How Enterprise Mobility Management (EMM) Keeps Your Business Devices Secure
Keep mobile devices secure and compliant with Enterprise Mobility Management (EMM). Gain full IT control over access, apps, and data anywhere.
You can’t secure what you can’t see, and mobile devices are the biggest blind spot in most IT environments today.
Employees are working from airports, coffee shops, and their own personal phones. Field teams are constantly switching devices. And when someone leaves the company, there’s no guarantee the data leaves with them.
This isn’t just inconvenient. It’s a security risk. A compliance risk. A business continuity risk.
The challenge is clear: IT teams need a better way to manage and protect mobile endpoints at scale. Enterprise Mobility Management (EMM) gives them the visibility and control to do exactly that, without compromising flexibility or speed.
In this blog, we’ll break down how EMM helps your team lock down devices, enforce policies, and keep sensitive data secure, no matter where or how work gets done.
What Is Enterprise Mobility Management (EMM)?
Let’s start simple: Enterprise Mobility Management, or EMM, is a way to keep all your company’s mobile devices, apps, and data safe and under control.
You might be familiar with Mobile Device Management (MDM), which mainly handles device settings and restrictions. EMM goes further. It wraps device management together with app security, data protection, and user access, all in one package.
Think of it this way: if your IT Hardware Asset Management is like knowing what devices you own and where they are, EMM is making sure those devices are set up right, locked down, and playing by the rules, no matter where they are or who’s using them.
For example, say your sales team is using company-issued smartphones like iPhones on the road. EMM ensures those iPhones have the right security settings, approved apps only, and that sensitive company data stays protected even if a phone gets lost or stolen.
It’s the kind of control and visibility your IT team needs to manage devices that aren’t always sitting in the office, without slowing everyone down.
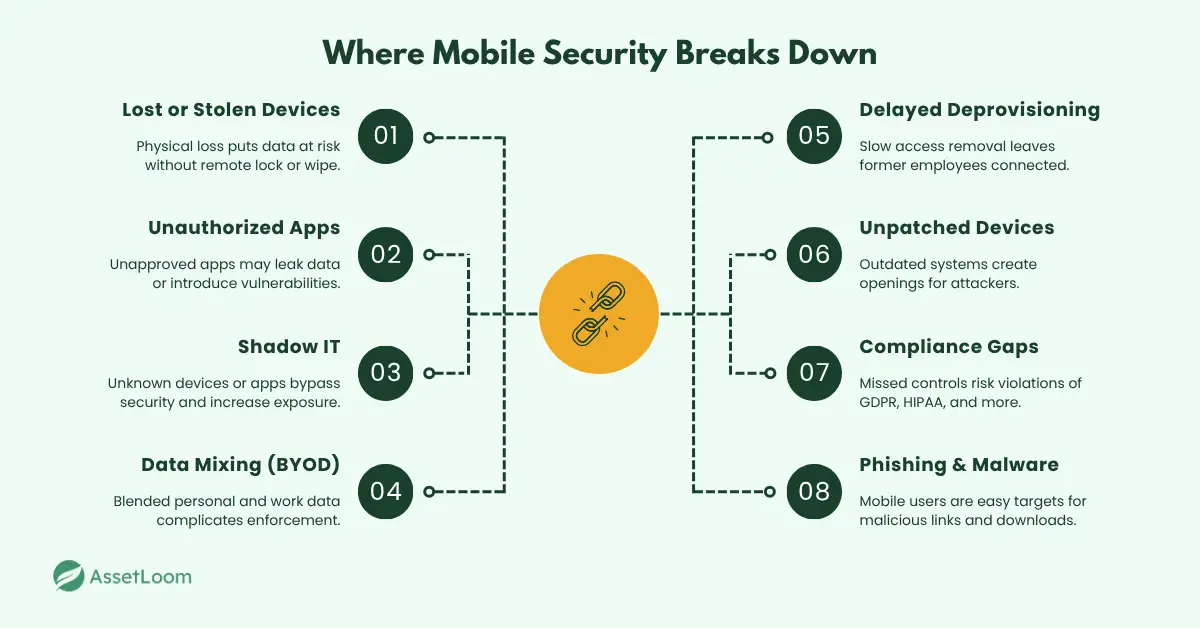
The Modern Threat Landscape for Mobile Devices
Mobile devices like laptops, tablets, and smartphones are everywhere in today’s workplace. But each device introduces multiple risks:
- Lost or stolen devices: Physical loss can lead to unauthorized access if the device isn’t secured or wiped remotely.
- Unauthorized apps: Employees may install apps that don’t meet security standards, creating vulnerabilities or leaking data.
- Shadow IT: Devices or apps used without IT’s knowledge complicate security and compliance efforts.
- Data mixing: In BYOD setups, personal and corporate data often coexist, making it harder to enforce strict policies.
- Delayed deprovisioning: When employees leave or change roles, delays in revoking device access increase risk.
- Unpatched devices: Outdated operating systems or apps leave security holes that attackers exploit.
- Compliance risks: Regulations like GDPR and HIPAA require strict control over mobile data; noncompliance can lead to heavy fines.
- Phishing and malware: Mobile devices are often targeted with phishing attacks or malware via email, apps, or insecure networks.
These challenges make it clear: standard IT security tools aren’t enough. Your IT team needs better visibility into every device, tighter controls over apps and data, and the ability to respond quickly to threats.
Enterprise Mobility Management (EMM) helps fill these gaps by providing centralized management and automated security enforcement across your entire mobile fleet.
Read also: How to Track a Stolen Laptop with Serial Number: Step-by-Step Guide
How Enterprise Mobility Management Keeps Business Devices Secure
Mobile devices are no longer just tools. They’re potential liabilities. Whether it's a lost tablet, a misconfigured phone, or an unpatched laptop in a remote location, every mobile endpoint introduces risk.
Enterprise Mobility Management (EMM) directly addresses that risk by giving IT teams real-time visibility, control, and response capabilities across every device, app, and data connection in use. Here's a detailed look at how EMM keeps business devices secure, with practical insights that apply across industries.
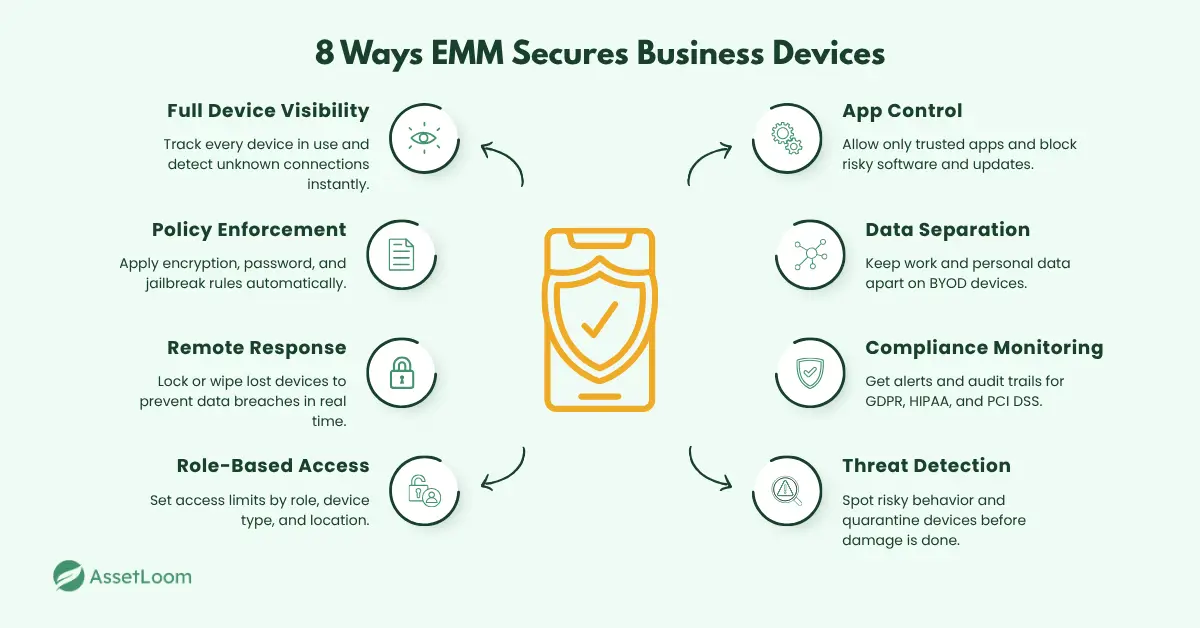
Full Device Visibility: The Foundation of Mobile Security
Security starts with knowing what’s out there. EMM platforms continuously track and inventory all mobile devices that connect to your environment, whether they are corporate-owned or personal.
This means:
- IT knows who is using what device, where, and when
- Unknown or unmanaged devices can be flagged or blocked
- Device status, such as OS version, encryption, or compliance, is visible at a glance
Insight: Many organizations underestimate how many unmanaged devices access company systems. EMM often reveals a hidden inventory, especially in fast-growing field teams or companies working with external contractors.
Policy Enforcement Without Manual Effort
Instead of relying on individual users to follow security policies, EMM automates enforcement across the entire mobile fleet.
This includes:
- Requiring encryption and passcodes
- Blocking risky features like screen sharing or file downloads
- Preventing access from jailbroken or rooted devices
Real example: A logistics company used EMM to block access from any tablet without a screen lock. When a driver left a device in an unlocked vehicle, the data remained safe because the device could not be accessed.
Remote Actions When Time Is Critical
Lost or stolen devices are a common reality. With EMM, your IT team can respond immediately by:
- Locking the device remotely
- Wiping sensitive business data
- Revoking access to systems and apps
Insight: In industries like telecom or healthcare, field staff often carry sensitive data. The ability to wipe that data instantly has prevented breaches that could have cost millions.
Role-Based Access Control That Aligns With Risk
EMM gives IT teams the flexibility to define who gets access to what, from where, and on which type of device.
For example:
- Finance staff can access sensitive systems only on encrypted company laptops
- Contractors can be restricted to limited-access web apps from managed devices
- Access from specific locations or networks can be denied entirely
Why it matters: Many security incidents come from overly broad access permissions. EMM allows organizations to align access levels with actual risk.
Application-Level Controls to Prevent Shadow IT
Shadow IT happens when users install unapproved or insecure apps. EMM solves this by:
- Allowing only whitelisted apps
- Blocking known-risk apps and consumer software
- Pushing mandatory updates to business-critical apps
Field example: One company discovered 30% of employees were using consumer messaging apps for work. EMM allowed them to roll out a secure, approved option while blocking everything else without touching a single device in person.
Separation of Personal and Business Data
In BYOD environments, users want to keep personal content private. EMM supports this by using containerization to keep business data separate.
This means:
- Work apps and data are stored in a secure, isolated container
- IT can wipe business data without affecting personal photos or apps
- Users maintain privacy while IT maintains security
Insight: Employees are far more likely to adopt security tools that respect personal boundaries. EMM gives you that balance.
Real-Time Compliance Monitoring and Reporting
Regulations like GDPR, HIPAA, and PCI DSS require ongoing oversight. EMM provides real-time monitoring and reporting to support compliance efforts.
Features include:
- Alerts when devices fall out of compliance
- Reports on patch status, policy enforcement, and app usage
- Audit trails to prove control in place for mobile security
Compliance advantage: Whether you face an audit or just want peace of mind, EMM helps you show that policies are actively enforced across all devices.
Integrated Threat Detection and Faster Response
Some modern EMM platforms go beyond configuration and integrate with endpoint security tools. This allows IT teams to:
- Detect risky behaviors or malicious apps
- Quarantine compromised devices automatically
- Factor device risk into real-time access decisions
Forward-thinking insight: This type of integration supports a zero-trust model, where access is based not just on credentials but also on the current health and behavior of each device.
Security You Can Rely On, Wherever Teams Work
Mobile threats are no longer hypothetical. Devices get misplaced. Employees install risky apps. Attackers look for weak spots in your security posture, and mobile is often the easiest target.
Enterprise Mobility Management gives you the visibility and control to deal with these risks head-on. It transforms scattered, unmanaged devices into a secure, centralized system that your IT team can trust.
The result: employees work freely and securely, and your business stays protected no matter where work happens.
Conclusion
Managing mobile devices isn’t getting any easier, and the risks only grow as work gets more flexible and distributed.
Enterprise Mobility Management gives your IT team the tools to see every device, enforce policies, and protect sensitive data, no matter where devices are or who’s using them. Without it, blind spots open the door to costly breaches and compliance headaches.
If you want to keep control without slowing down your teams, EMM is no longer optional; it’s essential. Start building a smarter, safer mobile strategy today, and turn your mobile devices from a security risk into a business advantage.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.

