Identifying Device Types: How Network Scanning Tools Can Help
Network scanning tools help in identifying device types on your network via several methods, like port scanning, OS fingerprinting, etc.
When you’re managing a network, could be a home setup, an office network, or an enterprise environment, one of the most important tasks is understanding exactly what devices are connected. It’s not just about knowing what’s out there but also about keeping everything secure, performing at its best, and making sure only authorized devices are on the network. That's why identifying device types is undeniable.
Automated network scanning tools can help identify all sorts of devices connected to your network. They perform asset discovery and provide insights into device types, making it easier to manage the network and ensure it’s secure.
But how do they figure out what devices are connected? How do they know what each device is and what it’s doing? Let’s take a closer look at the process, step by step.
What Are Network Scanning Tools?
Network scanning tools are designed to examine and assess the devices connected to your network. Think of them as digital detectives. They look for devices, figure out what type they are, and gather important details about them. These tools can tell you things like the device’s operating system, its open ports, and what services are running.
But why is all of this important? Well, knowing what devices are connected to your network is the first step in securing it. It ensures that only authorized devices are allowed to access the network and helps identify any security vulnerabilities these devices might have. It also assists with asset management, helping you keep track of devices as they come and go.
How Do Network Scanning Tools Help In Identifying Device Types?
Network scanning tools, or CMDB discovery tools, use several methods to identify devices. These methods involve gathering information about the device’s behavior, configuration, and communication patterns, all without needing direct access to the device itself. Let’s break down how these tools typically identify devices:
1. Scanning IP Addresses
The first step in identifying a device on a network is to look at the IP address. Each device connected to a network is assigned a unique IP address. Think of this as the device’s “address” on the network.
IP address scanner sends requests to a range of IP addresses and wait for a response. If a device is online, it will respond to the request, letting the tool know it’s there. From this, the tool can gather more information about the device and figure out what kind of device it might be.
2. Port Scanning
After identifying active device, the next step is to perform port scanning. Ports are like gateways through which devices communicate. Each service on a device, such as a web server, file server, or printer, uses a specific port to handle communication.
For example, a web server usually listens for requests on port 80. A file-sharing service will typically use port 21. By probing these ports, network scanning tools can figure out what services are running on a device. These services can give clues about the type of device.
Imagine scanning a device and finding that it has a web server running on it. This suggests the device might be a computer or server. If the tool finds that a printer’s service is running on a particular port, it identifies the device as a printer. In this way, network scanning tools can get a pretty good idea of the device’s function based on the services it exposes.
Below are some common ports and the types of devices or services that typically use them. This can help network scanning tools identifying device types based on which ports are open and responding.
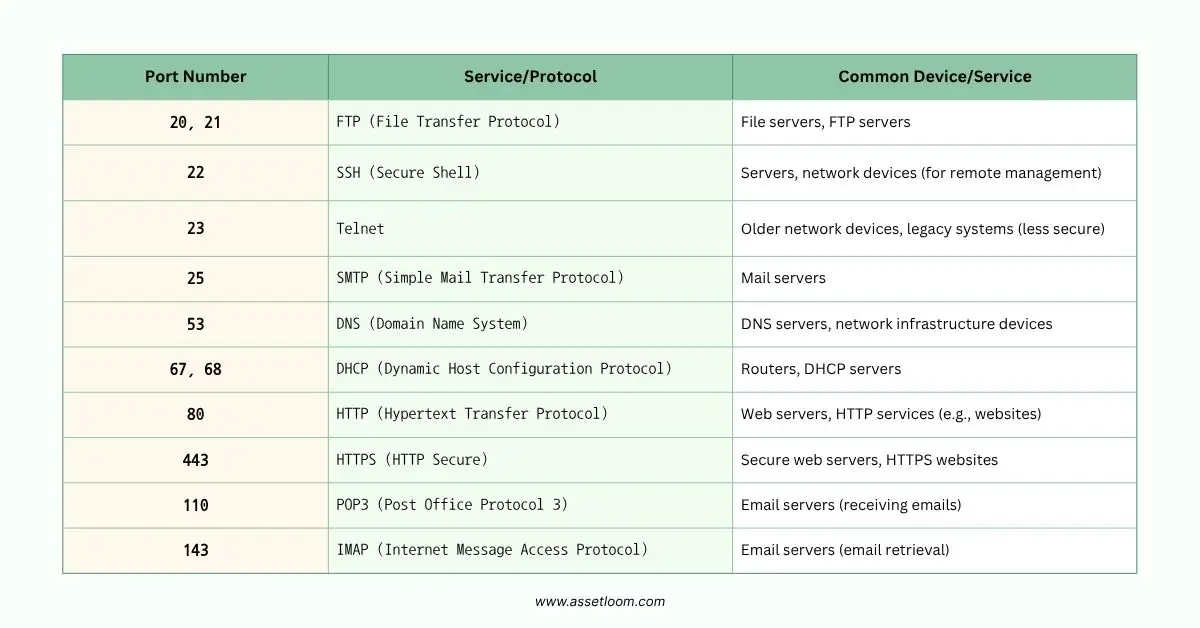
3. Operating System Fingerprinting
Now, this is where things get interesting. Operating system (OS) fingerprinting is a technique that helps identify the operating system of a device. It works by sending requests to the device and analyzing how it responds. Different operating systems, like Windows, Linux, or macOS, handle network communication differently. The way they respond to network requests can reveal a lot about them.
For example, Windows devices tend to have specific patterns in their network communication, different from what you’d see with a Linux machine. A network scanning tool can analyze these patterns, figure out which operating system the device is running, and use that information to classify the device more accurately.
By identifying the OS, tools can also point out any vulnerabilities related to specific versions of the OS. This is crucial for security assessments since different OS versions have different security profiles.
4. Service and Application Identification
Along with identifying the OS, network scanning tools can also figure out what applications and services are running on a device. Every application on a device that communicates over the network usually exposes a service. A web server might expose HTTP, a printer might expose printing services, and a file-sharing device might expose FTP.
The network scanning tool probes these services and examines their response. For example, a device might respond to an HTTP request with a banner that says “Apache HTTP Server.” This immediately tells the scanning tool that the device is running a web server. On the other hand, if the tool identifies the service as "CUPS" (Common Unix Printing System), it knows the device is probably a printer.
This step gives the scanning tool even more information about what the device does and helps narrow down the possible device types.
5. Device Behavior Analysis
Here’s an interesting aspect: some tools don’t even need to directly communicate with the device to figure out what it is. They can look at the behavior of the device on the network.
For example, some devices send periodic location updates, like smartphones. Others, like printers, might send frequent status updates to the network. By watching these behaviors, network scanning tools can identify the device’s role based on its patterns.
This method is particularly useful when scanning IoT (Internet of Things) devices, which may not respond to traditional scanning techniques. Analyzing how they interact with the network helps determine what they are without direct interaction.
6. MAC Address Lookup
Each device on a network also has a unique identifier called a MAC address. Think of it as a serial number for network interfaces. While the MAC address alone doesn’t tell you the device type, the first part of the MAC address can give clues about the manufacturer.
The first three bytes of the MAC address are assigned to the device’s manufacturer. For example, a MAC address starting with “00:1A:2B” could belong to Apple. This doesn’t tell you whether the device is a laptop, phone, or printer, but it helps narrow down the possibilities.
Below is a table showing some common MAC address prefixes (the first 3 bytes of a MAC address) that can help identifying device types or manufacturers. These prefixes are assigned to device manufacturers by the IEEE (Institute of Electrical and Electronics Engineers).
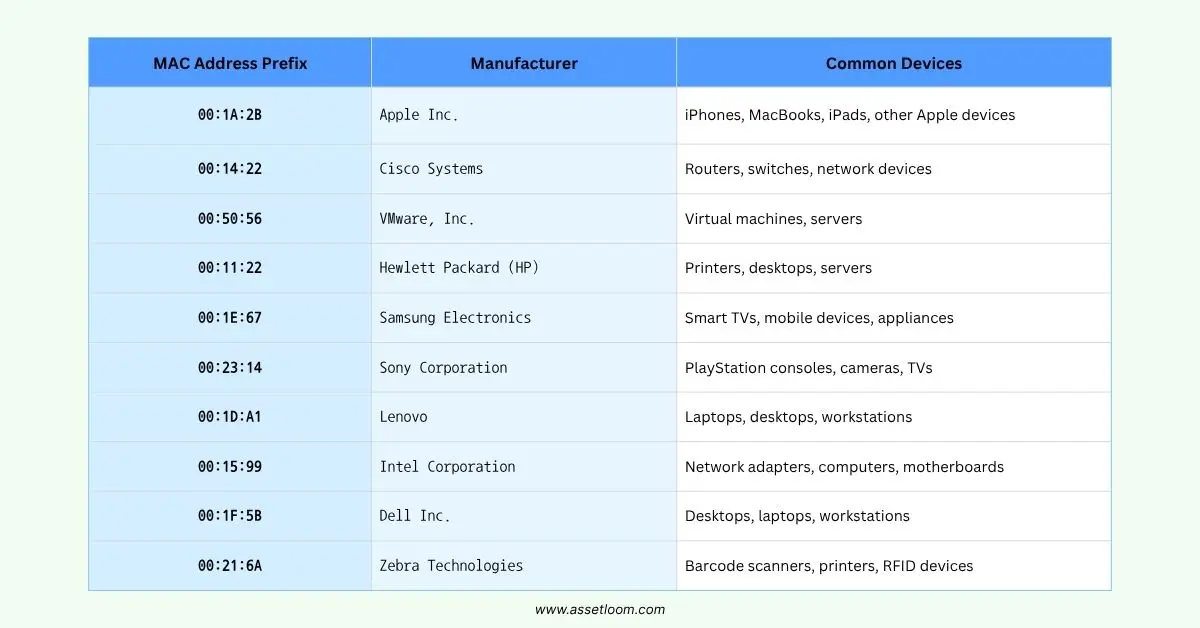
Using this information, network scanning tools can get a better sense of the type of device they’re dealing with.
7. Traffic Pattern Recognition
Finally, network scanning tools can identify device types by analyzing traffic patterns. Each type of device has its own unique communication style. For example, a device sending out small, frequent packets might be a sensor or an IoT device. A server or media device might send larger, burst-like packets.
By observing how devices communicate with the network, scanning tools can often identify the type of device based on its traffic patterns. This method is especially useful for identifying devices that don’t respond well to traditional scanning techniques, like IoT devices.
Conclusion
Network scanning tools are powerful tools for identifying devices connected to a network. They scan IP addresses, probe open ports, perform OS fingerprinting, and analyze network traffic. Each method gives more insight into the device’s type, helping network administrators classify and monitor devices efficiently.
These tools play a critical role in asset discovery and network security. By understanding how they work, you can better manage your network, keep devices secure, and ensure that only authorized devices are allowed to connect.
Whether you’re running a small home network or managing a large enterprise, network scanning tools are essential for maintaining a safe and well-organized network. By identifying device types and behaviors, these tools make it easier to protect your network from potential threats and ensure that it’s running smoothly.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


