10 Cloud Security Risks Every Business Must Know
Discover 10 critical cloud security risks like misconfigurations and weak access controls, and learn practical steps to mitigate them.
In an increasingly connected world, cloud computing has become the foundation of digital transformation. Businesses of all sizes are migrating to the cloud to improve flexibility, reduce costs, and enable remote work. But while the cloud delivers powerful advantages, it also brings new challenges, and cloud security risks are among the most critical.
Whether you're running a small startup or managing an enterprise-level IT infrastructure, understanding cloud security risks is essential. In this article, we'll walk through 10 key threats you should know about. We'll explain them in simple terms, give real-world examples, and share practical tips for staying secure.
What Are Cloud Security Risks?
Cloud security risks are vulnerabilities or threats in cloud computing environments that could lead to data breaches, unauthorized access, service disruptions, or compliance violations. These risks stem from technical missteps, human errors, and sophisticated cyberattacks. By identifying and addressing these risks, businesses can safeguard sensitive information and maintain trust with their customers.
10 Cloud Security Risks You Must Know
Let’s explore 10 critical cloud security risks and practical steps to mitigate them.
1. Misconfigured Cloud Settings
One of the most frequent causes of cloud data breaches is misconfiguration. This happens when cloud resources, like databases or storage buckets, are not properly secured.
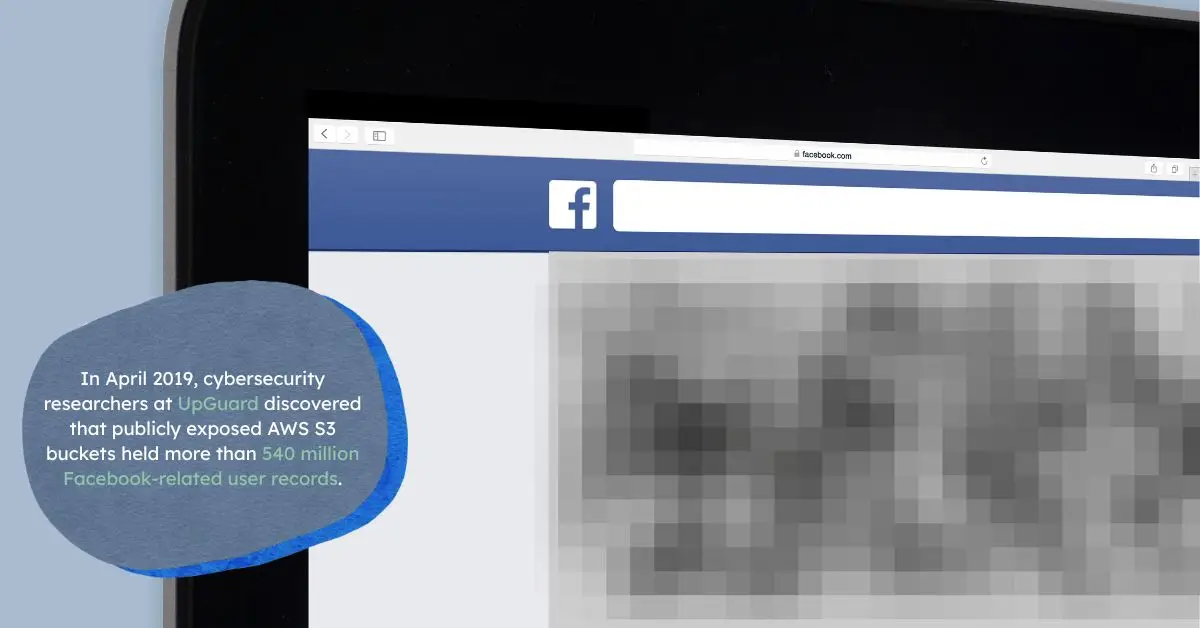
Cloud platforms like AWS, Microsoft Azure, and Google Cloud provide powerful tools with complex settings. A single oversight, such as leaving a storage bucket publicly accessible, can expose sensitive data to anyone on the internet. For example, in 2019, a misconfigured AWS S3 bucket exposed millions of Facebook user records, highlighting the dangers of improper settings.
To mitigate this risk, businesses should use automated configuration management tools to detect and fix errors. Regular audits of cloud settings and adopting best practices, such as disabling public access by default, can prevent costly mistakes.
Read more: Cloud Security Posture Management
2. Weak Identity and Access Management (IAM)
If too many users have access to sensitive data or systems, the chances of a breach increase. Access controls help manage who can view or change specific information.
Weak IAM practices are a significant cloud security risk. If users have overly broad permissions, weak passwords, or no multi-factor authentication (MFA), attackers can easily compromise accounts. For instance, an employee reusing a password across multiple platforms could inadvertently provide hackers with access to critical cloud systems.
To address this, organizations should enforce strong password policies, enable MFA for all users, and follow the principle of least privilege, ensuring employees only access the resources necessary for their roles. Regularly reviewing and updating permissions can further reduce this risk.
3. Inadequate Data Encryption
Encryption is a cornerstone of cloud security, but inadequate or inconsistent encryption practices can leave data vulnerable. If data is not encrypted during transit or at rest, attackers can intercept or steal it. Some organizations rely solely on their cloud provider’s default encryption, which may not meet specific compliance or security needs.
To mitigate this cloud security risk, businesses should implement end-to-end encryption using strong protocols like AES-256. Encryption keys should be managed securely, rotated regularly, and stored separately from the data they protect. Consulting with cloud providers to understand their encryption offerings can also ensure robust protection.
4. Insider Threats
Not all threats come from hackers. Sometimes the risk comes from within the organization, employees, contractors, or partners who misuse their access. A former employee who still has access credentials downloads sensitive files before leaving the company.
What to do: Immediately revoke access for departing staff. Monitor user behavior and establish clear policies for acceptable use.
5. Insufficient Data Backup and Recovery
Data loss, whether from cyberattacks, accidental deletions, or hardware failures, is a significant cloud security risk. Many organizations assume their cloud provider handles all backups, but most operate under a shared responsibility model, meaning customers must configure and manage their own backups. Without a robust backup plan, recovering from a ransomware attack or system failure can be challenging.
To address this, businesses should implement automated, regular backups and store them in secure, separate locations. Testing recovery processes periodically ensures data can be restored quickly and accurately, minimizing downtime and losses.
6. Third-Party Vendor Vulnerabilities
Many businesses rely on third-party vendors for cloud-based services, such as SaaS applications or managed cloud solutions. However, these vendors can introduce cloud security risks if their security practices are weak. A breach at a third-party provider could compromise your organization’s data, even if your internal systems are secure. For instance, a supply chain attack targeting a vendor could ripple through to your cloud environment.
To mitigate this risk, thoroughly vet third-party vendors by reviewing their security certifications, compliance standards, and incident response plans. Contracts should clearly define security responsibilities, and businesses should monitor vendor performance to ensure ongoing compliance.
7. Sophisticated Cyber Threats
The evolving nature of cyberattacks, such as ransomware, phishing, and distributed denial-of-service (DDoS) attacks, poses significant cloud security risks. Cybercriminals are increasingly targeting cloud environments with advanced techniques, such as exploiting unpatched vulnerabilities or using stolen credentials. For example, ransomware can encrypt cloud-stored data, rendering it inaccessible until a ransom is paid.
Organizations can protect against these threats by deploying cloud-native security tools, such as intrusion detection systems and anti-malware software. Keeping systems updated with the latest security patches and monitoring threat intelligence can help stay ahead of attackers.
8. Lack of Visibility and Monitoring
Without proper visibility into cloud activities, organizations may struggle to detect suspicious behavior or unauthorized access, increasing cloud security risks. For example, an attacker who gains access to a cloud account could exfiltrate data over time without being noticed if monitoring is inadequate.
To enhance visibility, businesses should deploy cloud-native monitoring tools that provide real-time insights into user activities, network traffic, and system changes. Setting up alerts for anomalies, such as unusual login locations or large data transfers, can help identify and respond to threats quickly.
9. Compliance and Regulatory Challenges
Cloud environments must adhere to industry-specific regulations, such as GDPR, HIPAA, or PCI-DSS. Non-compliance can result in legal penalties, reputational damage, and heightened cloud security risks. For example, storing sensitive customer data in a non-compliant cloud environment could lead to fines or lawsuits.
To address this, organizations should select cloud providers with certifications that align with their regulatory requirements. Conducting regular compliance audits, mapping data flows, and implementing controls to meet standards can help avoid violations and enhance security.
10. Misunderstanding the Shared Responsibility Model
A common cloud security risk stems from misunderstandings about the shared responsibility model. In this model, cloud providers secure the underlying infrastructure (e.g., servers, networks), while customers are responsible for securing their data, applications, and configurations. Failing to understand these responsibilities can lead to security gaps, such as unpatched applications or unsecured data.
Businesses should review their cloud provider’s shared responsibility model and clearly document their security obligations. Leveraging provider-supplied tools, such as security groups or encryption services, can help bridge gaps and ensure comprehensive protection.
Strategies to Mitigate Cloud Security Risks
To effectively manage cloud security risks, organizations should adopt a proactive, multi-layered approach. Here are actionable strategies to strengthen cloud security:
- Audit Configurations Regularly: Use automated tools to identify and fix misconfigurations in cloud settings. Schedule periodic audits to maintain compliance with security best practices.
- Strengthen Access Controls: Enforce MFA, strong passwords, and role-based access to limit unauthorized access.
- Encrypt Data Consistently: Implement end-to-end encryption for all sensitive data, using robust protocols and secure key management.
- Train Employees: Conduct regular training and simulations to educate staff on security threats and best practices.
- Implement Robust Backups: Set up automated backups and test recovery processes to ensure data availability after incidents.
- Vet Third-Party Vendors: Evaluate vendors’ security practices and include clear security terms in contracts.
- Deploy Advanced Security Tools: Use intrusion detection, anti-malware, and monitoring tools to protect against cyber threats.
- Monitor in Real-Time: Implement cloud-native monitoring to detect and respond to suspicious activities promptly.
- Ensure Compliance: Choose compliant cloud providers and conduct regular audits to meet regulatory requirements.
- Understand Responsibilities: Clarify the shared responsibility model and address all customer-side security tasks.
By implementing these strategies, businesses can significantly reduce their exposure to cloud security risks and build a secure, resilient cloud environment.
Learn more: Cloud Asset Management
Why Addressing Cloud Security Risks Is Critical
As cloud adoption grows, the impact of cloud security risks becomes more significant. A single breach can lead to financial losses, reputational harm, and regulatory penalties. For example, a 2021 study estimated that the average cost of a data breach was $4.24 million, with cloud-related breaches often involving higher costs due to their scale. By proactively addressing the 10 risks outlined above, organizations can protect their data, maintain customer trust, and ensure business continuity.
Moreover, strong cloud security practices demonstrate a commitment to safeguarding sensitive information, which can enhance a company’s reputation and competitiveness. Investing in cloud security is not just about preventing attacks; it’s about enabling long-term success in a digital-first world.
Bringing It All Together
Cloud computing is powerful, but it's not without its risks. These 10 cloud security risks show that security in the cloud isn't just about technology; it's about strategy, awareness, and continuous improvement.
By taking a proactive approach and understanding where the real risks lie, you can enjoy the full benefits of the cloud without compromising your data or systems. Remember, cloud security is a shared responsibility between cloud providers and users. Make sure you're doing your part.
If you're ready to take cloud security seriously, start with these fundamentals and build from there. Your data and your business will be better protected for it.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


