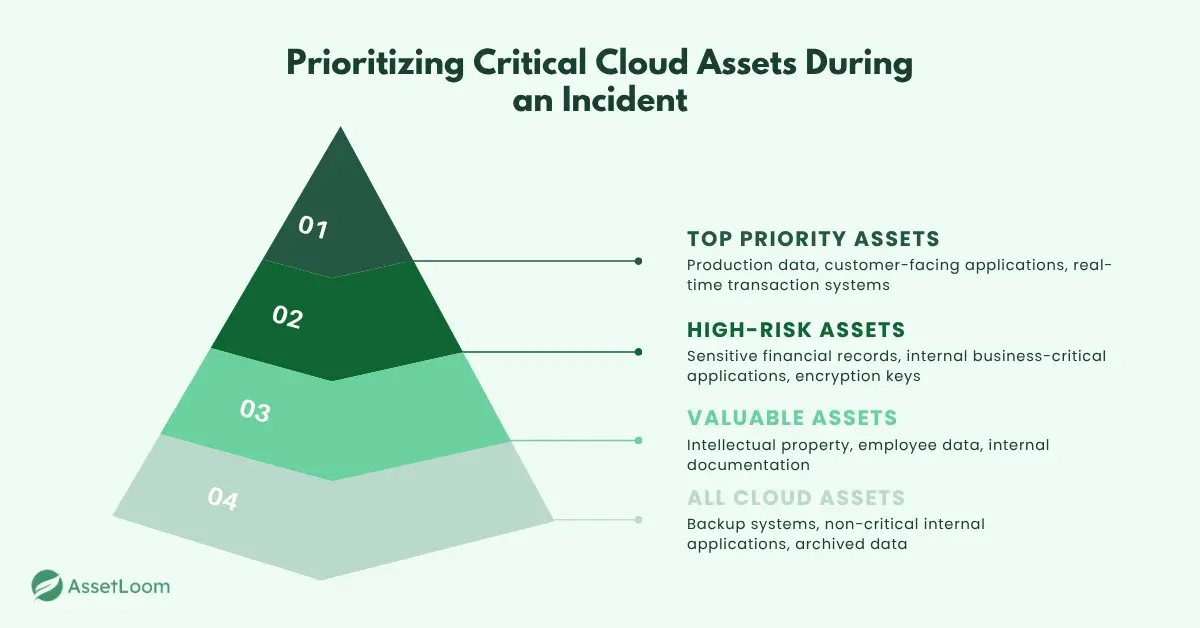
2. Prioritize Critical Cloud Assets
When a security incident happens, the last thing you want is to scramble and figure out which assets to protect first. With so many services, data, and systems in your cloud, it can feel overwhelming. But not all assets are equally critical. Knowing where to focus can make all the difference.
Start by identifying your most valuable assets, sensitive customer data, key business systems, and intellectual property. In the retail industry, for example, your top priorities would be payment information, inventory systems, and e-commerce platforms.
Using a CMDB discovery tool can help map out relationships between your assets and identify dependencies. This makes it easier to see which assets are most affected and need attention right away. Tagging these critical assets in your cloud-based inventory management system lets your team find them quickly, speeding up response times.
Then, prioritize. For a retailer, securing payment systems and customer databases should be your first focus, while less critical systems, like internal analytics, can wait.
By focusing on the most important assets, your team can avoid wasting time and get your business back on track faster.
Read also: Top 5 Cloud Asset Management Best Practices
3. Set Up Real-Time Monitoring and Alerts
In cloud security, waiting for an incident to escalate can be too late. Real-time monitoring is your first line of defense, catching threats before they turn into full-blown crises.
Start by implementing cloud-native monitoring tools, like AWS CloudTrail, Azure Security Center, or Google Cloud’s operations suite, to continuously track activity across your environment. These tools can alert you to abnormal behavior, like unauthorized access or unusual data transfers.
Set up automated alerts to notify your security team as soon as suspicious activity is detected. For instance, in retail environments, an alert might trigger when a large volume of customer payment data is accessed outside of regular business hours. The quicker your team is alerted, the faster they can act.
Make sure your team knows how to respond immediately with predefined procedures for containment and escalation. This ensures that when an alert is triggered, your team can jump into action without hesitation.
By monitoring your environment in real time and acting fast, you reduce the impact of security incidents before they can do real damage.
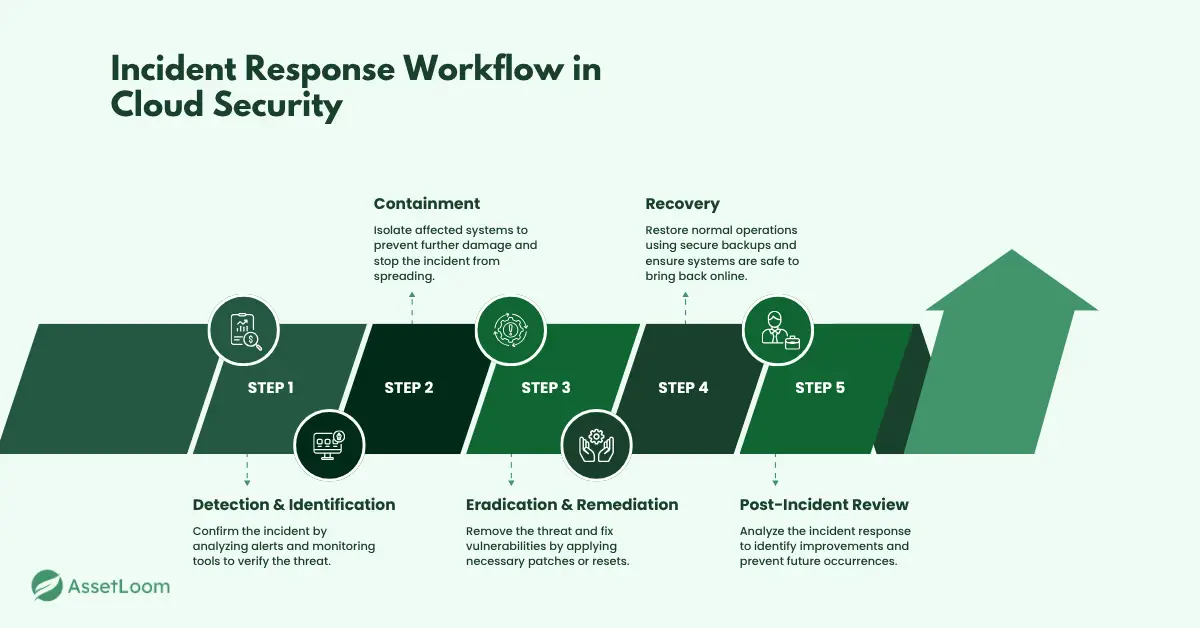
4. Develop a Clear Incident Response Workflow
When a security incident happens, it’s easy for panic to set in. That’s why having a clear incident response workflow in place is crucial, so your team can stay calm, focused, and follow a proven process every step of the way.
Start by breaking down each stage of the response process:
- Detection and Identification: The first step is confirming that an incident is actually happening. This is where monitoring tools and team instincts come in. Define what signals should trigger an alert and how to quickly verify if something’s truly a threat.
- Containment: Once an incident is confirmed, it’s about stopping it from spreading. Whether that means isolating affected systems or cutting off access to sensitive data, quick containment is key to minimizing damage.
- Eradication and Remediation: Now that the threat is contained, it’s time to get rid of it completely. Your team needs to work together to eliminate the root cause of vulnerabilities, reset credentials, or apply any necessary fixes.
- Recovery: After the threat is gone, it’s time to restore normal operations. This is where backups and recovery procedures come in. Ensure your team knows how to bring systems back online safely, without exposing you to more risk.
- Post-Incident Review: Once things are back to normal, it’s important to reflect on the incident. What went well? What could be improved next time? Hold a quick debrief to identify lessons learned and make sure the response plan is even stronger going forward.
In the retail sector, this might mean isolating customer payment systems or e-commerce platforms during an attack, followed by restoring those systems as quickly as possible without compromising security.
By having a clear workflow mapped out in advance, your team will know exactly what to do at every stage, making the response faster and more effective.
5. Test Your Incident Response Plan Regularly
A plan is only as good as its execution, and without regular testing, gaps can go unnoticed. Simulated incident drills, like mock data breaches or DDoS attacks, are crucial for making sure your team is ready when a real crisis hits.
Schedule these drills quarterly or biannually, simulating different types of incidents like data breaches or system outages. After each drill, debrief with your team to discuss what worked, what didn’t, and where improvements are needed. This helps keep your team sharp and ensures the plan is always evolving.
For instance, in the retail industry, you might simulate a scenario where payment systems are compromised, and the team practices containing the breach and restoring payment services while maintaining customer trust.
Regular testing builds muscle memory, so when an actual incident occurs, your team can respond quickly and efficiently.
6. Establish Clear Communication Channels
During a cloud security incident, poor communication can slow your team down and increase confusion. To avoid this, establish clear communication channels ahead of time.
Define who needs to be informed at each stage. For example, during detection and containment, the security team needs immediate updates, but as recovery begins, you should inform executives and external stakeholders. A centralized communication platform like Slack or an incident management tool helps provide real-time updates and keeps everyone aligned.
In the retail sector, ensure that customer support and the legal team are notified promptly if sensitive customer data is involved, to manage communications with affected customers and regulators quickly.
With clear communication protocols in place, your team can respond faster and more cohesively.
7. Document Everything
When a security incident occurs, documenting every step is essential, not just for operational purposes but also for compliance with regulations like GDPR or HIPAA.
Track every action your team takes, from detection to containment and resolution, using an incident management system. This documentation creates an audit trail, which is valuable for reviewing the response and improving future actions. It also ensures that you can demonstrate compliance if required by regulators.
In retail environments, this might include logging all access to payment systems, customer records, and inventory data during the incident. Having accurate records allows you to confidently communicate the details of the incident to regulators and affected customers.
By documenting everything, you can improve future responses and meet compliance requirements.
8. Continuously Improve Your Plan
A great incident response plan isn’t static; it needs to evolve. Each incident offers valuable lessons, and without continuous improvement, your plan can quickly become outdated.
After every incident or drill, take time to review the process. What worked well? What didn’t? Identify bottlenecks or areas for improvement and update the plan accordingly. Feedback from your team will help refine workflows, tools, and communication strategies to enhance your response for the future.
In the retail industry, as new technologies like mobile payment systems or e-commerce platforms emerge, your incident response plan should adapt to address new risks and attack vectors.
By making continuous improvement a part of your incident response process, you ensure your team remains agile and ready to handle any future incidents more efficiently.
Conclusion
An effective incident response plan for Enterprise Cloud Security ensures your team can act quickly when an issue arises. By defining roles, prioritizing assets, and setting up real-time monitoring, you’ll be ready to respond faster and more efficiently.
The key is continuous improvement. Regularly testing and refining your plan ensures everyone knows what to do when an incident occurs. A well-prepared plan not only protects your business but also helps you recover faster.
Start refining your plan today to stay ahead of potential threats and keep your business secure.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox

