Verifying IT Asset Custody: What Every Business Needs to Know
Verifying IT asset custody boosts accountability, security, and compliance, while ITAM software like AssetLoom reduces risks of asset misuse and loss.
If you don’t properly verify the custody of your IT assets, you could face risks like data breaches, loss of critical information, or legal issues that could severely impact your business.
So, what does “asset custody” mean when it comes to IT Asset Management? In simple terms, IT asset custody refers to the management and protection of assets. Verifying the custody of these assets means ensuring they are properly accounted for, secured, and used according to your business’s needs.
What is IT Asset Custody?
IT asset custody refers to the management, protection, and responsibility of digital and technological assets within a business. These assets include both physical equipment, such as computers, servers, and networking devices, as well as intangible resources, including software licenses, cloud storage, and company data. The concept of custody means understanding who has control over these assets and ensuring they are properly maintained, tracked, and secured according to company policies.

In environments where assets are frequently allocated to different team members—such as laptops, software licenses, or mobile devices—it’s important to track who has possession of the asset, its condition, and how it’s being used. The Custody Verification feature helps ensure this by requiring users to confirm their possession and the condition of the assets assigned to them. This process is essential for maintaining accountability and ensuring that assets are properly handled, used, and maintained throughout their lifecycle, from allocation to disposal.
Example: Imagine your company issues laptops to employees for remote work. Each laptop is an IT asset that needs to be tracked. The "custody" of these laptops involves knowing which employee has each laptop, ensuring it is in good condition, and making sure it is being used appropriately for work purposes. If an employee’s laptop is damaged or lost, it must be reported, and the business must take responsibility for replacing or repairing it. This helps ensure that valuable equipment is not misused, misplaced, or underutilized.
Who Handles IT Asset Custody?
The responsibility of handling IT asset custody can vary depending on the type of asset and the size of the business. In general, it’s a shared responsibility between internal teams, external vendors, and sometimes even the employees themselves.
1. Internal IT Teams
For most businesses, internal IT teams or departments are the primary custodians of physical IT assets like computers, servers, and networking devices. These teams are responsible for keeping track of assets, ensuring they’re well-maintained, and overseeing their usage. They also play a role in managing software and hardware inventory, as well as performing regular updates and security checks.
2. External Vendors or Service Providers
In many cases, businesses rely on third-party vendors to handle more specialized IT assets, such as cloud storage, SaaS applications, or managed IT services. For instance, if your company uses a cloud service to store sensitive data, the cloud provider holds custody of that data, but you remain responsible for ensuring it is properly managed and protected. These external parties typically have access to your assets but must follow strict security protocols to ensure compliance and safety.
Read also: What is Vendor Management?
3. Employees
Employees are often given physical assets like laptops, mobile devices, or software licenses to do their work. While the company retains ownership, the employee is responsible for taking care of the asset while it’s in their possession. This includes ensuring the asset is used appropriately, reporting any issues or damage, and returning it when they no longer need it.
In short, IT asset custody is often a combination of shared responsibilities. While internal teams manage and track assets, external providers may be responsible for certain aspects, and employees are responsible for taking care of what’s assigned to them.
When to Use Custody
You should use IT asset custody whenever your business deals with valuable, movable, or critical digital or physical assets that are assigned to individuals or teams. This includes scenarios like:
- When assets are frequently assigned to employees, for example, laptops, mobile phones, or software licenses.
- When assets are shared across departments or teams, Like servers, network devices, or cloud services.
- During audits or regulatory checks, ensure assets are properly tracked for compliance.
- When assets require regular maintenance or servicing, this includes hardware repairs, software updates, and security patches.
- When assets are being returned or disposed of: For instance, when employees leave or when devices are being recycled or sold.
The Importance of Verifying Asset Custody
Verifying the custody of your IT assets is crucial for protecting your business and ensuring that your assets are well-managed and properly secured. Failing to verify custody can lead to significant risks, including loss, theft, security breaches, and legal complications.
1. Protect Against Fraud and Misuse
When IT assets are not properly tracked or verified, there’s a higher risk of misuse or fraud.
For example, employees might accidentally or intentionally misuse company devices, or assets like software licenses could be used without proper authorization. Regularly verifying the custody of your assets helps ensure that they are being used for their intended purpose and by the right individuals. It also helps identify missing or damaged assets, which could otherwise go unnoticed and cause major operational disruptions.
2. Minimize Security Risks
IT assets, especially sensitive data and critical hardware, are prime targets for cyber threats. If custody isn’t verified, you may not be aware of unmonitored assets or devices that are vulnerable to security breaches. For example, an employee’s laptop containing company data might get stolen, and without proper verification, you might not even realize it’s missing. Verifying asset custody ensures that all devices are accounted for and protected, minimizing the risk of data loss, hacking, or unauthorized access.
3. Ensure Compliance with Regulations
Many businesses must comply with industry regulations regarding the handling and protection of IT assets. For example, regulations like GDPR (General Data Protection Regulation) or HIPAA (Health Insurance Portability and Accountability Act) require businesses to secure personal data and ensure that digital assets are properly managed. Verifying custody helps businesses stay compliant with these laws by ensuring that assets are properly secured, monitored, and handled according to legal requirements.
4. Increase Operational Efficiency
When assets are regularly verified, businesses can avoid the chaos of misplaced or mismanaged equipment. For instance, keeping track of software licenses, ensuring devices are properly configured, or knowing which employee is using which laptop can save time and reduce errors. By verifying custody, businesses can ensure that their IT resources are being used effectively, improving overall productivity and minimizing unnecessary expenses related to lost or damaged assets.
5. Build Trust and Accountability
Verifying asset custody fosters a culture of accountability within the company. When employees know that assets are regularly tracked and monitored, they are more likely to take care of them and report any issues. Additionally, it creates transparency for external stakeholders, such as investors, clients, or regulatory bodies, who may want assurance that assets are being properly managed and secured.
6. Prevent Financial Loss
The cost of replacing lost or damaged IT assets can quickly add up, especially when it comes to expensive hardware or software. Regular verification helps identify issues early, allowing for quicker resolutions and preventing costly replacements. Furthermore, keeping track of IT assets helps prevent underutilized resources from sitting idle, potentially saving the business money on unnecessary purchases.
How to Verify IT Asset Custody
Verifying the custody of IT assets involves setting up clear systems and processes to ensure that each asset is properly tracked, assigned, and accounted for.
1. Establish a System for Tracking and Assigning Assets
The first step in verifying IT asset custody is to set up a reliable system for tracking and assigning your assets. This system will help ensure that every asset is accounted for and can be easily identified, assigned, and monitored. Here’s how to do it:
Asset Register
Create a centralized database (either physical or digital) where you record every IT asset. This register should include crucial details about each asset, such as:
- Asset Tag: A unique identifier, such as a QR, barcode or RFID tag, that can be used to track the asset.
- Serial Number: A specific identifier provided by the manufacturer for each asset.
- Manufacturer and Model: Details about the maker and type of each asset.
- Assigned User: The person, department, or team responsible for the asset, along with the date it was assigned.
Having all of this information in one place makes it easier to track assets, verify their custody, and ensure they are properly managed.
Unique Identifiers
Each asset should have a unique identifier, such as a QR Code, barcode, serial number, or RFID tag. These identifiers allow you to track assets more effectively, and they simplify the process of verifying their custody. By linking each asset to its unique identifier, you ensure that there is no confusion about which asset belongs to whom.
User Assignment
Clearly define how assets are assigned to employees or teams. This includes establishing a formal process for requesting, approving, and recording asset assignments. Each time an asset is issued, make sure the process includes:
- Approval Process: Ensure proper authorization is in place before assigning an asset.
- Documentation: Record who the asset is assigned to and keep track of any changes, such as reassignment or return of assets.
Having a clear user assignment system in place ensures that everyone knows who is responsible for each asset at all times, helping prevent misuse or loss.
2. Implement Verification Procedures
Once you have a system for tracking and assigning your IT assets, the next step is to implement procedures that ensure these assets are regularly verified for custody, condition, and usage. Verification procedures help ensure accountability and prevent issues like asset loss or misuse.
Physical Audits
Conduct regular physical inspections of your IT assets to confirm their presence and condition. During these audits, verify that the assets in your possession match the records in your asset register. This process involves:
- Checking Asset Tags: Ensure each asset is correctly tagged with its unique identifier (e.g., barcode, serial number).
- Inspecting Condition: Assess the physical condition of each asset to ensure it’s in working order and hasn't been damaged or misused.
- Cross-Checking with Asset Register: Compare the physical assets with the entries in your asset register to ensure accuracy.
Physical audits are typically done at regular intervals (e.g., quarterly or annually), but more frequent checks may be necessary for high-value or critical assets.
System-Based Verification
Leverage it asset management software to help automate and streamline the verification process. This can include:
- Verification Requests: The software can send out automated requests to users, asking them to confirm they have the assets assigned to them and verify their condition.
- Digital Reporting: Users can confirm the asset’s status directly through the software, allowing for quick updates to the asset register.
- Audit Trails: Most asset management systems also allow you to track verification history, making it easier to spot any issues or discrepancies over time.
Automated Reminders
Set up automated alerts within your asset management system to remind users when it’s time to verify their assigned assets. These reminders can:
- Be sent via email or text message to ensure users don’t forget to respond.
- Include a deadline to prompt users to complete the verification promptly, minimizing delays.
Automated reminders help keep the process on track, ensuring that verification is completed on time without requiring constant manual follow-up.
Signature Capture
To add an extra layer of accountability, consider requiring electronic signatures during the verification process. When employees confirm they have an asset and verify its condition, they can sign off electronically, ensuring that they take responsibility for the asset.
- Digital Signatures: Use digital signature software to capture the user’s agreement, adding legal weight to the verification process.
- Record of Responsibility: By capturing signatures, you create a clear record of who is responsible for each asset, which can help resolve disputes or accountability issues.
3. Manage Verification Results
After conducting asset verification, the next critical step is to manage and track the results of these checks. This process helps ensure that any discrepancies are addressed, records are updated, and that proper follow-up actions are taken.
Track Verification Status
Monitor the progress and status of verification requests within your asset management system. Each request should have a clear status, such as:
- Pending: The verification has not yet been completed or confirmed.
- Verified: The asset has been successfully verified, and the information matches the asset register.
- Rejected: The asset could not be verified, possibly due to missing, damaged, or incorrect information.
Keeping track of the verification status ensures you can follow up on any outstanding tasks and address problems in a timely manner.
Investigate Discrepancies
If discrepancies are identified during verification—such as a missing asset or incorrect asset details—it’s important to investigate the issue promptly. Some common discrepancies include:
- Missing Assets: If an asset isn’t found during a physical audit or cannot be verified in the system, you’ll need to trace its last known location or user.
- Condition Issues: If an asset is reported as damaged or in poor condition, investigate to determine whether it needs to be repaired, replaced, or removed from service.
- Misassigned Assets: If assets are assigned to the wrong users or departments, rectify the assignment immediately and update records.
Investigating discrepancies helps ensure your asset register remains accurate and up to date, preventing any surprises or issues down the line.
Update Asset Records
Once verification is complete and any discrepancies are resolved, update your asset register with the latest information. This may include:
- Asset Status: Change the status of the asset if it has been repaired, reassigned, or disposed of.
- User Assignment: Update the records if an asset has been reassigned to a new user or department.
- Condition Report: Note any changes to the asset’s condition based on the verification results.
Updating the asset register ensures that all records reflect the most accurate, current status of your IT assets, which is crucial for future audits and asset management.
4. Additional Considerations
While implementing and managing asset verification procedures, there are several additional factors that can help streamline the process and ensure security, compliance, and efficiency.
Role-Based Access
Implement role-based access controls (RBAC) within your asset management system. This ensures that only authorized individuals can access sensitive data or make changes to asset records. For example:
- Admin Access: Only system administrators should have full control over asset management features.
- User Access: Employees can view and confirm their assigned assets but may not have permission to edit asset details or reassign them to others.
RBAC helps protect the integrity of your asset records by limiting access based on user roles, which reduces the risk of unauthorized changes or misuse.
Training
Providing proper training to employees on how to use the asset management system and participate in verification procedures is essential. Employees should understand:
- How to Confirm Assets: Teach them how to access the asset register, verify their assigned assets, and report any issues.
- Asset Care: Educate employees on the proper care and security protocols for the assets they are responsible for (e.g., keeping devices secure, not sharing access credentials).
- Verification Procedures: Make sure employees are familiar with the verification process, including how to respond to verification requests and how to handle discrepancies.
Training ensures that everyone involved in asset management is on the same page, leading to more efficient and accurate verification processes.
Documentation
Maintaining clear and up-to-date documentation of your asset management policies and procedures is critical for ensuring consistency and compliance. This should include:
- Verification Procedures: A step-by-step guide for how verification is carried out, including timelines and responsibilities.
- Asset Management Policies: Clear rules for asset assignment, usage, maintenance, and disposal.
- Compliance and Audit Logs: Documentation that tracks who is responsible for which assets and when verification occurred, which can be useful during audits or legal reviews.
Having well-documented processes and policies ensures that your asset management system operates smoothly and complies with both internal and external standards.
Common Challenges in Asset Custody Verification
- Lack of Standardization: Different departments or teams may use varied systems for tracking and verifying assets, leading to inconsistencies.
- Complex Ownership Structures: IT assets may be shared across multiple departments or managed by external vendors, making it difficult to track responsibility.
- Asset Mismanagement or Neglect: Employees may not report damaged, lost, or misused assets, risking security and operational issues.
- High Volume of Assets: Managing a large number of assets, especially in fast-growing organizations, can overwhelm tracking and verification efforts.
- Resistance to Change: Employees or teams may resist new asset verification procedures, slowing down the process or causing non-compliance.
- Inadequate Technology or Tools: Manual tracking or outdated software can lead to inefficiencies, errors, and difficulty in managing assets.
- Human Error: Mistakes in asset verification or reporting can compromise the accuracy and integrity of asset records.
How AssetLoom Helps in Managing Custody Verification
AssetLoom simplifies the management of asset custody verification by providing a streamlined process for administrators and users to track, verify, and manage the status of IT assets.
1. Centralized Asset Custody Tracking
AssetLoom keeps all asset information in one place, ensuring that administrators and authorized users can easily access detailed records for each asset. This includes crucial information such as:
- Asset Name
- Asset Tag
- Assigned User
- Condition
- Verification Status (Pending, Verified, Not in Possession) This centralization allows for better oversight and efficient management of assets across different departments or teams.
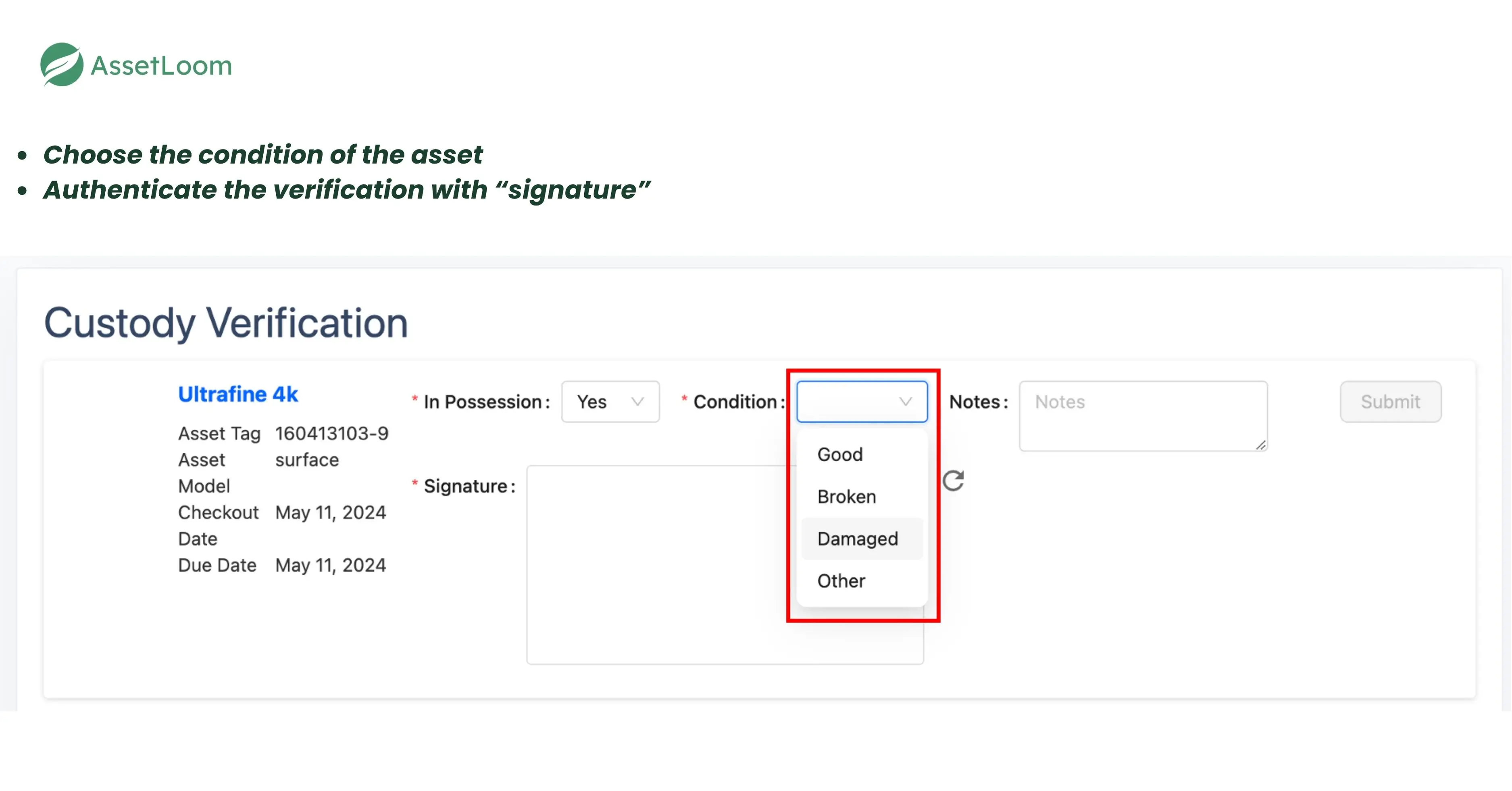
2. Verification Request Management
Administrators can initiate and send out custody verification requests with just a few clicks. AssetLoom makes it easy to:
- Select individual assets or bulk assets for verification.
- Set specific due dates for the verification completion.
- Add instructions or notes to help users understand the context of the verification request.
3. Automated Reminders & Notifications
AssetLoom automatically sends out email notifications to users when it’s time to verify the custody of their assigned assets. This ensures that no verification request is missed and keeps the process timely and organized.
4. Digital Signature Capture
To enhance accountability, AssetLoom captures digital signatures from users during the verification process. When users confirm possession or provide condition reports, they can sign electronically, ensuring that the information is accurate and verifiable.
5. Verification Status Monitoring
AssetLoom enables administrators to track the verification status of each asset. You can easily filter and view the following statuses:
- Pending: Verifications waiting for user responses.
- Verified: Completed and confirmed verifications.
- Not in Possession: Assets that are not currently with the user.
This helps to maintain a real-time overview of which assets are verified, whose custody is pending, and which assets need immediate attention.
6. Advanced Filtering Options
AssetLoom provides advanced filtering options that allow administrators to sort custody verification lists based on different criteria, such as:
- Assigned User: Filter by the individual or department assigned to the asset.
- Condition: Search by asset conditions (e.g., Good, Damaged, Lost).
- Due Date: Find assets that need urgent verification or are overdue.
7. Bulk Verification Process
For larger organizations or during audits, AssetLoom offers bulk verification features. Administrators can:
- Select multiple assets for verification.
- Send out group verification requests in a streamlined process.
- Review and finalize bulk verification requests quickly.
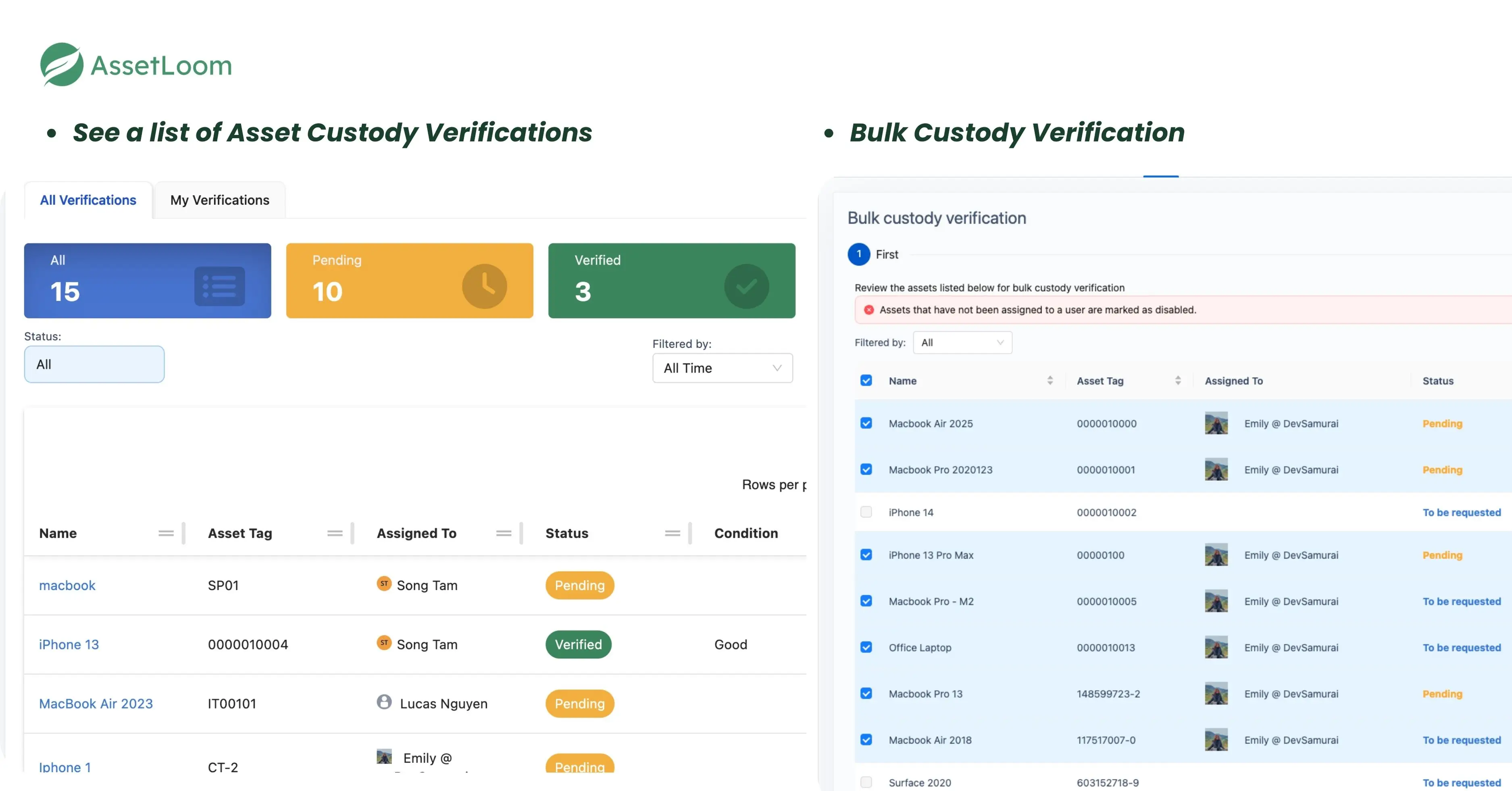
8. Tracking and Resolving Discrepancies
If any discrepancies arise (e.g., missing assets, damaged equipment), AssetLoom helps administrators track and address these issues. The system allows for easy investigation and updates, ensuring that all discrepancies are resolved and the asset records are accurate.
9. Detailed Asset Condition Reports
Users are asked to report the condition of the asset they’re verifying, with options like:
- Good, Broken, Damaged, Lost, Stolen: These specific condition options ensure that AssetLoom captures the asset’s true status, enabling better asset management and faster resolution for any issues.
10. Comprehensive Reporting and Audit Trail
AssetLoom keeps an audit trail of all custody verification activities, allowing businesses to generate reports that show asset movement, user responses, and verification statuses. This transparency ensures full accountability and supports compliance with internal policies or external regulations.
Conclusion
Verifying the custody of your IT assets is a crucial part of maintaining control, security, and accountability within your business. By establishing clear tracking systems, conducting regular verifications, and using tools like AssetLoom to streamline the process, you can significantly reduce risks such as loss, theft, or misuse.
From ensuring legal compliance to improving operational efficiency, the benefits of asset custody verification are undeniable. It not only protects your assets but also fosters a culture of responsibility across the organization. With the right procedures and technologies in place, managing and verifying the custody of IT assets becomes a straightforward, reliable process that contributes to the overall health and success of your business.
By embracing a systematic approach to asset custody verification, businesses can stay secure, efficient, and compliant, safeguarding both their physical and digital resources for the future.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


