What is Unified Endpoint Management?
Unified Endpoint Management (UEM) allows IT and security teams to manage, monitor, and secure all endpoints.
Unified Endpoint Management is a centralized software platform that enables IT and security teams to monitor, manage, and secure all of an organization’s endpoints, whether on-site or remote, with one single tool. It’s a straightforward approach that enables consistent device management across all devices, no matter where they are or what system they run on.
What Makes Unified Endpoint Management So Special?
Let’s face it, endpoint management used to be a mess. You had one tool for managing mobile devices, another for desktops, and still another for laptops. This fragmented system created inefficiencies, added confusion, and, let’s be honest, introduced a whole lot of risk. Unified Endpoint Management solves this by providing one unified platform to manage all devices across various operating systems, whether they’re on-premises or in the cloud.
The need for such a solution grew exponentially as the Bring Your Own Device policy (BYOD) and hybrid workforces emerged. Employees increasingly wanted to use their own devices for work, and businesses were shifting towards remote and flexible work arrangements. With the rise of the work-from-home trend, especially during the COVID-19 pandemic, security and IT teams needed a more streamlined, robust solution to manage devices efficiently. Unified Endpoint Management became a game-changer.
The Evolution of Unified Endpoint Management: How We Got Here
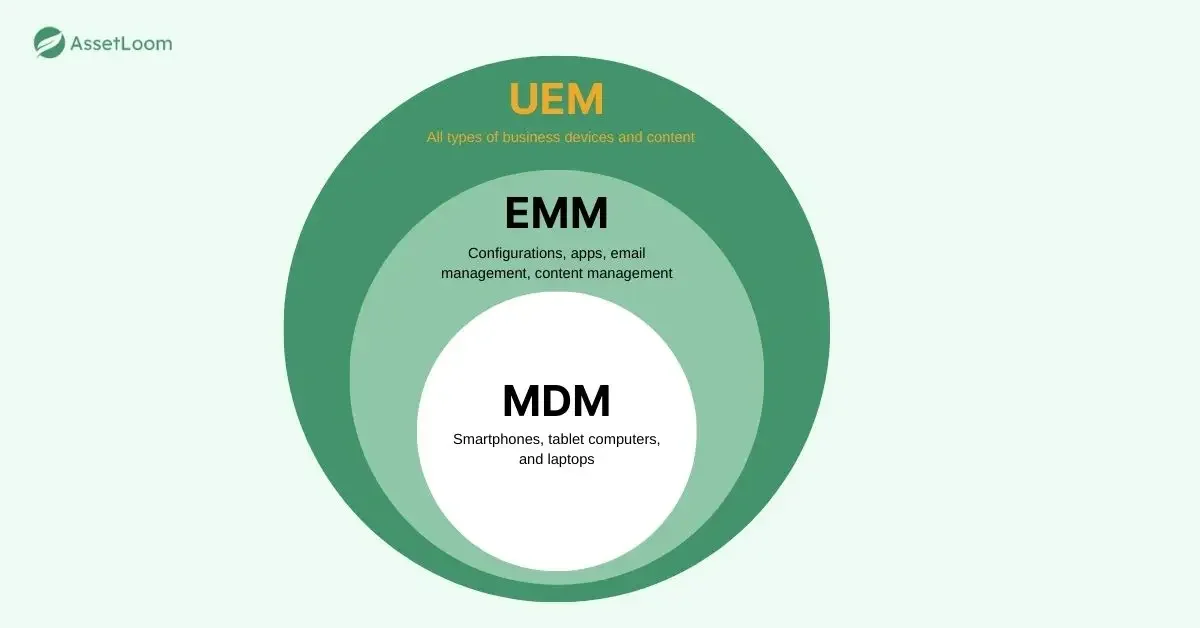
To understand why Unified Endpoint Management is so revolutionary, we need to look at how endpoint management has evolved over the past few decades. The journey from MDM to Unified Endpoint Management is both interesting and necessary:
1. MDM (Mobile Device Management):
Initially, Mobile Device Management (MDM) solutions were designed to handle company-owned mobile devices, providing IT admins with control over security, configuration, and remote management. They could wipe data remotely, track devices, and manage app installations. But when smartphones became mainstream and employees wanted to use their personal devices (BYOD), MDM had a tough time adapting.
2. MAM (Mobile Application Management):
To address the BYOD trend, MAM emerged. Instead of managing the entire device, MAM focused on securing and managing business apps on personal devices. This allowed employees to keep their personal data private while still giving IT the tools they needed to protect company data. However, MAM didn’t go far enough—there were still limitations in securing other device aspects.
3. EMM (Enterprise Mobility Management):
Next, we saw the rise of EMM, which combined MDM and MAM into one solution. It extended mobile security to laptops and tablets, providing a more comprehensive management solution for remote workers. EMM improved user experience and data security, but still couldn’t unify device management for both onsite and offsite devices.
4. UEM (Unified Endpoint Management):
Finally, UEM bridged the gap between EMM and client management tools (CMTs) used for on-premise devices. Unified Endpoint Management allows companies to manage all endpoints, whether mobile, desktop, or remote, with a single tool. And, UEM platforms now integrate with advanced endpoint security technologies like antivirus software, firewalls, and real-time threat detection systems, providing an even more comprehensive security approach.
How Unified Endpoint Management Boosts Endpoint Security
In a typical scenario, using multiple tools to manage different types of devices creates chaos for IT and security teams. It increases the risk of errors, gaps in security, and inconsistent configurations. UEM cuts through the clutter by consolidating everything into one unified system.
-
Centralized Management: UEM gives you a single dashboard to view, manage, and secure all devices across your network. This central hub not only saves time but ensures you’re not missing any critical updates or security issues, regardless of where the device is or what system it’s running.
-
Security Policy Enforcement: With UEM, security policies are no longer a hassle. You can apply consistent, automated policies across all devices—whether mobile, desktop, or IoT devices. From encryption to password rules and multifactor authentication, UEM simplifies policy enforcement and ensures everyone adheres to the same standards.
-
Automatic Updates and Patching: One of the key features of UEM is its ability to automatically scan devices for vulnerabilities and push patches when necessary. IT teams don’t have to worry about manually applying updates for every single device. UEM handles it automatically, keeping your devices up-to-date and secure.
-
App Control and Management: UEM gives you full control over which apps are allowed on company devices. You can approve or block specific apps, ensuring that only enterprise-approved software has access to corporate data. Additionally, many UEM platforms allow the creation of an enterprise app store, simplifying app distribution and updates for employees.
-
Data Isolation for BYOD Programs: With BYOD on the rise, UEM ensures that personal data and corporate data stay separate. It provides the optimal user experience while safeguarding corporate assets, ensuring data security even on personal devices.
-
Wiping and Locking Lost Devices: If a device is lost, stolen, or reaches the end of its lifecycle, UEM gives you the tools to lock it, wipe data remotely, and even track its location. This is critical for preventing unauthorized access and keeping your sensitive data secure.
Real-World Benefits of UEM
So, why should your business implement UEM? Here are some of the key use cases:
- Simplified Regulatory Compliance: Regulatory compliance can be a nightmare with hybrid workforces, but UEM makes it easier. It enables you to enforce encryption policies and control access to regulated data, helping you comply with regulations like GDPR and HIPAA.
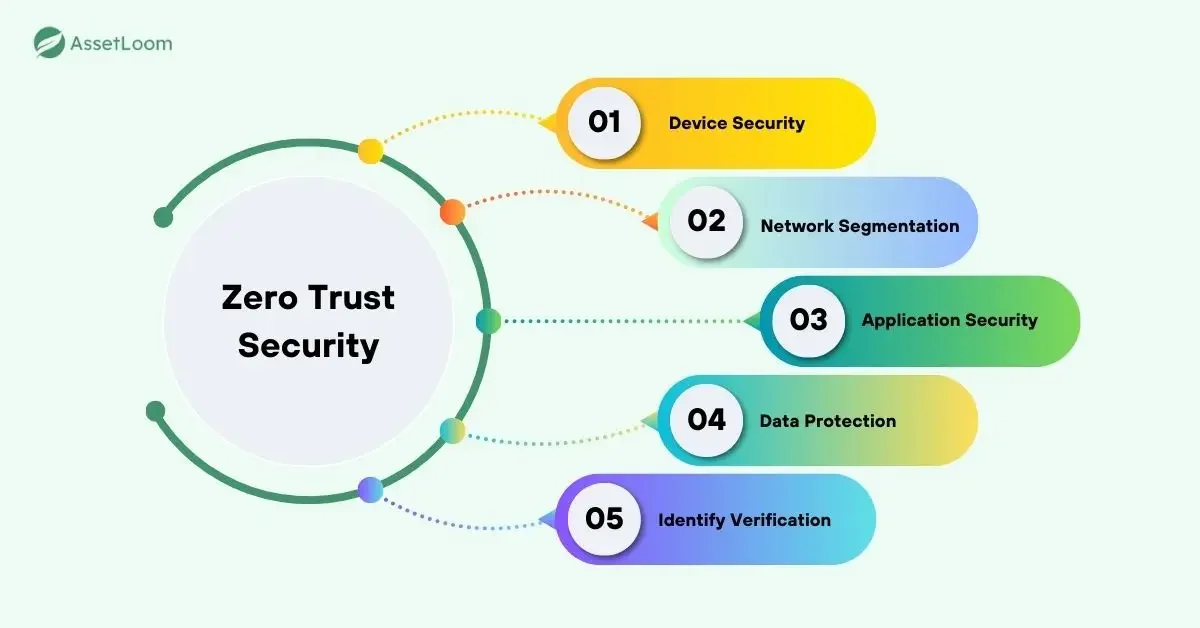
- Zero Trust Security: Zero Trust models are becoming more popular, and UEM supports this approach by providing visibility into all devices accessing your network. It ensures that only authorized devices and users can connect to your system, continuously verifying each entity’s access level.
- Improved Employee Productivity: With UEM, employees can securely use their personal devices for work, without the risk of compromising corporate data. UEM enables seamless BYOD programs while maintaining security standards, resulting in happier, more productive employees.
- Enhanced IT Efficiency: By consolidating device management into a single platform, UEM reduces administrative overhead and streamlines processes for IT teams. Tasks that once required multiple tools and manual interventions can now be automated, saving valuable time and resources.
The Future of UEM: What’s Next?
UEM technology is rapidly evolving, and the future looks promising. As IoT devices become more prevalent, UEM will need to scale to manage and secure these devices as well. The integration of AI and machine learning will likely play a bigger role in automating threat detection and response, improving security even further.
With the rollout of 5G, the number of connected devices is expected to skyrocket, which means UEM platforms will need to be even more agile and capable of handling the influx of new endpoints in real time.
Conclusion
If you’re still managing your endpoints with separate tools for mobile devices, desktops, and remote workers, it’s time for a change. UEM brings everything together, making your endpoint security more efficient, less error-prone, and easier to manage. Whether you’re dealing with BYOD, remote workers, or regulatory compliance, UEM is the solution to the challenges of modern device management.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox


