What Do Most Corporations Do With Returned Computers?
Learn how corporations manage returned computers through IT inventory processes, ITAM workflows, and lifecycle management.
When an employee leaves a company or gets a laptop upgrade, their computer comes back to the IT team. On the surface, it seems simple—collect the device and hand it to someone else later. In reality, returned computers create a lot of work. They hold sensitive company data, they cost thousands of dollars over their lifetime, and they need to be tracked carefully in the inventory.
If returned devices are not managed properly, they can pile up in storage rooms, get misplaced in records, or worse, still carry data that should have been erased. For IT teams, the real task is not just taking the laptop back but making sure it is cleaned, recorded in the system, and either reused, stored, or retired in the right way. So the question is: what do most corporations actually do with these returned computers?
1. Returned Computers in the ITAM Lifecycle
A computer isn’t just a piece of hardware to the IT department. It’s an asset that has been tracked from the moment it was purchased. When it’s returned, that’s another step in its lifecycle.
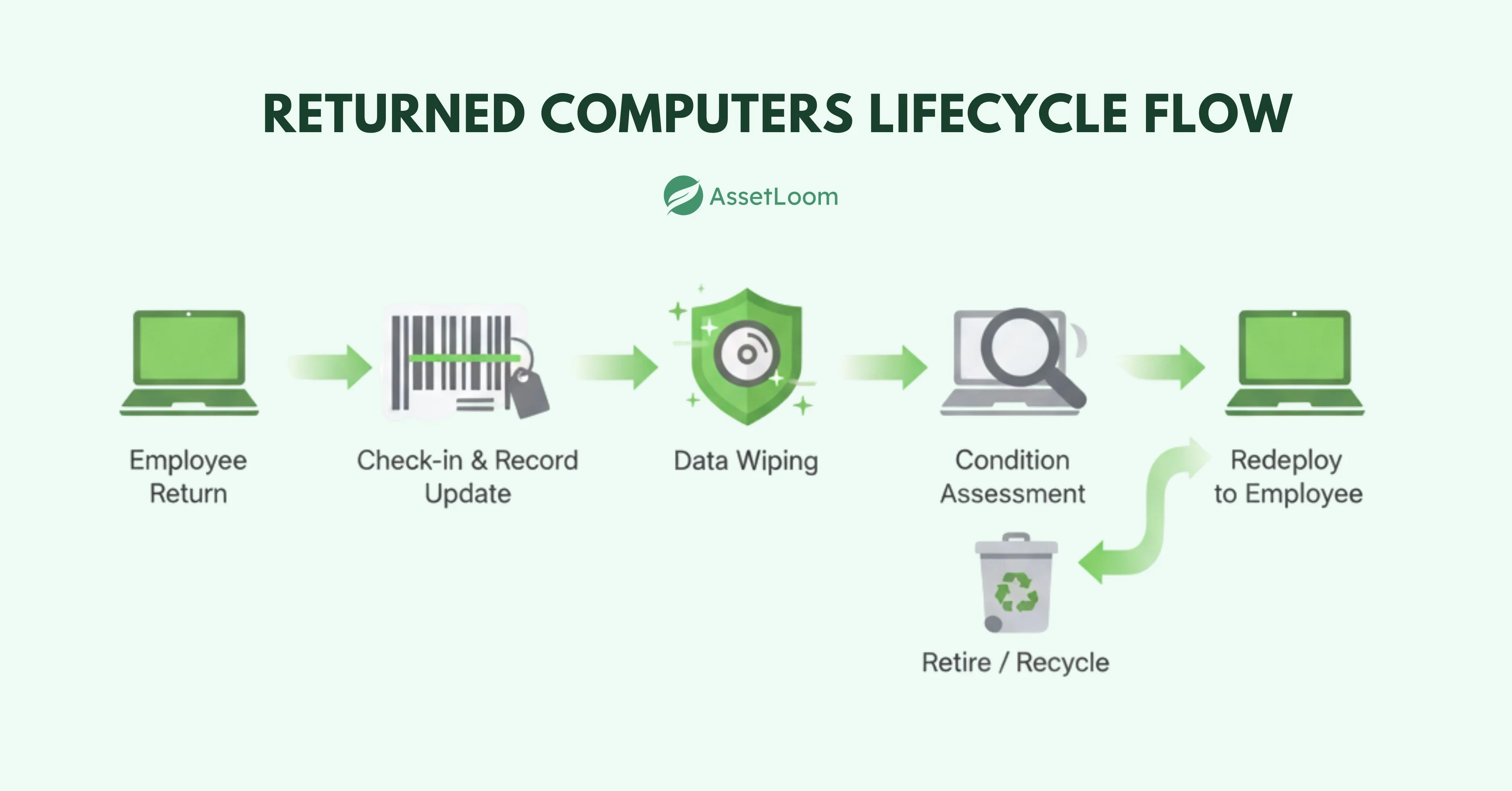
Computers usually come back in a few situations:
- An employee leaves the company and turns in their laptop
- The hardware is being refreshed because of age or performance issues
- A device is replaced under warranty
Each of these moments adds work for IT teams. The return needs to be recorded in the inventory system so the asset doesn’t become a “ghost” device that exists in the books but no one can find physically. From there, decisions have to be made: is the machine still good enough to redeploy, should it be sent for repair, or has it reached the end of its useful life?
Returned computers aren’t the end of the story, they’re just moving into another stage in the lifecycle. How well that stage is handled often depends on how strong the company’s IT asset management practices are.
2. Common IT Inventory Actions for Returned Computers
Once a computer is handed back, IT teams usually follow a series of steps to make sure it’s secure, properly logged, and ready for its next stage. These steps vary depending on company policies, but most corporations have a process that looks something like this:
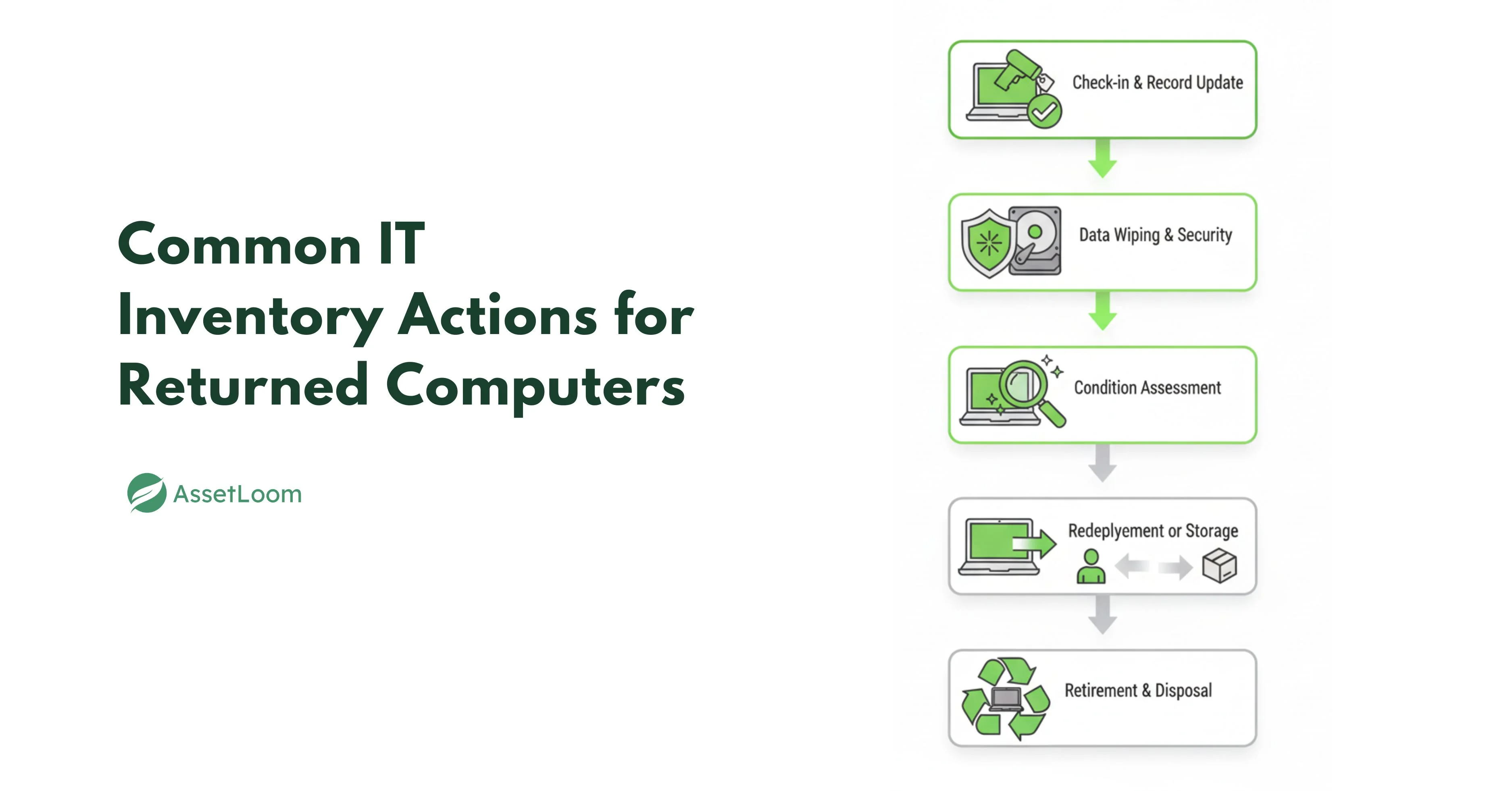
Read also: IT Inventory Management: Best Practices for IT, Finance, Security
Check-in and Record Update
When a computer is handed back, the first step is always confirming that it’s officially returned.
Most companies use asset tags, barcodes, or serial numbers to identify each machine. The IT team scans or enters that number, and the system updates the asset’s status. For example, it might move from “Assigned to Employee” to “Returned” or “Pending Review.”
Doing this right away prevents problems later. If the computer isn’t checked in, it can still show as “in use” under the employee’s name, even though it’s sitting in a storage cabinet. That creates a “ghost asset,” which throws off reports, budgets, and audits.
Some organizations also connect this step with HR offboarding. When HR closes out an employee, the IT system automatically prompts staff to confirm whether the laptop was returned. This link between departments helps avoid missed devices.
Data Wiping and Security
After a computer is checked in, the next step is clearing out the data. Returned machines almost always hold sensitive information—emails, documents, saved passwords, and even cached files that users forget about. Leaving that data untouched is a major security risk.
Most corporations use certified wiping tools that overwrite the hard drive multiple times, making it impossible to recover the old data. This is very different from just deleting files or doing a quick reset, which can often be reversed. Some organizations go further by keeping digital certificates of the wipe. These certificates can be attached to the asset record in the IT system as proof that the process was done correctly.
In higher-security industries, some companies even remove the hard drive and destroy it physically. That way, there’s zero chance of data being recovered. While more extreme, it’s a common approach in finance, healthcare, or government environments.
The key point is that wiping isn’t optional. Every computer that comes back must go through this step before it’s reused, stored, or recycled. It protects the company’s information, the employee’s privacy, and ensures compliance with regulations like GDPR or HIPAA.
Read also: IT Asset Management Certifications That Employers Look For
Condition Assessment
Once the data has been securely wiped, the computer goes through a condition check. This step helps the IT team figure out what to do next with the device.
The assessment usually covers a few areas:
- Physical inspection: checking for cracks, broken screens, missing keys, or signs of heavy wear.
- Performance check: powering it on, running quick tests, and seeing if it can still handle standard company software.
- Warranty status: looking up whether the device is still under manufacturer coverage, which could make repairs easier or free of charge.
- Repair costs: estimating how much time and money it would take to fix any issues, compared to buying new equipment.
All of this information is logged into the IT asset management system. For example, the device’s record might be updated with notes like “Good condition – ready for redeployment” or “Battery replacement required.”
This step is important because it prevents IT from redeploying faulty machines or wasting money repairing devices that should be retired. It also creates a clear record that can be used later for audits or budget planning.
Redeployment or Storage
If a returned computer is still in good condition, the most cost-effective option is usually to put it back into service. Redeployment can save a company thousands by extending the life of existing devices instead of purchasing new ones.
Before redeployment, IT teams often:
- Reinstall the standard operating system and company software
- Apply the latest security updates
- Replace small parts if needed, like a battery or keyboard
- Give the device a new asset tag if the old one is damaged
Once ready, the device can be reassigned to a new employee. In many organizations, the ITAM system tracks this automatically. For example, the asset’s status moves from “In Stock” to “Assigned,” and the new user is linked to that machine in the record.
Not every computer is redeployed immediately. Sometimes devices are kept in storage until they’re needed. In this case, the inventory must show exactly where the computer is—such as “Storage Room A, Shelf 2”—so it doesn’t go missing or get counted as lost.
Redeployment and storage might seem like simple steps, but they’re where many organizations lose track of assets. Clear documentation in the IT system makes sure every device is accounted for, whether it’s back on a desk or waiting in a cabinet.
Retirement and Disposal
Not every computer is worth keeping. Some are too old to run current software, too costly to repair, or simply at the end of their useful life. In these cases, companies move them into retirement or disposal.
The first step is updating the IT asset record. The status is changed to something like “Retired,” “Disposed,” or “Decommissioned.” This makes it clear that the device is no longer active and prevents it from showing up in reports as if it’s still being used.
From there, companies usually choose one of two paths:
- Recycling – The device is sent to a certified e-waste recycler. These vendors break down the hardware safely, recover valuable materials, and handle toxic components in line with environmental regulations.
- Physical destruction – In some cases, especially for devices with highly sensitive data, companies may shred or crush the hardware. Certificates of destruction are often provided by vendors, and these documents are attached to the asset record for compliance purposes.
Retirement isn’t just about getting rid of old machines—it’s about doing it responsibly. If a company skips proper disposal, it risks data leaks, environmental penalties, and gaps in its audit trail. That’s why most organizations document every step of the process, from the final inventory update to the recycling or destruction certificate.
Handled correctly, retirement closes the loop in the computer’s lifecycle and ensures the company has both a clean inventory and a secure data record.
3. Risks of Mishandling Returned Computers
When returned computers aren’t handled properly, problems can build up quickly. What seems like a small oversight—forgetting to log a laptop or delaying a data wipe—can lead to bigger issues across the company. Some of the most common risks include:
Ghost Assets
A laptop that was returned but never updated in the system may still show as “in use.” These ghost assets make reports inaccurate, complicate audits, and mislead finance teams about how many devices the company actually owns.
Data Breaches
If returned computers still contain old files or accounts, they pose a serious risk. A misplaced device with sensitive data could expose the company to compliance violations, financial penalties, or damage to reputation.
Audit Failures
Auditors often check disposal and lifecycle records. Missing certificates for data wiping or recycling can cause red flags, leading to fines or extra scrutiny.
Unnecessary Costs
Holding on to outdated or broken computers without proper records increases storage costs and clutters the inventory. At the same time, failing to reuse good devices forces the company to spend money on new hardware it doesn’t really need.
These risks are why most corporations build detailed return workflows and connect them directly to their IT asset management system. It keeps the inventory reliable, protects data, and avoids unnecessary expenses.
4. ITAM Best Practices for Returned Computers
Handling returned computers doesn’t have to be complicated, but it does require consistency. Companies that manage this stage well usually follow a clear set of practices tied directly into their IT asset management process.
A standard return workflow is the first step. Every computer should pass through the same cycle:
- Check in and log the return in the system
- Wipe the data securely
- Assess the condition and record findings
- Redeploy if usable, or retire if it’s at end-of-life
Keeping the inventory system updated is just as important. For example, if a laptop is checked in but its record still shows “Assigned to Employee,” reports will be misleading and may cause problems during audits. Updating the record right away prevents these ghost assets from appearing.
Compliance evidence should also be stored with each asset record. Typical examples include:
- A data-wipe certificate proving secure erasure
- A recycling receipt from a certified vendor
- A destruction certificate if hardware is physically destroyed
Some companies make the process smoother with automation. For instance, when HR marks an employee as offboarded, the ITAM system can automatically trigger a task reminding IT to collect and check in the laptop. Barcode scanners also make it faster to update asset records.
Finally, lifecycle metrics give a big-picture view. Tracking numbers like “70% of laptops redeployed” versus “30% retired” helps IT and finance teams understand how long devices last and when refresh cycles should happen.
With these practices in place, returned computers are handled predictably, risks are reduced, and the inventory stays accurate.
Conclusion
Returned computers are a normal part of corporate life, but how they are handled makes a big difference. Each device represents both a security risk and a financial investment. If returns are managed through a clear ITAM process, companies can protect data, avoid ghost assets, and get the most value from their hardware.
FAQs
What happens to company laptops when an employee leaves?
Most companies require the laptop to be returned during offboarding. IT then checks it back into the inventory system, wipes the data, and either redeploys it to another employee or retires it if it’s too old.
Can returned computers be reused?
Yes. If the device is in good condition, it can be refurbished, updated, and assigned to another employee. This saves money and extends the asset’s lifecycle.
How do companies make sure data is erased from returned computers?
They use secure wiping tools that overwrite the drive, often with a certificate as proof. In high-security industries, some organizations physically destroy the drives.
What if a computer is too old or broken to reuse?
It’s usually marked as “Retired” in the asset management system and sent to a certified recycler. Some companies also receive a disposal or destruction certificate for compliance records.
Why is tracking returned computers important?
If a device isn’t logged properly, it can become a “ghost asset,” showing up in reports as active when it’s not. This causes problems during audits and can mislead budget planning.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


