Network Discovery vs. Network Inventory: What’s the Difference?
Discover the key differences between network discovery and network inventory, why both are essential for IT asset management.
Teams often use “network discovery” and “network inventory” as if they were the same. They aren’t. Discovery finds what’s connected right now; inventory tracks those assets over time. Treat them as one and you get blind spots and audit pain. Pair them and you get a reliable map plus the context to manage it well.
This guide explains what each does, how they differ, and a practical way to run both together—without spreadsheets or guesswork.
What is Network Discovery?
Network discovery is the automated process of identifying devices, endpoints, and services communicating on your network. The goal is live visibility: who and what is present, right now.
How network discovery works
- Active probes: Ping, ARP scans, SNMP, SSH/WMI, and service banners identify device types and attributes.
- Passive listening: SPAN/TAP ports and flow data reveal devices that avoid pings or speak intermittently.
- Directory & cloud lookups: Enrich results via AD, mobile device management (MDM), hypervisors, and cloud control planes.
What you get
- A time-stamped snapshot of connected assets: endpoints, servers, network gear, IoT/OT, VMs, containers, and sometimes SaaS identities.
- Early warning of rogue or misconfigured devices.
- Security context: open ports, OS fingerprints, and where assets live on the network.
Use cases
- After a merger, reveal overlapping subnets and unknown devices.
- In healthcare, verify that clinical devices are visible and segmented.
- For remote-first teams, discover endpoints over VPN or ZTNA and check baseline controls.
Discovery answers: “What’s on the network right now, and what does it look like?”
What is Network Inventory?
Network inventory is the governed, continuously updated record of your hardware, software, ownership, configuration, cost, and lifecycle state.
What a good inventory contains
- Identity & ownership: asset ID, device name, owner/department, location, cost center.
- Technical data: model/serial, CPU/RAM, OS/version, installed software, license state, warranty, patch level.
- Lifecycle & compliance: procurement date, support status, EOL/EOS, risk rating, and links to tickets or changes.
Why it matters
- Operations: faster troubleshooting with details one click away.
- Compliance: verifiable software counts, encryption status, policy evidence.
- Financials: avoid overbuying, reclaim licenses, plan refresh with real numbers.
Inventory answers: “What do we own, who is responsible, and what is its current state across time?”
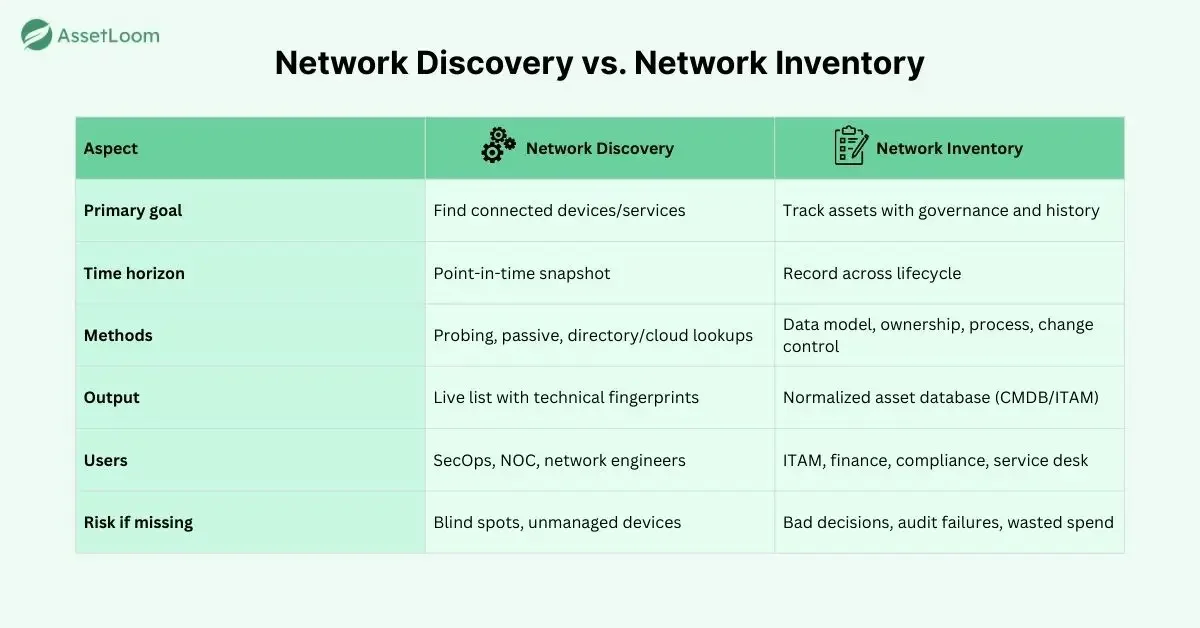
Network Discovery vs. Network Inventory
Discovery and inventory may sound similar, but their goals, processes, and outcomes are very different. Here’s a side-by-side look at what sets them apart.
How They Work Together
Discovery without inventory is noisy: you see devices but not ownership or policy status. Inventory without discovery gets stale: you miss new or silent assets. Tight coupling fixes both.
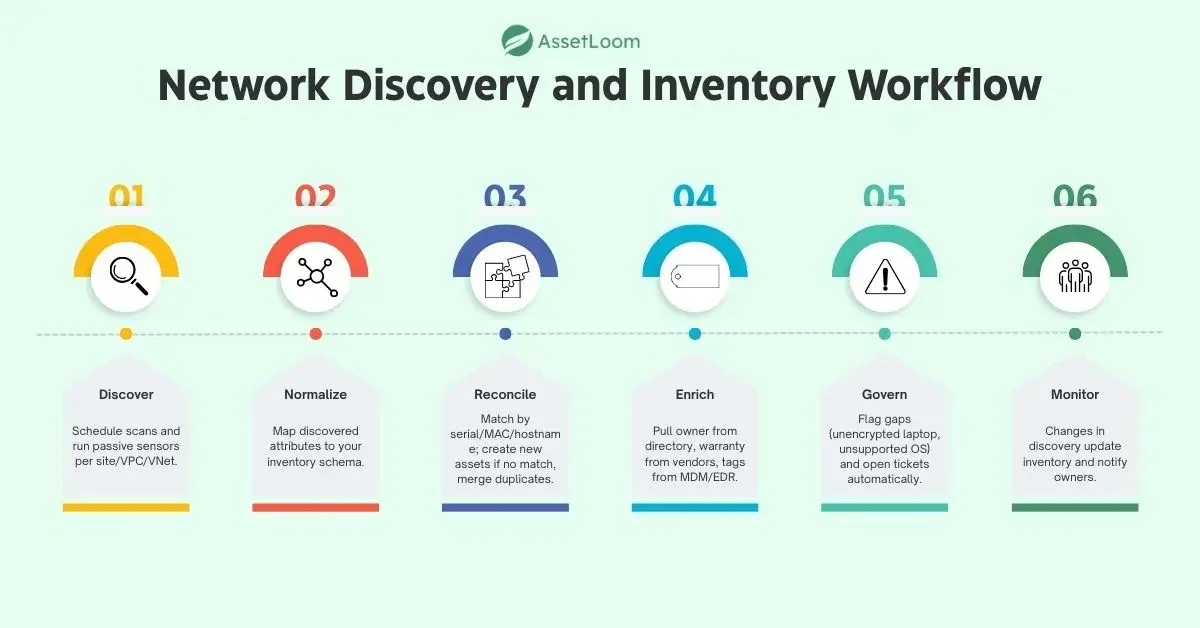
Practical flow
- Discover: Schedule scans and run passive sensors per site/VPC/VNet.
- Normalize: Map discovered attributes to your inventory schema.
- Reconcile: Match by serial/MAC/hostname; create new assets if no match, merge duplicates.
- Enrich: Pull owner from directory, warranty from vendors, tags from MDM/EDR.
- Govern: Flag gaps (unencrypted laptop, unsupported OS) and open tickets automatically.
- Monitor: Changes in discovery update inventory and notify owners.
When done well, discovery feeds your inventory with facts; inventory feeds teams with decisions.
Real-World Scenarios
University onboarding Thousands of devices hit Wi-Fi in days. Discovery identifies categories and quarantines unknown MACs. Inventory assigns owners when users authenticate; policy checks then grant access.
Hybrid cloud Discovery reads cloud APIs to find ephemeral VMs and containers. Inventory tracks owning team, cost tags, and expected lifetime. Drift reports show workloads that outlived their purpose.
Common Challenges of Network Discovery and Network Inventory
Even with the right tools, IT teams often run into challenges when managing discovery and inventory together. Here are some of the most common issues:
1. Shadow IT
Employees bring in personal devices or use unsanctioned cloud apps. These never make it into official inventory records but still interact with the network, creating security risks.
👉 Impact: Security blind spots, potential data leakage, and compliance failures. 👉 Fix: Continuous network discovery scan that flags new devices and auto-enrolls them into inventory for review.
2. Stale or Inaccurate Records
If inventory isn’t updated, it quickly becomes unreliable. For example, a server might be retired, but it still shows as “active” in the inventory, confusing audits and cost reports.
👉 Impact: Wasted license spending, failed audits, poor decision-making. 👉 Fix: Integrate discovery results with inventory so assets update automatically.
3. Duplicate Entries
When discovery and inventory tools don’t sync properly, the same device may appear multiple times under different names or identifiers.
👉 Impact: Inconsistent data, inflated asset counts, and wasted troubleshooting time. 👉 Fix: Set reconciliation rules (like matching by MAC address + serial number) to merge duplicates.
4. Fragmented Environments
Modern IT isn’t just on-premises anymore, it includes cloud, remote work, IoT, and SaaS platforms. Many discovery tools only scan the local network, leaving gaps.
👉 Impact: Partial visibility, especially for remote or hybrid setups. 👉 Fix: Use discovery tools that support hybrid and multi-cloud, and ensure inventory can handle both physical and virtual assets.
5. Compliance Pressure
Regulatory frameworks (HIPAA, PCI DSS, GDPR, ISO) often require complete and accurate asset records. Discovery without inventory won’t satisfy auditors, and inventory without discovery may miss unauthorized devices.
👉 Impact: Audit failures, fines, and reputational damage. 👉 Fix: Automate compliance reporting from inventory, powered by real-time discovery data.
6. Resource Overhead
Discovery scans can be resource-intensive if not managed carefully. Too frequent scans may overload networks; too infrequent scans leave blind spots.
👉 Impact: Network slowdowns or missed device activity. 👉 Fix: Balance frequency—e.g., daily scans for dynamic networks, weekly for stable environments, plus passive monitoring.
Frequently Asked Questions (FAQs)
1. Is network discovery the same as a vulnerability scan?
No. A vulnerability scan checks for weaknesses, missing patches, or misconfigurations. Network discovery simply identifies what devices exist on the network, regardless of whether they’re secure.
2. Do I need both network discovery and network inventory?
Yes. Discovery helps you spot what’s connected right now, while inventory helps you manage those assets over time. Using only one creates blind spots.
3. How often should I run network discovery?
It depends on your environment. Dynamic networks with lots of remote workers or IoT devices may need daily or continuous scans, while more stable environments may only need weekly scans.
4. What happens if devices don’t show up in discovery?
This usually means they’re powered off, hidden behind firewalls, or using unapproved connections. Continuous discovery methods or agent-based tools can help fill those gaps.
5. Can spreadsheets be used as a network inventory?
Technically yes, but they don’t scale well. Spreadsheets often become outdated, error-prone, and hard to reconcile with real-time discovery data. Automated inventory tools are much more reliable.
6. How does cloud computing change network discovery and inventory?
Cloud resources like VMs, containers, and SaaS apps spin up and down quickly. Discovery tools need API integrations with cloud platforms, while inventory must handle short-lived assets and cost tracking.
7. What’s the link between network inventory and compliance?
Auditors require accurate records of all assets, software, and configurations. Inventory provides this structured data, while discovery ensures no device is left undocumented.
8. Can network discovery impact performance?
If scans are too aggressive, they may cause minor slowdowns. Best practice is to schedule scans during off-peak hours and use passive monitoring to reduce load.
9. How does AssetLoom help with discovery and inventory?
AssetLoom integrates both processes in one platform—discovery automatically feeds into inventory management, ensuring you always have accurate, real-time asset records for better visibility, compliance, and cost control.
Conclusion
Network discovery and network inventory are complementary. Discovery provides live visibility; inventory provides durable truth. Link them with clear rules, automate the handoff, and measure accuracy. You’ll catch unknown devices faster, answer audit questions with confidence, and make smarter budget calls.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


