Key NIS2 Requirements for Asset Management: A Guide for IT Leaders
Key NIS2 requirements for asset management highlight how IT leaders can ensure compliance, address challenges, and strengthen cybersecurity with effective tools and practices.
As an IT leader, you're likely familiar with the growing challenges of keeping your organization's systems secure. Every day, new threats arise, and the pressure to stay ahead of them never stops. At the same time, regulations are becoming stricter. One of the most important of these is the NIS2 Directive, which requires businesses to meet specific cybersecurity standards to protect critical infrastructure.
One area where many organizations struggle is IT asset management. Often, it’s not until a security breach or audit occurs that people realize the importance of knowing exactly what assets they have and how they're managed. NIS2 places a significant emphasis on asset management because knowing your assets is crucial to protecting them and mitigating risks.
What is NIS2 and Why It Matters for Asset Management
NIS2, or the Network and Information Systems Directive 2, is a set of rules introduced by the European Union to strengthen the cybersecurity of essential services and critical infrastructure across member states. Its main goal is to improve resilience against cyberattacks, especially as the digital world becomes more interconnected.
The directive focuses on organizations that provide essential services such as energy, transport, banking, and healthcare, as well as digital service providers. However, its scope extends beyond these sectors. If your organization handles sensitive information or provides critical services, you may be required to comply.
For IT leaders, the NIS2 Directive highlights the importance of asset management. Why? Without knowing exactly what assets you own and manage, it’s impossible to ensure their security. NIS2 requires organizations to track and manage their assets in a way that reduces vulnerabilities, ensures quick recovery after incidents, and makes it easier to implement preventive measures.
For example, imagine your company relies on a specific piece of software to process payments. If you don’t have proper tracking for this software, you might miss important security patches. This could leave your organization vulnerable to a cyberattack, and it would be harder to recover if something goes wrong. By keeping track of the software, knowing its status, and having an updated list of assets, you’ll be better equipped to manage these risks.
In simple terms, asset management helps organizations identify what they have, where it’s located, how it’s used, and how to protect it. NIS2 makes sure that asset management is integrated into every part of an organization’s cybersecurity strategy, which is why it’s a critical part of compliance.
Key NIS2 Requirements Relevant to Asset Management
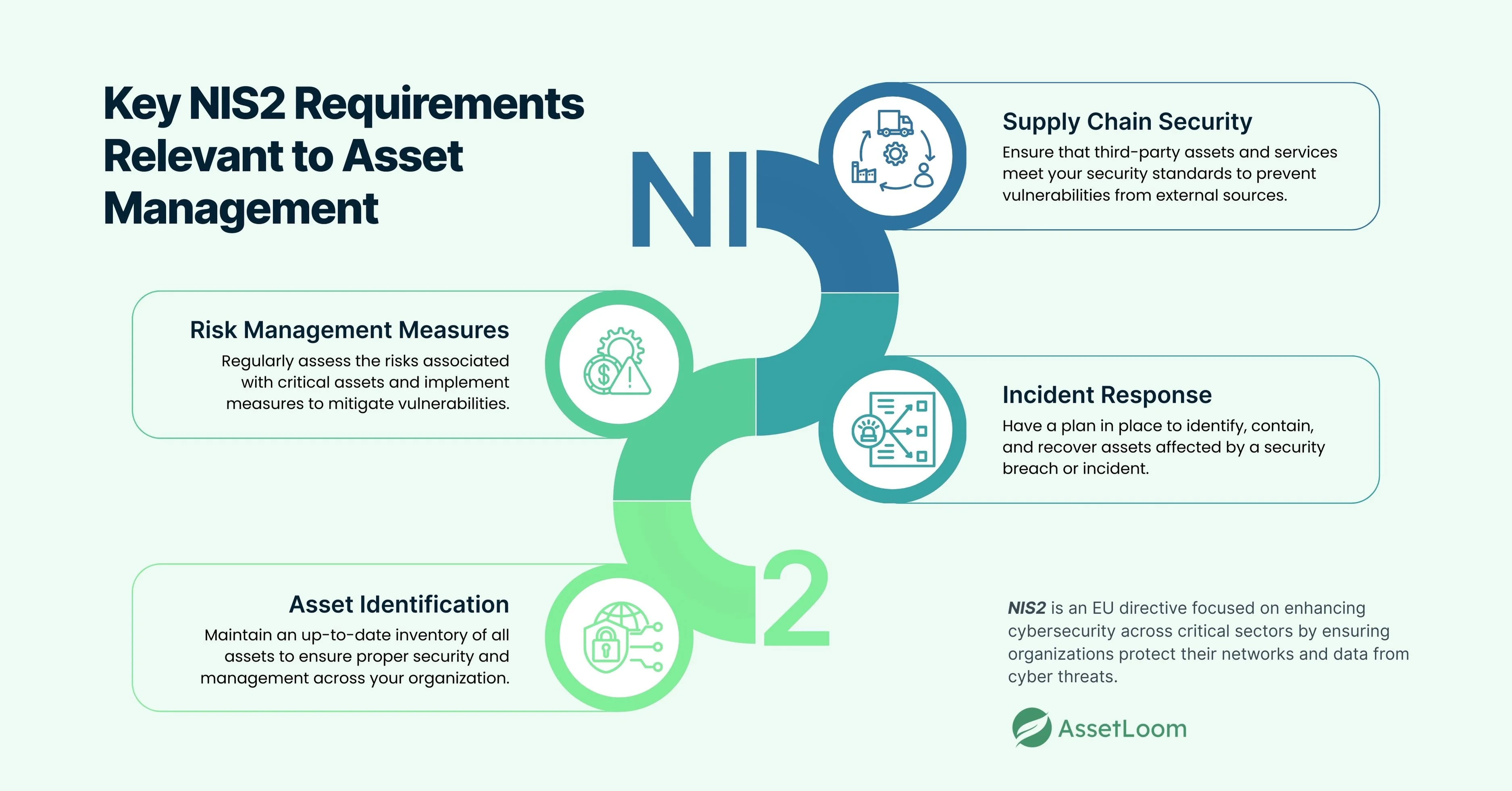
The NIS2 Directive includes several key requirements that directly impact asset management within your organization. As an IT leader, understanding these requirements will help you align your asset management strategy with the NIS2 guidelines, ensuring compliance and enhancing your cybersecurity posture. Below are some of the most relevant NIS2 requirements and how they relate to managing your assets:
1. Risk Management Measures
One of the most important aspects of NIS2 is its focus on risk management. The directive requires organizations to assess their cybersecurity risks regularly and take appropriate measures to manage them. This includes identifying critical assets and evaluating their potential risks.
For asset management, this means ensuring that all assets are tracked and assessed for vulnerabilities. Knowing which assets are critical to your operations and understanding their potential risks is key to protecting them effectively.
Example: If your company relies on a specific server for processing transactions, it’s vital to identify the risks associated with that server and take steps to mitigate these risks, like applying patches or replacing outdated hardware.
2. Security of Network and Information Systems
NIS2 also requires organizations to ensure the security of their network and information systems. Asset management plays a significant role here, as it involves securing and protecting all assets within your network. You need to know what devices are connected to your network, where they’re located, and what software is running on them.
By tracking these assets, you can apply necessary security updates and configurations, monitor for potential vulnerabilities, and protect your organization from cyber threats.
Example: Let’s say your organization uses several remote devices to access sensitive data. It’s crucial to know the status of these devices—whether they have up-to-date security software or if any are running outdated operating systems. Without proper asset tracking, it’s easy to overlook vulnerabilities that could lead to a breach.
3. Incident Response
Incident response is another key requirement in NIS2. The directive emphasizes the importance of having an effective plan in place to respond to security incidents. This includes quickly identifying which assets are affected by an attack and how to recover them.
Asset management ensures that when an incident occurs, your team can easily locate the affected assets, determine their status, and initiate recovery procedures. This helps reduce downtime and limits the damage caused by incidents.
Example: Imagine a cyberattack on your company’s database server. If you’ve been tracking your assets, you’ll know exactly which server was compromised, which data it holds, and how to disconnect it from the network quickly to prevent further damage. Asset management allows you to respond efficiently and recover faster.
Read also: 8 Tips to Manage an Effective Incident Response Plan for Enterprise Cloud Security
4. Supply Chain Security
NIS2 also stresses the importance of supply chain security. As organizations increasingly rely on third-party vendors for critical services or products, ensuring the security of assets within the supply chain becomes crucial.
Asset management ensures that you have visibility into your organization’s assets, including those provided by external vendors. This can help identify potential vulnerabilities in your supply chain and make sure that third-party assets meet your security standards.
Example: If a vendor provides software that integrates with your internal systems, asset management helps you track its version, updates, and any known security vulnerabilities. By keeping an eye on this asset, you can ensure it doesn’t introduce security risks into your organization.
Key Components of Asset Management for NIS2 Compliance
To meet the NIS2 requirements, effective asset management is essential. But what exactly does this look like in practice? Several key components form the foundation of asset management, ensuring that your organization is both secure and compliant with the directive. Below are the critical elements that IT leaders should focus on to align their asset management strategy with NIS2:
1. Inventory Management
The first and most fundamental component of asset management is maintaining an accurate and up-to-date inventory of all assets. This includes physical devices, software, and even data. NIS2 requires organizations to know what assets they have, where they’re located, and how they’re used.
Why It’s Important for NIS2: Without a clear inventory, you can’t ensure that all critical assets are properly protected. For NIS2 compliance, you must track each asset’s status and assess its potential risks.
Example: If your company uses a variety of laptops, servers, and mobile devices, it’s essential to keep a record of each one, including information such as serial numbers, locations, operating systems, and software versions. This enables you to quickly identify and address any vulnerabilities or risks associated with these devices.
Read also: IT Inventory Management: Best Practices for IT, Finance, Security
2. Asset Classification
Not all assets are equally important or vulnerable. NIS2 requires organizations to classify their assets based on their criticality to the business. This means that some assets, such as servers storing sensitive data, will require more stringent security measures than less critical assets.
Why It’s Important for NIS2: Properly classifying assets allows you to prioritize your cybersecurity efforts. By identifying which assets are most crucial, you can allocate resources more effectively to protect them.
Example: You may classify your company’s financial database as a high-priority asset that requires stronger security controls and frequent monitoring. In contrast, an office printer may be classified as a lower priority and require less attention in terms of security.
3. Monitoring & Maintenance
Once your assets are tracked and classified, the next step is to continuously monitor and maintain them. This includes ensuring that software is updated, security patches are applied, and hardware is in good working condition. NIS2 emphasizes the need for organizations to regularly monitor their assets to prevent vulnerabilities from being exploited.
Why It’s Important for NIS2: Ongoing monitoring ensures that your assets are always protected. It helps you identify issues early on, ensuring that risks are mitigated before they turn into major problems.
Example: Regularly checking the status of your network’s firewalls or updating antivirus software across your company’s devices ensures that you stay ahead of potential threats. Monitoring also helps identify which assets need maintenance or replacement before they fail.
Read also: Difference Between Machine Maintenance Software and ITAM Software
4. Audit Trails & Documentation
One of the NIS2 requirements is to have a well-documented process for asset management. This includes keeping audit trails of all asset-related activities—whether it’s the addition of new assets, changes in configuration, or maintenance actions. Proper documentation is essential for audits and regulatory checks.
Why It’s Important for NIS2: Audit trails help demonstrate that your organization is meeting the NIS2 requirements. They provide proof that assets are being properly managed, monitored, and maintained, which can be invaluable in the event of a security breach or audit.
Example: If your company replaces an old server, maintaining detailed records of the asset’s removal and replacement ensures that you have a clear history of changes. This documentation can be used to verify that all actions were in line with your cybersecurity policies.
Best Practices for IT Leaders
- Automate Asset Discovery and Tracking: Use automated tools to track all assets in real time, ensuring accuracy and reducing manual effort.
- Implement a Centralized Asset Management System: Store all asset data in a single platform for easy access and efficient management.
- Regularly Train and Educate Employees: Provide ongoing training to ensure staff understand asset management practices and NIS2 compliance.
- Conduct Regular Audits and Reviews: Perform periodic audits to verify that assets are accurately recorded and that security measures are up to date.
- Ensure Continuous Monitoring and Updates: Continuously monitor assets and apply security updates to keep them secure and compliant.
Challenges IT Leaders May Face
Complexity of Multi-Asset Environments
Managing diverse assets, such as physical devices, software, and cloud infrastructure, can be overwhelming. In large organizations, these assets may be spread across multiple departments and locations, making it difficult to maintain visibility and control.
How AssetLoom helps: AssetLoom provides a centralized platform for tracking and managing all types of assets in real time. Whether assets are physical or cloud-based, AssetLoom consolidates them into one easy-to-use interface, giving IT teams full visibility and control over all assets, no matter how complex the environment.
Resource Limitations
IT teams are often stretched thin due to time and budget constraints. Implementing an asset management system that meets NIS2 compliance standards can seem like a daunting task with limited resources.
How AssetLoom helps: AssetLoom automates key asset management tasks, such as asset discovery and tracking, significantly reducing the manual workload on IT teams. This automation saves time, improves efficiency, and reduces the need for additional resources, making compliance more manageable within budget constraints.
Coordination Across Teams
Asset management requires collaboration between multiple departments, including IT, procurement, and security. Ensuring everyone is aligned and following the same asset management processes can be challenging.
How AssetLoom helps: AssetLoom provides a unified system that can be accessed by various departments, ensuring that everyone is on the same page. With role-based access controls and real-time updates, teams can collaborate more effectively and ensure asset management processes are consistently followed across the organization.
Maintaining Accurate and Up-to-Date Data
As assets change, get replaced, or are updated, keeping records accurate and current can be difficult. Outdated or incomplete asset data can lead to compliance gaps and increased risk.
How AssetLoom helps: AssetLoom offers real-time asset tracking and automatic updates, ensuring that asset data is always accurate and up-to-date. The platform continuously monitors asset status, making it easy to track changes and maintain accurate records in line with NIS2 requirements.
Conclusion
NIS2 compliance is essential for safeguarding your organization’s cybersecurity. Effective asset management is key to meeting these requirements, providing the visibility and control necessary to reduce risks.
While challenges exist, tools like AssetLoom simplify the process by automating asset discovery, centralizing management, and ensuring accurate records. By adopting these practices, IT leaders can streamline compliance, enhance security, and better protect critical assets.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


