Leveraging CrowdStrike Falcon Audit for Real-Time Incident Response: Best Practices
Master best practices for using CrowdStrike Falcon Audit in real-time incident response, including alert customization, automation, and forensic log analysis.
When a security incident strikes, delays can be costly - missed alerts, slow responses, and incomplete data can turn a manageable issue into a full-blown crisis. The pressure of identifying and containing a threat in time can feel overwhelming, especially when the right tools aren’t fully optimized.
CrowdStrike Falcon Audit gives you the visibility you need to detect and respond to threats in real time. But to truly harness its power, you need to go beyond basic setups and adopt best practices that help you act faster, automate key responses, and leverage forensic data effectively.
In this post, we’ll cover practical tips for mastering real-time incident response with Falcon Audit, from customizing alerts to using forensic logs for deeper analysis, so you can respond with confidence and speed.
Understanding CrowdStrike Falcon Audit
Before diving into the best practices, it’s important to understand how CrowdStrike Falcon Audit works and why it’s essential for real-time incident response.
CrowdStrike Falcon is a cloud-native endpoint protection platform that uses artificial intelligence (AI) to prevent, detect, and respond to cybersecurity threats in real time. Falcon Audit is a critical feature of this platform, providing complete visibility into endpoint activity, allowing you to track everything from file modifications to process executions. It records detailed logs of all security events and suspicious activities, which can help you detect threats early, analyze how an attack unfolds, and respond swiftly to minimize damage.
For organizations involved in IT Hardware Asset Management, Falcon Audit ensures that all endpoints, whether physical or virtual, are closely monitored and protected against cyber threats, providing security teams with vital insights to safeguard critical IT assets.
At its core, Falcon Audit helps you answer critical questions during an incident:
-
What happened? – Reconstruct the timeline of the attack.
-
When did it happen? – Pinpoint when the attack began and how it progressed.
-
How did it happen? – Identify the tactics, techniques, and procedures (TTPs) used by attackers.
Understanding these basics ensures that you can use Falcon Audit to its full potential during a security breach, giving you the information you need to respond quickly and effectively.
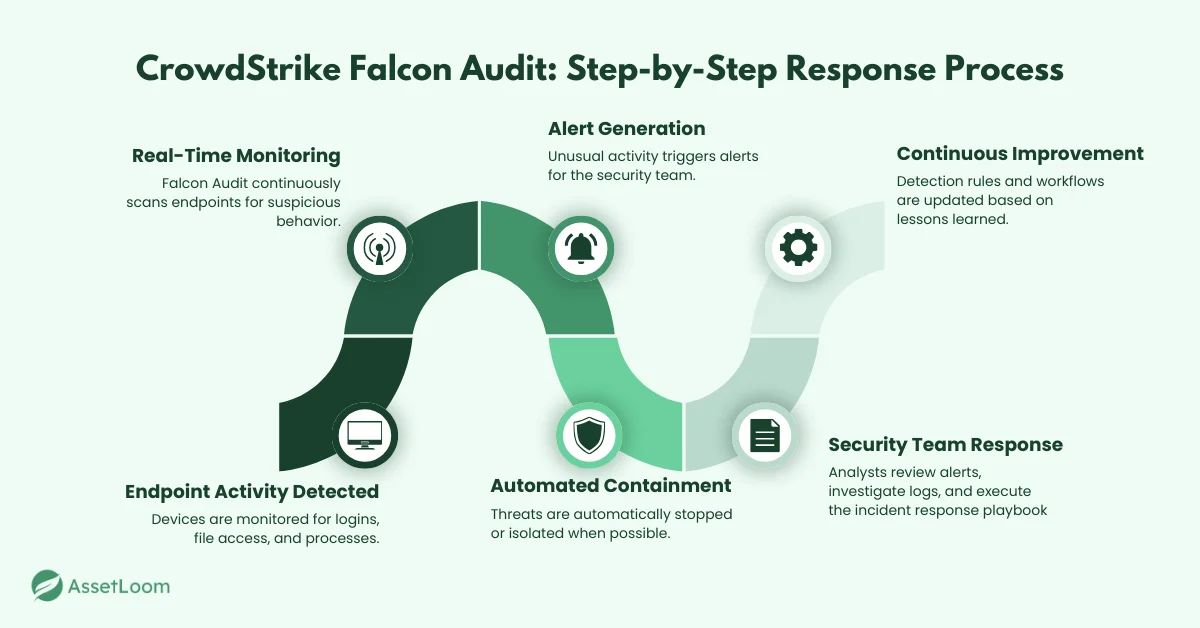
Advanced Best Practices for Leveraging CrowdStrike Falcon Audit in Real-Time Incident Response
1. Tailoring Real-Time Alerts to Focus on What Matters
To make the most of Falcon Audit’s alert system, it’s essential to customize alerts based on your organization’s unique vulnerabilities. By adjusting the alert thresholds and focusing on the most critical assets, you can avoid being overwhelmed by low-priority events. For example, if you manage sensitive data or critical servers, prioritize alerts for unusual access or failed login attempts. Customizing these alerts helps ensure that your security team focuses on high-risk events and can respond to them without delay.
Pro Tip: Set alert profiles for different teams, so they only receive relevant notifications, reducing confusion and speeding up responses.
2. Automating Responses to Speed Up Action
When it comes to security, speed is key. Automating your responses allows you to act fast without waiting for manual intervention. With Falcon Audit, you can automatically isolate compromised devices or block malicious traffic as soon as a threat is detected. For example, if ransomware is detected, Falcon Audit can immediately isolate the affected system, preventing the malware from spreading further.
Pro Tip: Use containment rules to automatically isolate compromised devices based on threat severity, ensuring quick action without manual intervention.
3. Using Forensic Logs to Understand What Happened
One of the most powerful features of Falcon Audit is its ability to provide detailed forensic logs. When an incident happens, these logs help you piece together the timeline of events, showing what happened, when it happened, and how the attack unfolded. By reviewing these logs, you can quickly understand the scope of the attack and identify how the intruder gained access. This level of detail allows you to strengthen your defenses by learning from past incidents and improving your overall enterprise cloud security.
Pro Tip: Leverage time-stamped logs to quickly trace the attack’s origin and scope, helping you focus on key events during an investigation.
4. Regularly Testing Your Incident Response Plan
You never know how well your incident response strategy will work until you test it. That’s why it’s essential to regularly test your systems with simulated attacks, like ransomware drills or phishing campaigns. These exercises show you how well Falcon Audit detects and responds to threats and help you fine-tune your strategy. Testing also gives you the chance to identify any gaps in your response plan.
Pro Tip: Conduct tabletop exercises to test your team’s response and Falcon Audit’s detection capabilities, identifying areas for improvement.
By following these best practices, you’ll be able to use CrowdStrike Falcon Audit to handle security incidents more efficiently. Whether it's customizing alerts, automating responses, using forensic logs, or regularly testing your incident response plan, these steps will help ensure you’re always prepared for potential threats.
5. Continuously Updating and Improving Your Security Rules
Cyber threats are constantly evolving, and so should your security measures. To stay ahead, it's crucial to regularly update your detection rules and response protocols in Falcon Audit. Review logs and threat data to identify patterns or tactics that may not have been fully addressed in your current security settings. For example, if new attack vectors emerge, update your system to detect those specific behaviors.
Pro Tip: Regularly review and refine your detection rules to include new threat intelligence, ensuring your system stays up-to-date with the latest tactics used by attackers.
By following these best practices, you’ll be able to use CrowdStrike Falcon Audit to handle security incidents more efficiently. Whether it's customizing alerts, automating responses, using forensic logs, regularly testing your response plan, or continuously improving security rules, these steps will ensure you're always prepared for potential threats.
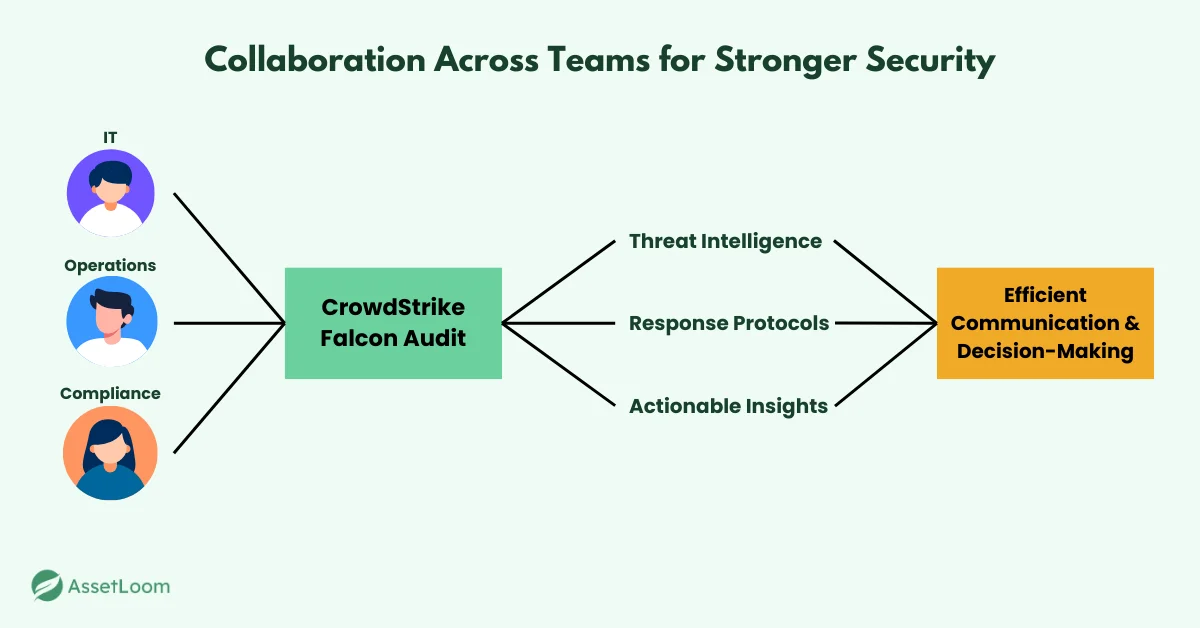
Collaborating Across Teams for Stronger Security
Successful incident response requires more than just the right tools; it also requires collaboration across teams. Integrating CrowdStrike Falcon Audit into your organization’s wider security strategy can help ensure that everyone is on the same page when a threat arises.
Work closely with your IT, operations, and compliance teams to ensure seamless coordination. Sharing threat intelligence, response protocols, and actionable insights from Falcon Audit will improve communication and speed up decision-making during incidents. Regularly review your incident response playbooks with all stakeholders to make sure everyone knows their role in a crisis.
By fostering collaboration and aligning Falcon Audit with your broader security efforts, you create a unified response strategy that enhances your organization’s ability to handle threats effectively.
Conclusion
Incorporating these CrowdStrike Falcon Audit best practices will help you detect and respond to threats faster and more effectively.
The key is to stay proactive. By refining your security measures and adapting to new threats, you’ll minimize the impact of incidents and strengthen your security posture. CrowdStrike Falcon Audit empowers you to protect your endpoints and respond quickly, keeping your organization safe.
Start applying these practices today to improve your response times and reduce security risks.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox

