Cloud Security Best Practices: Strengthening Your ITAM Process
Learn how to secure your cloud assets with cloud security best practices in your ITAM process. Discover simple steps to reduce risks.
Cloud computing powers modern businesses, offering flexibility and scalability for data storage, applications, and operations. However, the dynamic nature of cloud environments introduces security risks like data breaches, misconfigurations, and unauthorized access. Using cloud security best practices in your IT Asset Management (ITAM) process keeps your cloud assets safe and compliant.
This article explains how to secure your cloud assets with simple, clear steps and real examples.
What Is ITAM, and Why Is Cloud Security Important?
ITAM tracks and manages IT assets like hardware, software, and cloud resources. It ensures assets are used well, licensed correctly, and securely. In the cloud, assets like storage buckets or virtual machines change often, making tracking hard. Without security, these assets are at risk. A strong Cloud asset management process protects data, meets rules like GDPR or HIPAA, and reduces risks.
Learn more about GDPR and HIPAA: Cloud Compliance
Cloud security matters because businesses rely on the cloud for critical operations. Data breaches can lead to financial losses, legal penalties, and damaged reputations. A 2023 study found that the average cost of a data breach was $4.45 million. ITAM helps by providing visibility into all assets, ensuring they are secure and compliant. By integrating security practices into ITAM, businesses can protect their cloud environment, avoid costly mistakes, and maintain trust with customers.
Keep a Full Cloud Asset Inventory
Knowing all your cloud assets is the first step to securing them. Without a complete list, you can’t protect everything. Cloud environments use many platforms, like AWS, Azure, or Google Cloud, so manual tracking is tough. Tools like AWS Config or Azure Resource Manager find assets automatically, such as databases or virtual machines. AssetLoom scans networks to list all assets, including SaaS apps, in real time. These tools provide real-time visibility, ensuring no asset goes unnoticed.
For example, a global retail company used AWS Config to discover over 200 untracked S3 buckets containing customer data. By identifying these assets, the company applied encryption and access controls, preventing potential data leaks. A 2021 IBM Security report noted that 43% of organizations lack visibility into their cloud assets, increasing the risk of shadow IT, unauthorized cloud services used by employees. A robust inventory integrated into the ITAM process mitigates this risk by bringing all assets under management, enabling organizations to secure them effectively.
Learn more: CMDB Discovery Tools: What They Are and Why Your IT Team Needs One
Control Access with Least Privilege
Limiting who can access cloud assets prevents unauthorized use. The least privilege rule gives users only the access they need. A notable example is the 2019 Capital One data breach, where overly permissive IAM roles allowed attackers to access 100 million customer records. By contrast, a healthcare provider used Azure Active Directory to limit patient data access to only the needed staff. Incorporating least privilege into ITAM involves mapping access policies to each asset in the inventory. This ensures that permissions are consistently monitored and updated as part of the asset management lifecycle.
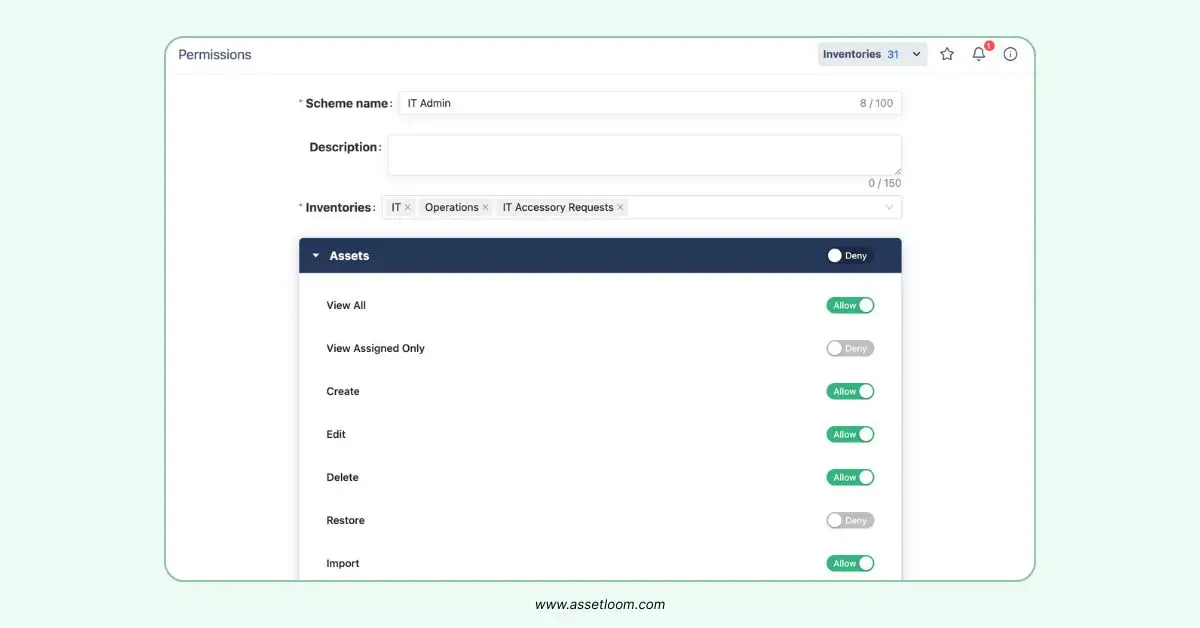
AssetLoom's permission settings, showing how to configure role-based access controls to ensure only authorized users access specific IT assets
Automate Compliance Checks
Following rules like GDPR or PCI-DSS is key for cloud users. Manual checks take time and miss errors, especially in fast-changing cloud setups. Automating compliance monitoring within ITAM ensures continuous adherence to standards and faster remediation of issues.
Cloud-native tools can monitor configurations in real-time and flag non-compliant settings, such as unencrypted storage or open ports. For instance, a financial services company used AWS Security Hub to automate PCI-DSS compliance checks across its cloud infrastructure. This reduced audit preparation time by 30% and ensured all assets met regulatory requirements. By integrating compliance monitoring into ITAM, organizations can track the compliance status of each asset alongside its lifecycle, streamlining audits and reducing the risk of penalties.
Encrypt All Cloud Data
Encryption keeps data safe by making it unreadable to outsiders. It protects data in storage and during transfer. Cloud platforms offer built-in encryption and secure encryption keys. In 2023, a Google Cloud Storage bucket leaked 1TB of data because it wasn’t encrypted. They keep data safe even if the settings are wrong. Including encryption in ITAM ensures all assets are protected and checked regularly.
Add Threat Detection to ITAM
Spotting threats early stops security issues from growing. Systems can watch for problems like unauthorized logins. Linking these systems to ITAM shows which assets are at risk. A tech firm caught an attack on a virtual machine and fixed it fast. A 2022 study said early threat detection cuts breach costs by 20%. Adding threat detection to ITAM makes security part of asset management, helping you respond quickly.
Solve Common Cloud Security Problems
Cloud security in ITAM has challenges, but you can fix them. Shadow IT happens when employees use unapproved cloud tools. Automated systems find these assets to secure them. Multi-cloud setups, using different providers, make tracking complex. A central ITAM platform unifies asset views. Misconfigurations, like open storage systems, cause many breaches. Regular scans fix these issues. Addressing these problems in ITAM keeps your cloud secure.
Benefits of Cloud Security in ITAM
Using cloud security best practices in ITAM has clear benefits. It lowers risks by securing all assets, which helps meet rules and avoid fines. It gives a clear view of all cloud assets and saves money by finding unused resources. For example, a manufacturing company shut down 15% of its unused cloud assets, saving $100,000 a year while improving security.
These benefits improve business operations. Secure assets protect customer trust and prevent financial losses. Compliance avoids legal issues, especially for industries like healthcare or finance. Clear asset visibility helps IT teams make better decisions. Cost savings free up budgets for other priorities. Together, these advantages make ITAM a critical part of cloud security.
How to Start
To apply cloud security best practices in ITAM, follow these steps:
- Check your cloud assets to find security gaps.
- Use systems that work with your cloud platforms.
- Train your team on ITAM and security steps.
- Keep checking and updating your processes.
Start by reviewing your current assets. Look for untracked systems or apps. Set up automated tracking to stay current. Train staff to follow security practices, like setting strong access rules. Regularly review your ITAM process to catch new risks or changes. This keeps your cloud environment secure and compliant over time.
Conclusion
Using cloud security best practices in your ITAM process protects cloud assets and ensures compliance. A full asset inventory, least privilege access, automated compliance, encryption, and threat detection build a secure cloud setup. Begin today by checking your ITAM process and applying these practices to keep your cloud safe.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox













![Top 10 Cloud Asset Management Software for Modern Businesses [2025 Updated]](https://assetloom.com/marketing/blog/cloud-asset-management-software.png)






























![IT Asset Lifecycle Management Policy Template [Free Download]](https://assetloom.com/marketing/blog/it-asset-lifecycle-management-policy-template.webp)