Laptop Tracking Software: Top 5 Must-Have Features
Laptop tracking software keeps your device safe. Discover 5 powerful features for this hardware asset tracking solution to ensure security.
Laptops are now inevitable for work, education, and personal use. This also means that losing a laptop is terrifying, as it can result in significant financial and data security risks. This is where laptop tracking software comes in.
The purpose of laptop tracking tools is to offer users peace of mind by helping locate, manage, and secure their devices. For businesses, such software doubles as a tool for hardware asset management and IT asset management, ensuring efficient tracking of company-owned devices.
Choosing the right laptop tracking software requires understanding the key features that make it effective. In this article, we’ll explore five must-have features, explaining how they work and why they matter. Whether you’re an individual user or an IT manager, these insights will help you pick a solution that meets your needs.
![]()
1. Real-Time Location Tracking
Real-time location tracking is the core feature of any laptop tracking software. It uses GPS, Wi-Fi triangulation, or IP address data to pinpoint your laptop’s location. Once installed, the software runs in the background, periodically sending location updates to a secure cloud server. Users can access this data through a web portal or mobile app, viewing their laptop’s location on a map in real time.
If a laptop is stolen or misplaced, the software can provide precise coordinates, helping you or law enforcement recover it. Some advanced solutions even allow you to set geofencing alerts, notifying you if the laptop leaves a designated area.
Why It Matters?
Real-time tracking ensures you can act quickly in case of loss or theft. For businesses managing multiple devices, this feature supports hardware asset management by keeping tabs on where laptops are at all times, whether they’re with remote employees or in the office. It minimizes downtime and reduces the risk of unauthorized use.
2. Remote Lock and Wipe Capabilities
Remote lock and wipe features allow you to secure your laptop’s data if it’s lost or stolen. Through the software’s online portal, you can send a command to lock the device, requiring a password to regain access. If recovery seems unlikely, you can initiate a remote wipe, which erases all data on the laptop, preventing unauthorized access to sensitive information.
These features rely on the software maintaining an active internet connection with the laptop. Even if the device is offline, the command is queued and executed as soon as it connects to the internet.
Why It Matters?
Data breaches can be catastrophic, especially for businesses handling customer information or proprietary data. Remote lock and wipe capabilities protect your privacy and comply with data protection regulations. This feature ensures that company data remains secure, even if a device is no longer in your possession.
3. Activity Monitoring and Screenshots
Activity monitoring tracks how a laptop is being used, capturing details like websites visited, applications opened, and files accessed. Some laptop tracking software also takes periodic screenshots or records keystrokes, storing this data securely for review. This feature is particularly useful for businesses that need to ensure employee laptops are used appropriately.
The software operates discreetly, and users typically can’t disable it without administrative privileges. Data is encrypted and sent to a centralized dashboard, where IT managers or individual users can analyze it.
Why It Matters?
For individuals, activity monitoring can help identify unauthorized access if someone else uses your laptop. For organizations, it’s a critical part of hardware asset management, ensuring devices are used for their intended purposes. It also aids in troubleshooting technical issues by providing a record of recent activity.
4. Anti-Theft Alerts and Recovery Tools
Anti-theft features in laptop tracking software include alerts triggered by suspicious activity, such as multiple failed login attempts or the laptop being powered on in an unfamiliar location. Some solutions take it a step further by capturing photos or videos using the laptop’s webcam when unauthorized access is detected. These images are sent to the software’s server, helping identify the thief.
Recovery tools may also include a “lock screen message” feature, where you can display a custom message on the laptop’s screen, urging the finder to return it and providing contact details.
These features increase the chances of recovering a stolen laptop while deterring thieves from using or selling it. For businesses, they enhance IT asset management by reducing the financial impact of lost devices and ensuring accountability.
5. Custody Verification
Custody verification ensures that a laptop is in the possession of its authorized user or within a trusted environment. The software authenticates the user or device through methods like biometric login, multi-factor authentication, or legal signature. It logs custody details, such as who is using the laptop, when, and where, storing this data in a secure dashboard.
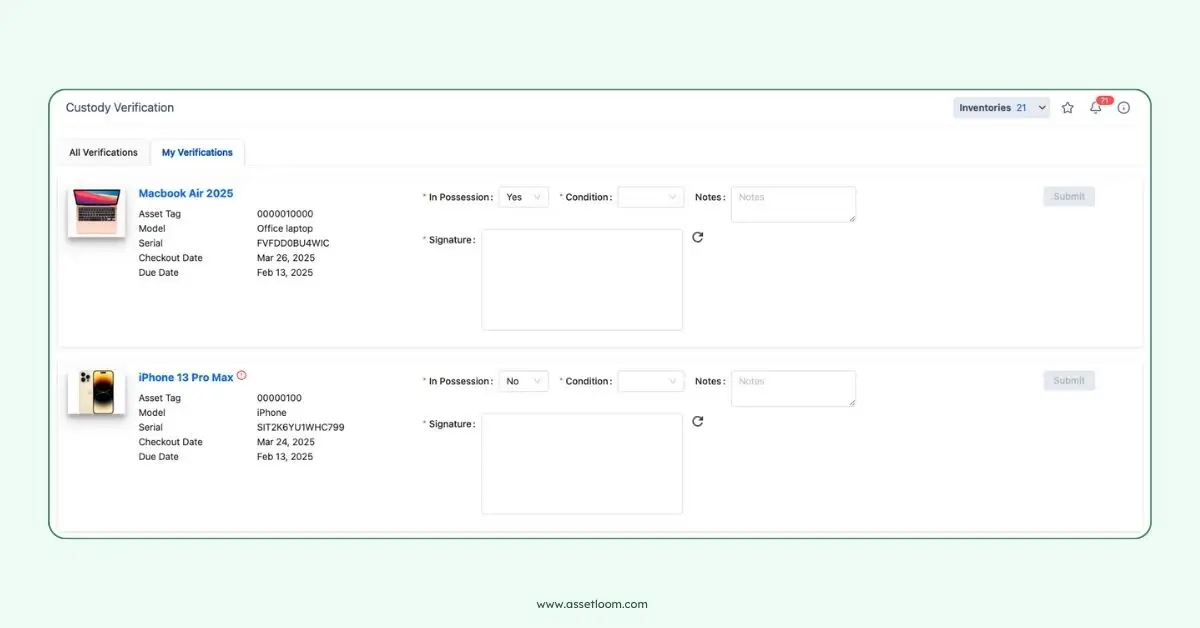
Custody Verification Request in AssetLoom
If an unauthorized user attempts to access the laptop, the software can lock the device or send an alert to the owner or IT team. For businesses, custody verification integrates with hardware asset management systems, maintaining a clear record of which employee is assigned to each laptop and flagging any discrepancies.
Why It Matters?
Custody verification is critical for preventing unauthorized access and ensuring accountability. For individuals, it adds a layer of security, confirming that only trusted users can access the laptop. For organizations, it’s a cornerstone of IT asset management, helping track device assignments and detect misuse. This feature is especially valuable for companies with remote or hybrid workforces, where laptops may be used outside the office.
![]()
It also supports compliance with data protection regulations by ensuring only authorized personnel have access to sensitive information. By maintaining a chain of custody, businesses can audit device usage and resolve disputes about who was responsible for a laptop at a given time.
Why Choose the Right Laptop Tracking Software?
Investing in laptop tracking software is a proactive step toward securing your devices and data. Whether you’re an individual protecting a single laptop or a business overseeing a fleet of devices, the right software can save you time, money, and stress. By prioritizing features like real-time location tracking, remote lock and wipe, activity monitoring, anti-theft tools, and inventory management, you ensure comprehensive protection and efficient IT asset management.
When selecting a solution, consider ease of use, compatibility with your laptop’s operating system (Windows, macOS, or Linux), and customer support quality. For businesses, scalability and integration with existing hardware asset management systems are crucial. Always read user reviews and test the software’s trial version to ensure it meets your needs.
Conclusion
Laptop tracking software is more than just a tool for finding lost devices. It’s a complete solution for securing data, managing assets, and maintaining peace of mind. By focusing on the five features discussed, whether for personal use or IT asset management, the right software empowers you to protect your laptops and stay in control.
For more information on laptop tracking software, explore trusted providers and compare their features to find the perfect fit. Don’t wait until it’s too late, secure your devices today.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


