How IT Asset Management Helps Monitor Pirated Software Usage
Monitor pirated software with IT Asset Management to protect your business from security threats, legal risks, and compliance issues.
Software piracy is the use of software that hasn’t been properly licensed. This can involve downloading cracked versions from the internet, sharing a single license key across multiple devices, or installing programs that the company has never officially authorized.
It often happens in workplaces for simple reasons. Some employees may want to avoid delays from procurement. Others might think using a “free” version won’t cause harm. In some cases, it’s simply a lack of awareness about policies or the associated risks.
Even if the intent isn’t malicious, pirated software puts the entire organization at risk. Understanding what it looks like is the first step toward keeping systems safe and compliant.
What is software piracy?
Software piracy is the use of software without a proper license from the vendor. This directly violates software license management practices, which are designed to ensure every installation is legal and properly tracked.
It happens in different ways:
- Cracked versions: downloading modified copies that bypass license checks.
- Shared keys: using the same license on more devices than allowed.
- Unauthorized installs: employees adding tools that the company has not purchased.
- Counterfeit copies: buying cheap versions from unverified sellers that turn out to be illegal.
In many cases, people do not set out to break the rules. They might think it saves time or money, or they may not realize the software is pirated. But intentional or not, it creates serious risks for the business, from security threats to compliance violations.
The Risks of Pirated Software in the Workplace
Using pirated software in the workplace introduces significant risks that can impact an organization’s operations, finances, security, and reputation.
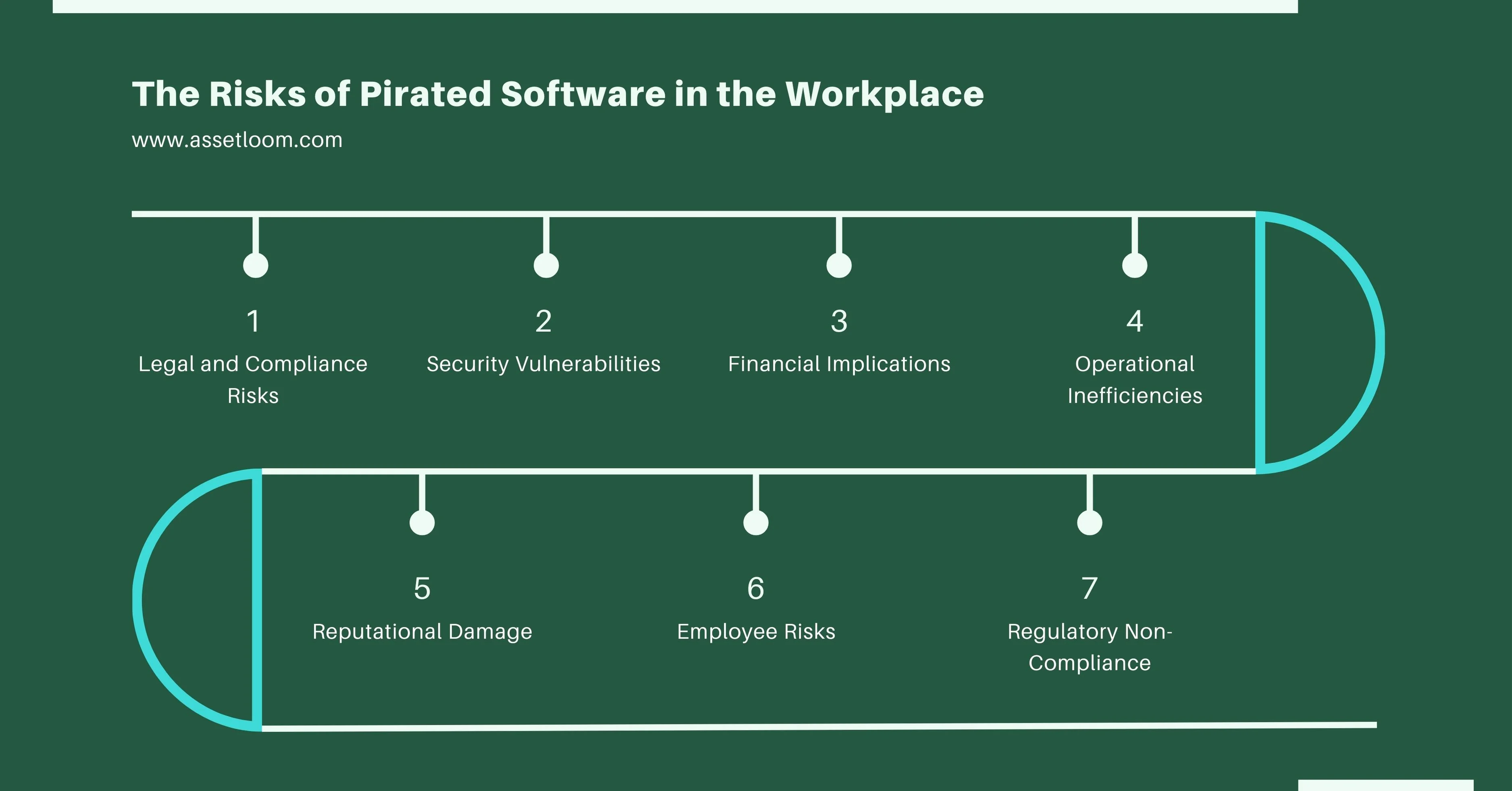
1. Legal and Compliance Risks
- Intellectual Property Violations: Pirated software infringes on copyright laws, as it is used without a valid license from the software vendor.
- Consequences:
- Fines and Penalties: Organizations may face hefty fines from software vendors or regulatory bodies. For example, the Business Software Alliance (BSA) can impose penalties of up to $150,000 per instance of pirated software in the U.S.
- Lawsuits: Vendors may pursue legal action, leading to costly litigation and settlements.
- Audits: Software vendors conduct audits, and non-compliance can result in public exposure and financial penalties.
- Example: A company using unlicensed copies of Microsoft Office could face a vendor audit, resulting in fines and mandatory purchase of legitimate licenses.
2. Security Vulnerabilities
- Malware and Viruses: Pirated software often comes from untrustworthy sources and may be embedded with malware, ransomware, or spyware.
- Consequences:
- Data Breaches: Malicious code in pirated software can compromise sensitive company data, leading to breaches that expose customer or employee information.
- System Compromise: Pirated software can serve as an entry point for hackers to infiltrate networks, leading to widespread cyberattacks.
- Lack of Updates: Pirated software typically cannot receive official patches or updates, leaving systems vulnerable to known exploits.
- Example: A pirated version of a design tool might contain a Trojan horse that allows hackers to steal proprietary designs or intellectual property.
3. Financial Implications
- Unexpected Costs: While pirated software may seem cost-free initially, the long-term financial impact can be significant.
- Consequences:
- Legal Fines: As mentioned, non-compliance penalties can be substantial.
- Remediation Costs: Addressing security breaches caused by pirated software requires investment in cybersecurity measures, data recovery, and system repairs.
- Lost Productivity: Downtime from malware infections or system failures disrupts business operations, leading to revenue loss.
- Example: A company hit by ransomware from pirated software may need to pay for data recovery services and face operational downtime, costing thousands or more.
4. Operational Inefficiencies
- Software Instability: Pirated software is often modified or cracked, leading to instability, crashes, or compatibility issues.
- Consequences:
- Reduced Productivity: Employees may experience frequent software failures, slowing down workflows.
- Incompatibility: Pirated software may not integrate well with other legitimate tools, causing delays or errors in collaborative projects.
- Lack of Support: Unlike licensed software, pirated versions do not come with vendor support, leaving IT teams to troubleshoot issues independently.
- Example: A pirated project management tool might crash during a critical deadline, delaying project delivery and frustrating team members.
5. Reputational Damage
- Loss of Trust: Using pirated software can tarnish an organization’s reputation if discovered by clients, partners, or the public.
- Consequences:
- Customer Loss: Clients may hesitate to work with a company known for unethical practices, such as software piracy.
- Negative Publicity: Media coverage of legal action or non-compliance can harm brand image.
- Partner Relationships: Business partners may sever ties with organizations that fail to adhere to legal and ethical standards.
- Example: A software development firm caught using pirated tools could lose credibility with clients who value intellectual property rights.
6. Employee Risks
- Unintentional Violations: Employees may unknowingly install pirated software, unaware of the risks or legal implications.
- Consequences:
- Disciplinary Actions: Employees may face internal repercussions for violating company policies.
- Security Breaches: Unvetted software installed by employees can introduce vulnerabilities, putting the entire organization at risk.
- Example: An employee downloading a pirated analytics tool from an unverified website might inadvertently install malware that spreads across the company network.
7. Regulatory Non-Compliance
- Industry Standards: Certain industries (e.g., finance, healthcare) have strict regulations requiring the use of licensed software to ensure data security and compliance.
- Consequences:
- Regulatory Fines: Non-compliance with regulations like GDPR, HIPAA, or PCI-DSS can lead to penalties.
- Loss of Certifications: Organizations may lose industry certifications if pirated software is detected during audits.
- Example: A healthcare provider using pirated software to manage patient records could violate HIPAA, leading to fines and loss of accreditation.
How ITAM Detects Pirated Software Usage
IT Asset Management (ITAM) systems are built to give companies a full view of their software landscape. By combining scanning, license tracking, and reporting, ITAM makes it easier to spot unlicensed or pirated programs. Here are the main ways it works:
1. Automated Software Discovery
- How it works: ITAM systems regularly scan company devices and networks to collect details about every installed program. This includes the software name, version, publisher, and installation date.
- How it detects piracy: If the scan finds software that isn’t part of the company’s approved list or doesn’t have a valid license, it gets flagged for review.
- Example: During a scan, ITAM might uncover a pirated version of AutoCAD on an employee’s laptop. The program doesn’t match the company’s license records, so the IT team can investigate before it becomes a bigger problem.
2. License Compliance Tracking
- How it works: ITAM keeps a central record of all purchased software licenses, including the number of seats, license keys, and usage rights. It then compares this data with the actual number of installations found across company devices.
- How it detects piracy: If more copies of a program are installed than the company has purchased, or if the license key is missing, duplicated, or invalid, ITAM flags it as a potential case of piracy.
- Example: A business buys 10 licenses of Microsoft Office. When ITAM runs a scan, it discovers 15 installations. The extra five copies could be pirated or unauthorized, and the IT team can step in to resolve the issue.
3. File and Source Verification
- How it works: AITAM tools check the authenticity of installed software by looking at digital signatures, checksums, and version details. Legitimate software usually comes with a verified signature from the vendor.
- How it detects piracy: Pirated or cracked programs often lack valid signatures or show signs of tampering in their files. If the source looks suspicious or the verification fails, ITAM flags the software for investigation.
- Example: An ITAM scan finds Adobe Photoshop on a workstation. Instead of a proper vendor certificate, the program has a missing or invalid signature. This signals that the copy could be pirated.
4. Integration with Security Tools
- How it works: ITAM can connect with endpoint protection systems, firewalls, and monitoring tools. This integration allows IT teams to see not just what software is installed, but also how it behaves on the network.
- How it detects piracy: Pirated programs often show unusual activity, like trying to bypass security settings or connecting to unsafe servers. When security tools flag this behavior, ITAM links it back to the specific software and device involved.
- Example: An employee installs a pirated video editing program. The software attempts to make unauthorized network connections. The endpoint security tool raises an alert, and through ITAM integration, the IT team can identify the software as pirated and remove it.
5. Reporting and Audit Trails
- How it works: ITAM creates detailed reports about software usage, installations, and license status. It also keeps audit trails that record when and where software was installed or removed.
- How it detects piracy: These reports make it easy to spot mismatches between what has been purchased and what is actually installed. Audit trails also help trace unauthorized installations back to a specific device or user.
- Example: An ITAM report shows VMware installed on several machines, but there is no record of the company buying licenses. The audit trail confirms the installations happened outside of the standard deployment process, pointing to possible piracy.
6. Policy Enforcement
- How it works: ITAM tools can enforce rules around software installation. This usually means requiring IT approval for new programs and blocking installs from unapproved sources.
- How it detects piracy: If someone tries to add software outside of the approved process, the system flags it right away. Since pirated software often comes from unofficial websites or cracked files, these rules help stop it before it spreads.
- Example: An employee tries to install a cracked version of a video editor they found online. The ITAM system blocks the installation attempt and alerts the IT team, preventing unlicensed software from entering the environment.
7. Monitoring Outdated Versions
- How it works: ITAM tracks the version and patch status of software across all company devices. It checks whether programs are receiving updates from the vendor.
- How it detects piracy: Pirated software often can’t connect to official update servers, leaving it stuck on old or unpatched versions. ITAM flags these outdated applications as potential piracy risks.
- Example: An ITAM scan shows several machines running an older build of Windows that hasn’t received updates in months. Because legitimate versions should update regularly, the system flags these installations for review.
8. Cross-Checking with Procurement Records
- How it works: ITAM connects with procurement and finance records to verify that every installed program has a matching purchase record.
- How it detects piracy: If software is found on a device but there’s no record of the company buying it, the installation is flagged as unlicensed and possibly pirated.
- Example: An ITAM scan finds Oracle Database installed on a server, but finance records show no purchase of that software. This mismatch points to a potential case of piracy that the IT team can investigate.
Using AssetLoom for software monitoring
An ITAM platform like AssetLoom gives companies a single place to monitor all software across their environment. Instead of relying on manual checks or scattered records, AssetLoom automates the process and provides clear visibility.
- Central dashboard: View all installed applications across devices in one place.
- License reconciliation: Compare software usage against purchased licenses to spot gaps or overuse.
- Real-time alerts: Get notified when unauthorized or unapproved software appears in the environment.
- Audit-ready reports: Generate compliance reports that simplify vendor audits and reduce risk.
- Integration with workflows: Fit monitoring into daily IT operations, making it easier to catch issues early.
By using AssetLoom, companies can move from reactive problem-solving to proactive monitoring, ensuring pirated or unlicensed software is identified before it causes legal, security, or operational problems.
5 tips to prevent pirated software in your company
Preventing the use of pirated software in your company is essential to avoid legal, security, and financial risks.
1. Establish a clear software policy
Create a written policy that outlines how software should be purchased, approved, and installed. Make sure all employees know the rules and understand that pirated software is not allowed under any circumstances.
2. Provide employee training
Many employees install pirated software without realizing the risks. Regular training sessions can explain the dangers, such as malware infections or legal fines, and guide staff on the right way to request new tools.
3. Run regular ITAM audits
Use IT Asset Management to perform routine scans of company devices. These audits help identify unauthorized software early and keep license records up to date.
4. Set up automated alerts
Configure ITAM systems to send alerts when new or unapproved software is installed. Quick notifications give IT teams the chance to act before problems spread.
5. Reclaim and reassign licenses
Avoid unnecessary purchases by reusing licenses from employees who leave or no longer need certain software. This reduces the temptation for teams to download cracked or free versions.
Conclusion
Pirated software is not just a minor shortcut. It creates real risks that affect security, compliance, and the overall stability of a business. From hidden malware to unexpected legal fines, the consequences often cost far more than a legitimate license would.
IT Asset Management gives companies the visibility they need to detect and prevent these issues. By scanning devices, tracking licenses, and flagging unauthorized programs, ITAM makes it easier to stay compliant and keep systems secure.
Combining ITAM practices with clear policies, regular audits, and employee training helps create a safer IT environment. With the right approach, organizations can reduce the risk of piracy and focus on running their operations without disruptions.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


