Understanding Cloud Security Posture Management
Discover how Cloud Security Posture Management tools mitigate risks, ensure compliance, and enhance security in cloud environments.
Businesses nowadays rely heavily on cloud computing to store data, run applications, and deliver services. However, with the increasing use of cloud platforms comes the need to ensure their security. This is where Cloud Security Posture Management (CSPM) plays a critical role. CSPM is a set of tools and processes designed to monitor, assess, and improve the security of cloud environments. This article explains what CSPM is, why it matters, how it works, and its benefits for organizations, all in clear and straightforward language.
What Is Cloud Security Posture Management?
Cloud Security Posture Management refers to a group of automated tools and practices that help organizations manage and secure their cloud infrastructure. The cloud includes services like Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and other platforms where businesses store data or run applications. CSPM focuses on identifying and fixing security risks, such as misconfigurations, vulnerabilities, or non-compliance with regulations, to keep cloud environments safe.
Read more: What is Cloud Asset Management in ITAM? Key Features and Functions
CSPM tools continuously scan cloud resources, like servers, databases, storage systems, or user access permissions, to ensure they meet security standards. For example, they might detect an unsecured storage bucket that could expose sensitive data to the public or flag a user account with excessive permissions. By addressing these issues, CSPM helps prevent data breaches, cyberattacks, and regulatory penalties.
Why Is Cloud Security Posture Management Important?
The cloud offers flexibility and scalability, but it also introduces unique security challenges. Unlike traditional on-premises IT systems, cloud environments are dynamic, with resources frequently added, changed, or removed. This complexity makes it easy for errors to occur, such as leaving data unprotected or granting improper access. Here’s why CSPM is essential:
- Reduces Misconfigurations: Misconfigurations, like unsecured databases or open ports, are a leading cause of cloud security incidents. CSPM tools detect and fix these errors before they can be exploited.
- Ensures Compliance: Many industries must follow regulations like GDPR, HIPAA, or PCI DSS, which set strict rules for data protection. CSPM helps organizations stay compliant by monitoring their cloud setup against these standards.
- Improves Visibility: Cloud environments often involve multiple services and teams, making it hard to track all resources. CSPM provides a clear view of all cloud assets, reducing the risk of unnoticed vulnerabilities.
- Prevents Data Breaches: By identifying and addressing risks early, CSPM lowers the chance of cyberattacks that could lead to costly data leaks or downtime.
- Supports Scalability: As businesses grow and add more cloud resources, CSPM scales to monitor new assets without requiring manual oversight.
How Does Cloud Security Posture Management Work?
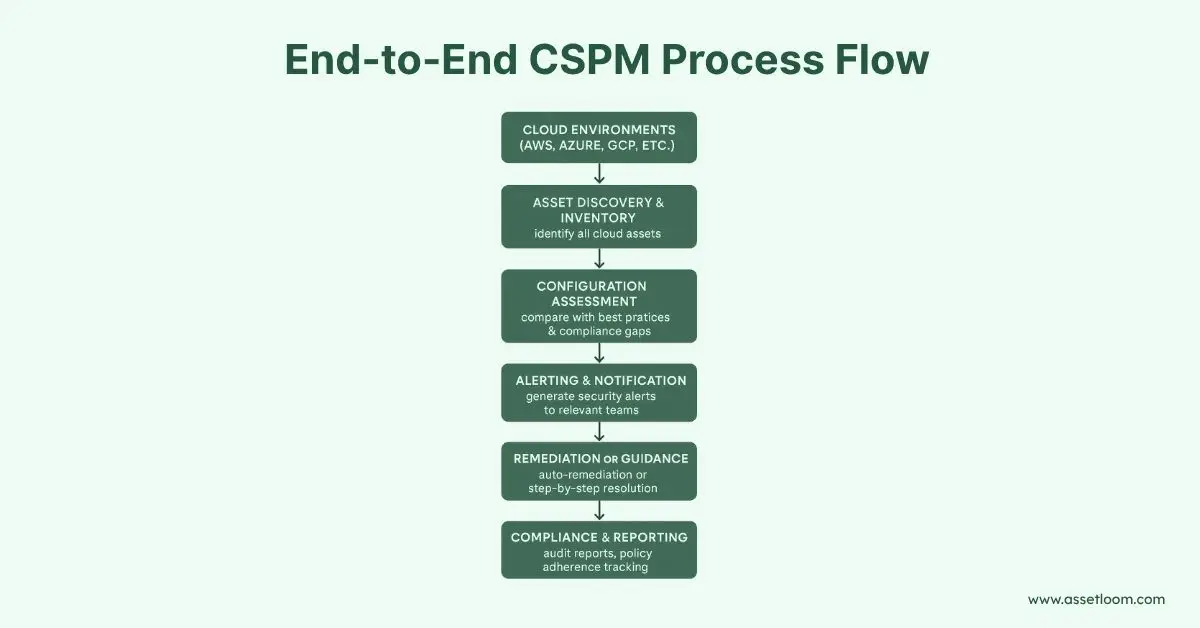
CSPM operates through a combination of automated scanning, analysis, and reporting. Here’s a step-by-step look at how it functions:
1. Discovery of Cloud Assets
Cloud security posture management tools start by identifying all resources in a cloud environment, such as virtual machines, storage buckets, databases, or user accounts. This step ensures no assets are overlooked, including those created without IT’s knowledge (known as shadow IT).
Read more: Top 10 Cloud Asset Management Software for Modern Businesses in 2025
2. Configuration Assessment
Once assets are identified, CSPM scans them to check for misconfigurations. For example, it might find a storage bucket set to “public” or a database without encryption. It compares the setup against security best practices, such as those from the Center for Internet Security (CIS) or cloud provider guidelines.
3. Compliance Monitoring
Cloud security posture management checks whether the cloud environment meets regulatory requirements or industry standards. For instance, it ensures sensitive data is encrypted to comply with GDPR or that access logs are enabled for PCI DSS.
4. Risk Prioritization
Not all issues are equally urgent. CSPM tools rank risks based on severity, helping teams focus on critical problems first, like an exposed database versus a minor permission issue.
5. Remediation Guidance
After identifying issues, CSPM provides recommendations for fixing them. Some tools can even automate fixes, such as tightening access controls or enabling encryption, reducing the workload for IT teams.
6. Continuous Monitoring
Cloud environments change constantly, so CSPM tools run ongoing scans to catch new risks as they arise. This ensures security remains consistent over time.
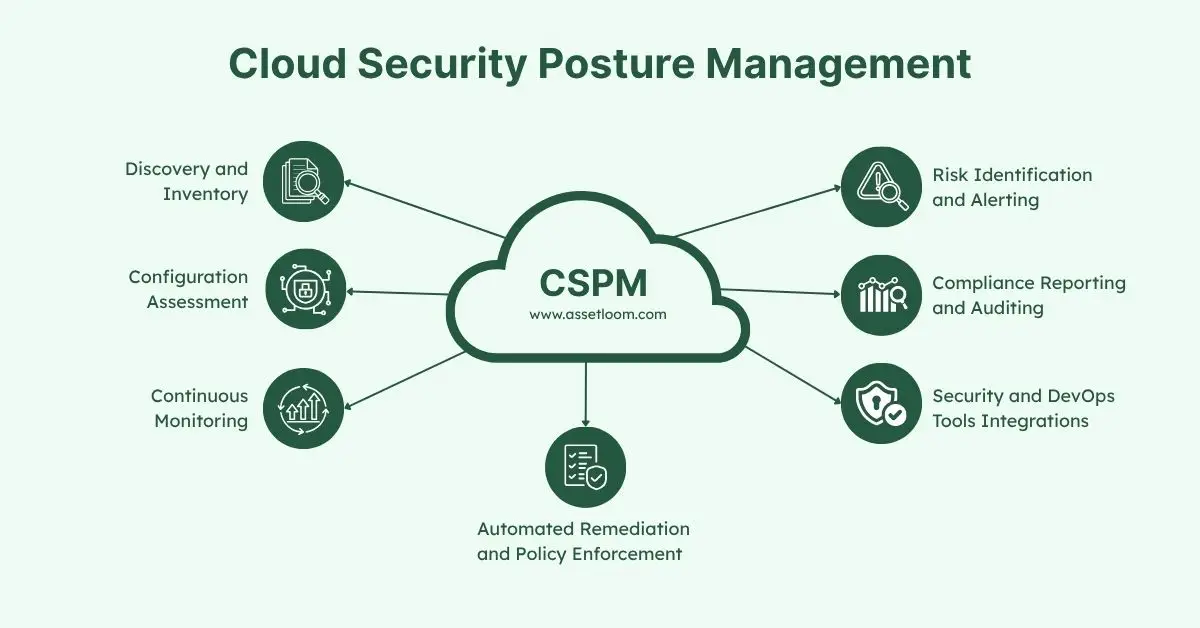
Key Features of Cloud Security Posture Management Tools
CSPM solutions vary, but most include the following features to support cloud security:
- Asset Inventory: Tracks all cloud resources to provide full visibility.
- Configuration Checks: Scans for misconfigurations and vulnerabilities.
- Compliance Templates: Offers pre-built rules for regulations like GDPR, HIPAA, or SOC 2.
- Automated Remediation: Fixes issues automatically when possible.
- Reporting and Alerts: Generates reports for audits and sends alerts for urgent risks.
- Integration: Works with other security tools, like firewalls or identity management systems, for a unified approach.
Popular CSPM tools include Prisma Cloud, Check Point CloudGuard, and Microsoft Defender for Cloud, among others. Each offers unique features, but all aim to simplify cloud security management.
Benefits of Cloud Security Posture Management
Implementing Cloud security posture management brings several advantages to organizations using cloud services. Here are the main benefits:
Enhanced Security
CSPM reduces the risk of cyberattacks by addressing vulnerabilities before they can be exploited. For example, fixing an open storage bucket prevents unauthorized access to sensitive data.
Simplified Compliance
Meeting regulatory requirements can be complex, but CSPM automates compliance checks, saving time and reducing the risk of fines or penalties.
Increased Efficiency
Manual security checks are time-consuming and error-prone. CSPM automates these tasks, allowing IT teams to focus on other priorities.
Cost Savings
Preventing breaches or compliance violations avoids costly consequences, such as legal fees, ransom payments, or lost business. CSPM’s proactive approach helps organizations save money in the long run.
Better Collaboration
CSPM provides clear reports and dashboards that help IT, security, and compliance teams work together effectively, aligning their efforts to improve cloud security.
Challenges of Cloud Security Posture Management
While Cloud security posture management offers significant benefits, it’s not without challenges. Organizations should be aware of these potential hurdles:
- Complex Implementation: Setting up CSPM tools can be time-consuming, especially in large or multi-cloud environments with many resources.
- Alert Overload: CSPM tools may generate numerous alerts, which can overwhelm teams if not prioritized properly.
- Skill Gaps: Some organizations lack staff with expertise in cloud security, making it harder to use CSPM tools effectively.
- Cost Considerations: While CSPM can save money long-term, the initial cost of tools and subscriptions may be a barrier for smaller businesses.
- Multi-Cloud Complexity: Organizations using multiple cloud providers (e.g., AWS and Azure) may struggle to unify CSPM across platforms.
To address these challenges, businesses can start with a single cloud provider, train staff on CSPM tools, or work with a managed security provider for support.
Best Practices for Using Cloud Security Posture Management
To get the most out of CSPM, organizations should follow these best practices:
- Start with a Clear Strategy: Define security and compliance goals before selecting a CSPM tool to ensure it meets your needs.
- Regularly Review Alerts: Prioritize and address high-risk issues promptly to maintain a strong security posture.
- Train Your Team: Ensure staff understand how to use CSPM tools and interpret their findings.
- Integrate with Other Tools: Combine CSPM with other security solutions, like threat detection or access management, for comprehensive protection.
- Update Policies: Regularly review and update cloud security policies to align with new threats or regulations.
Read more: Using Cloud Asset Tracking to Catch Ghost Assets Early
The Future of Cloud Security Posture Management
As cloud adoption grows, CSPM is becoming more advanced and essential. Emerging trends include:
- AI and Machine Learning: CSPM tools are using AI to predict risks and automate more complex remediation tasks.
- Multi-Cloud Support: Tools are improving their ability to manage security across multiple cloud providers seamlessly.
- Integration with DevOps: CSPM is being integrated into development pipelines to catch security issues early in the software lifecycle.
- Zero Trust Alignment: CSPM is aligning with zero trust principles, which assume no user or device is inherently safe, to enhance security.
These advancements will make CSPM even more effective at protecting cloud environments in the years ahead.
Conclusion
Cloud security posture management is a vital tool for organizations using cloud services. By identifying misconfigurations, ensuring compliance, and improving visibility, CSPM helps businesses protect their data and avoid costly security incidents. While challenges like complexity or costs exist, the benefits of enhanced security, efficiency, and compliance make CSPM a worthwhile investment. By adopting CSPM and following best practices, organizations can confidently embrace the cloud while keeping their assets safe.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


