Cloud-Based User Provisioning: Processes, Types, and Best Practices
Discover cloud-based user provisioning, its types, processes, and best practices to streamline IT access management and boost security.
Managing user access has become a constant pain for IT teams. Onboarding new employees, updating permissions, and removing accounts when people leave - these tasks pile up fast. Manual processes make it worse: slow onboarding, costly mistakes, and security gaps.
As companies move to the cloud and adopt dozens of SaaS apps, the challenge only grows. That’s why cloud-based user provisioning is now essential. It automates the entire process, reducing errors, improving compliance, and saving valuable time. Combined with IT Asset Management (ITAM), it gives IT teams a clear view of users, assets, and access in one place.
This guide explains what user provisioning is, why it matters, how it works in the cloud era, and the best practices to get it right.
What is User Provisioning?
User provisioning is the process of giving employees access to the tools and systems they need to do their jobs and removing that access when they no longer need it. It starts when someone joins the company and continues through role changes, promotions, or project shifts, all the way to when they leave.
Here’s what that looks like in practice: A new sales rep joins your team. They require an email account, access to the CRM, and permissions for communication tools such as Slack. If that rep moves to marketing, their sales access should be removed and marketing tools added. And when they leave the company, every account needs to be shut down quickly.
User provisioning isn’t just about handing out login credentials. It often involves integrating with identity systems, applying security policies, and ensuring role-based access control (RBAC) so employees only get the permissions they need. It also includes periodic reviews to confirm access is still appropriate, a critical step for security and compliance.
As businesses move to cloud environments and adopt dozens of SaaS apps, this process becomes harder to manage manually. That’s where cloud-based user provisioning comes in.
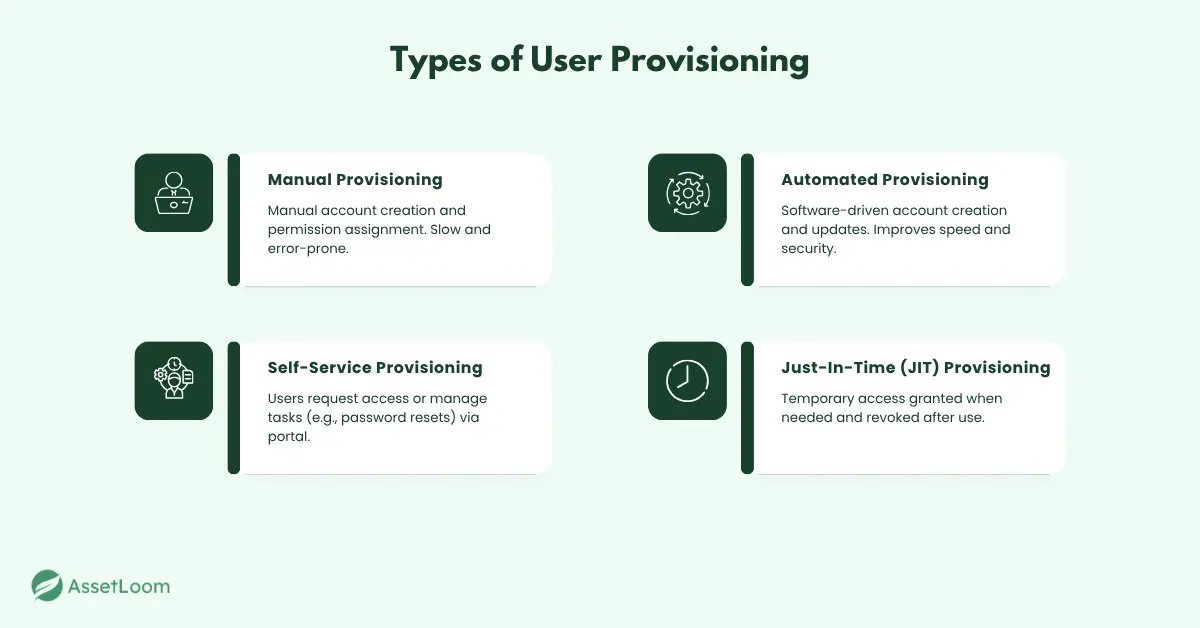
Types of User Provisioning
User provisioning can take different forms, depending on how access is managed. Here are the main types:
- Manual Provisioning: IT teams create accounts and assign permissions manually. While simple for small setups, it’s slow and error-prone as the number of users and applications increases.
- Automated Provisioning: Uses software or identity management tools to handle account creation, updates, and removal based on predefined rules. This improves speed, accuracy, and security.
- Self-Service Provisioning: Allows users to request access or manage basic tasks - like password resets - through a portal, often with automated approvals. It reduces IT workload but requires strong controls.
- Just-In-Time (JIT) Provisioning: Grants temporary access only when needed and revokes it immediately after. This approach is common in cloud environments to minimize standing privileges and reduce risk.
Organizations often combine these methods to balance convenience, security, and compliance. Next, let’s look at how the cloud-based user provisioning process works.
The Cloud-Based User Provisioning Process
Cloud-based user provisioning is more than just automation. It’s about securing access and scaling efficiently across the entire user lifecycle. Here’s how the process works and why it matters:
- User Onboarding: When a new hire is added in an HR or identity system, the provisioning tool automatically creates accounts across required applications, including email, collaboration platforms, CRM, and more. This speeds up onboarding and reduces IT workload.
- Role-Based Access Control (RBAC): Access rights are assigned based on predefined roles, ensuring employees only get permissions relevant to their job. This enforces the principle of least privilege and minimizes cloud security risks.
- Role Changes and Updates: When employees switch roles or get promoted, the system removes old permissions and applies new ones automatically. This prevents delays and avoids over-provisioning.
- Automated De-Provisioning: Offboarding is critical for security. The system revokes all accounts immediately when an employee leaves, eliminating orphaned accounts that attackers could exploit.
- Continuous Monitoring and Auditing: Every change is logged, and reports highlight unused accounts, privilege creep, or policy violations, helping businesses stay compliant with standards like SOC 2, ISO 27001, and GDPR.
This streamlined process not only saves time but also strengthens security, reduces errors, and ensures compliance in dynamic cloud environments.
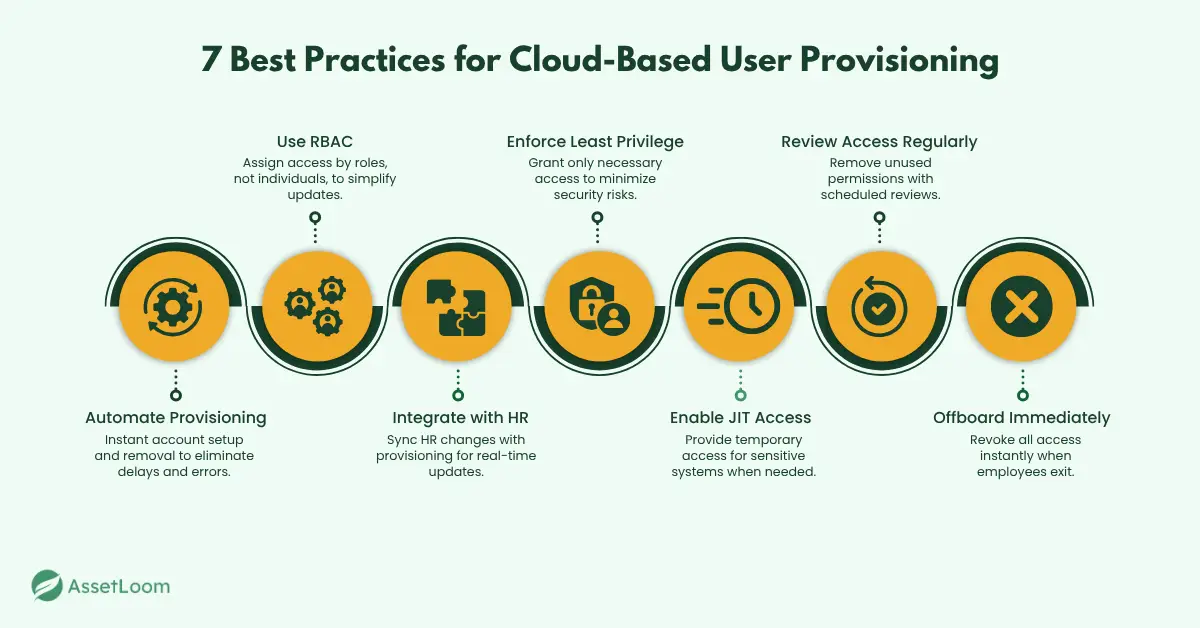
Best Practices for Cloud-Based User Provisioning
Cloud-based user provisioning is about more than automation. It is about creating a secure, efficient process that scales with your business. Here are seven best practices you can apply right away:
1. Automate End-to-End Provisioning
Manual account setup causes delays, mistakes, and security risks. Automating the full lifecycle ensures accounts are created instantly, permissions are updated accurately, and access is revoked when someone leaves. For example, when HR adds a new hire, automation can set up email, chat tools, and CRM access immediately.
Pro Tip: Pick a tool that integrates with HR and identity systems for seamless workflows.
Read also: Application Management in the Age of AI and Automation
2. Implement Role-Based Access Control (RBAC)
Assigning permissions one by one wastes time and increases errors. With RBAC, you define roles like Sales or HR and assign access based on those roles. When an employee changes roles, updating their access is as simple as switching their role in the system.
Pro Tip: Review and update roles regularly as your organization grows.
3. Integrate with Your HR System
HR is the first to know when someone is hired, promoted, or exits. Linking your HR system to your provisioning tool ensures access changes happen immediately and automatically. No delays, no forgotten accounts.
Pro Tip: Use HR as the single source of truth for employee data.
4. Apply the Principle of Least Privilege
Give users only the access they need, nothing more. Avoid giving blanket admin rights unless absolutely necessary. For critical applications, use approval workflows to keep control tight.
Pro Tip: Pair least privilege with regular reviews to stop privilege creep.
5. Use Just-In-Time (JIT) Access for High-Risk Systems
Permanent access to sensitive systems is dangerous. JIT grants temporary access only when needed and removes it automatically afterward. This greatly reduces insider threats and credential misuse.
Pro Tip: Always set expiration times on temporary access.
6. Conduct Regular Access Reviews
Permissions can become outdated quickly. Schedule monthly or quarterly reviews to find unused accounts and unnecessary permissions. Automated reporting from your provisioning tool makes this easy and helps with compliance audits.
Pro Tip: Involve department managers as they know what access their teams really need.
7. Make Offboarding Immediate and Complete
When an employee leaves, access should be removed right away. Orphaned accounts are one of the biggest security risks. Automation ensures nothing is left behind.
Pro Tip: Add automated app deactivation to your offboarding workflow.
Conclusion
User provisioning may seem like a small part of IT operations, but it has a huge impact on security, compliance, and productivity. As businesses move deeper into cloud environments and adopt more SaaS tools, manual processes simply cannot keep up.
Cloud-based user provisioning changes the game. It speeds up onboarding, enforces security policies, and ensures access is always accurate. By automating the user lifecycle, applying role-based access, and regularly reviewing permissions, organizations can reduce risk while improving efficiency.
The goal is simple: make sure the right people have the right access at the right time, and no more. Following the best practices in this guide will help you achieve that with confidence.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox

