How Software Asset Management Lifecycle Diagrams Boost Cybersecurity
Discover how the software asset management lifecycle diagram enhances cybersecurity to manage software assets securely and efficiently.
Cyber threats are a growing concern for businesses today. A software asset management lifecycle diagram offers a clear way to manage software while strengthening cybersecurity. This visual tool maps out the stages of software management, helping organizations spot risks and stay secure. This article explains how software asset management lifecycle diagrams (SAM lifecycle diagrams) enhance cybersecurity and provides practical tips for IT teams.
What is a Software Asset Management Lifecycle Diagram?
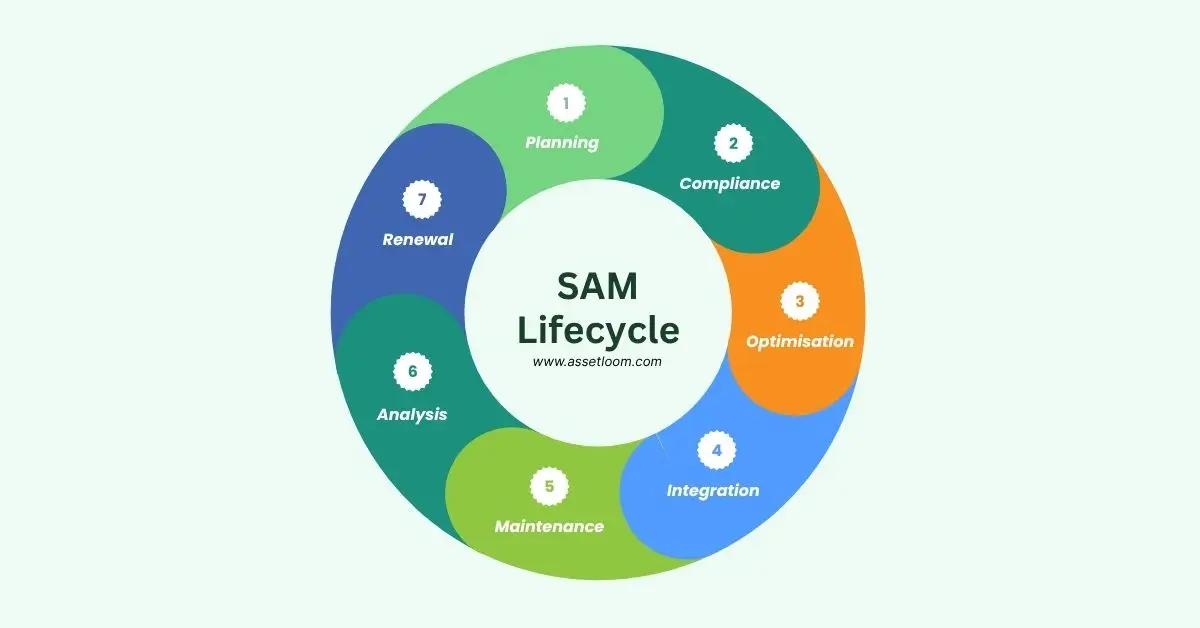
A software asset management lifecycle diagram shows the stages of managing software assets. It is often presented as a 5-step model for simplicity. This high-level view is useful for executive overviews and general understanding:
- Planning – Defining SAM policies and identifying software needs
- Acquisition – Procuring licenses and negotiating contracts
- Deployment – Installing and configuring software
- Management – Monitoring usage, optimizing licenses, and ensuring compliance
- Retirement – Decommissioning and reassigning software licenses
Download the free editable template of the software asset management lifecycle diagram here: Free Diagram Template
However, for IT teams, compliance officers, and cybersecurity professionals, a more detailed lifecycle offers better visibility and control. This expanded version breaks down the process into specific, actionable stages:
- Planning and Inventory: Defining goals and cataloging software assets.
- Verification and Compliance: Ensuring software aligns with licensing agreements.
- Optimisation: Maximizing software efficiency and cost-effectiveness.
- Integration and Automation: Streamlining SAM with automated processes.
- Maintenance and Monitoring: Continuously tracking software usage.
- Reporting and Analysis: Evaluating SAM performance with data.
- Renewal and Disposal: Managing license renewals and software retirement.
Why Cybersecurity is Critical in Software Asset Management
Cyberattacks often exploit software vulnerabilities. A 2024 report by Cybersecurity Ventures predicts global cybercrime costs will hit $10.5 trillion by 2025. Unpatched software, outdated applications, and unlicensed tools increase risks. A software asset management lifecycle diagram helps organizations track software and reduce these threats.
Related article: What is the Software Asset Management Lifecycle?
How SAM Lifecycle Diagrams Improve Cybersecurity
Each stage of the SAM lifecycle offers chances to boost security. Here’s how a software asset management lifecycle diagram protects your organization.
1. Planning and Inventory: Laying a Secure Foundation
The planning and inventory stage involves setting SAM goals and cataloging software. A SAM lifecycle diagram ensures security by:
- Identifying Assets: List all software, including versions and locations, to spot unsupported or risky applications.
- Defining Security Goals: Include cybersecurity policies, such as using only certified vendors.
- Risk Mapping: Highlight potential vulnerabilities, like untracked software.
The diagram visualizes these steps. It helps teams prioritize security from the start.
2. Verification and Compliance: Ensuring Legal Use
This stage focuses on matching software usage to license agreements. A SAM lifecycle diagram supports cybersecurity by:
- Compliance Checks: Verify licenses to avoid unauthorized software, which may contain malware.
- Audit Preparation: Document compliance status for vendor audits.
- Security Standards: Ensure software meets frameworks like NIST or ISO 27001.
For example, the diagram can include a checklist for validating licenses. This reduces risks from non-compliant software.
3. Optimisation: Reducing Security Gaps
Optimisation ensures efficient software use. A SAM lifecycle diagram helps by:
- Removing Redundant Software: Identify unused applications that could be exploited.
- Reallocating Licenses: Shift licenses to avoid over-deployment, which may lead to vulnerabilities.
- Updating Software: Highlight outdated versions needing patches.
The diagram can flag software nearing end-of-life (EOL). This prompts timely updates to close security gaps.
4. Integration and Automation: Streamlining Security
Integration and automation improve SAM efficiency. A software asset management lifecycle diagram enhances cybersecurity by:
- Automating Scans: Use tools to detect vulnerabilities in real time.
- Integrating with IT Systems: Connect SAM to security platforms like SIEM for better monitoring.
- Reducing Manual Errors: Automate compliance checks to avoid oversight.
The diagram can show how automation tools fit into the SAM process. This ensures consistent security.
5. Maintenance and Monitoring: Staying Vigilant
Continuous monitoring is key to cybersecurity. A SAM lifecycle diagram supports this stage by:
- Tracking Usage: Monitor software for unusual activity, such as unauthorized access.
- Patching Regularly: Highlight the need for timely updates to fix vulnerabilities.
- Auditing Assets: Schedule regular inventory checks to maintain accuracy.
For instance, the diagram can include alerts for EOL software. This ensures proactive risk management.
6. Reporting and Analysis: Measuring Security Success
Reporting and analysis evaluate SAM effectiveness. A SAM lifecycle diagram aids cybersecurity by:
- Tracking Metrics: Visualize compliance rates, patch status, and cost savings.
- Identifying Trends: Spot patterns, like frequent use of risky software.
- Informing Decisions: Use data to prioritize security investments.
The diagram can display key metrics, such as the percentage of compliant software. This guides strategic planning.
7. Renewal and Disposal: Securing the End of the Lifecycle
This stage manages license renewals and software retirement. A SAM lifecycle diagram ensures security by:
- Secure Disposal: Outline steps to remove data from retired software.
- License Renewal Checks: Verify new agreements for security compliance.
- EOL Management: Identify unsupported software to prevent exploitation.
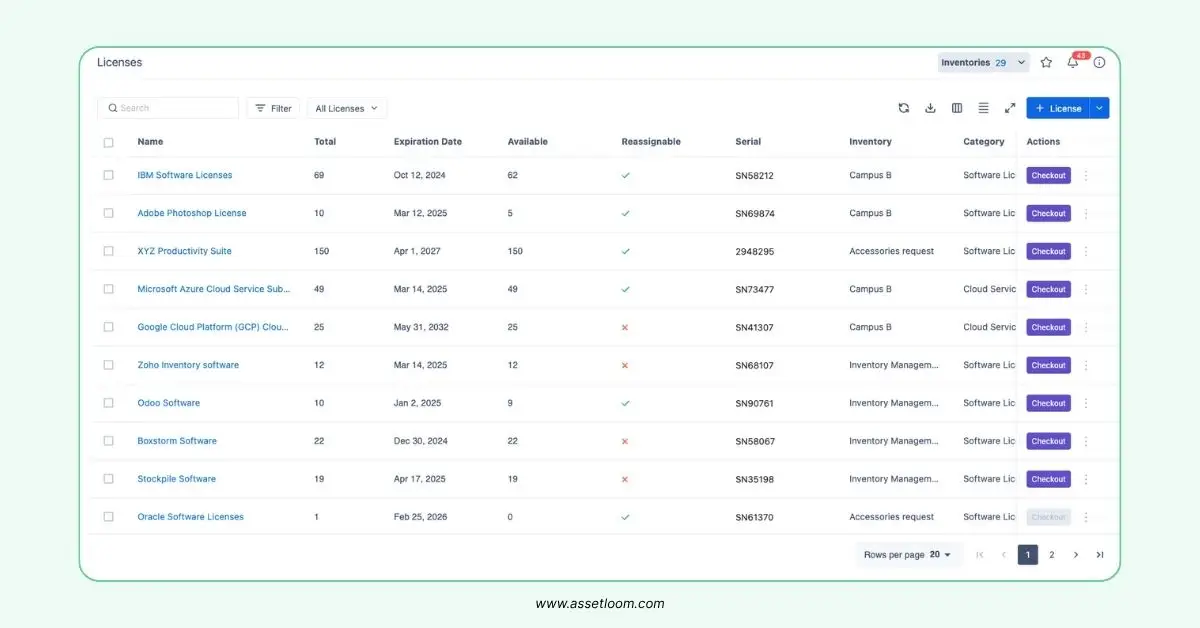
AssetLoom manages the software asset management lifecycle by providing a license renewal alert threshold.
The diagram can include a checklist for secure decommissioning. This prevents data leaks from retired assets.
Why This Lifecycle Enhances Cybersecurity
When organizations follow the software asset management lifecycle diagram, they:
- Control who gets access to software
- Ensure only approved, secure apps are used
- Maintain full visibility of active software
- Remove unused or vulnerable applications
- React quickly to issues through monitoring and reports
Case Study: Boosting Security with a SAM Lifecycle Diagram
A mid-sized healthcare provider faced compliance issues due to untracked software. By using a software asset management lifecycle diagram, they:
- Found Risks: Identified 15% of software as EOL, posing security threats.
- Improved Patching: Reduced vulnerabilities by 30% in four months.
- Ensured Compliance: Avoided $80,000 in fines by tracking licenses.
- Cut Shadow IT: Trained staff, reducing unauthorized software by 40%.
This case highlights the diagram’s role in strengthening cybersecurity.
Conclusion
A software asset management lifecycle diagram is a powerful tool for cybersecurity. It guides teams through each stage of software management, from planning to disposal. Highlighting risks and security tasks helps organizations stay compliant and secure. Whether you’re a small business or a large enterprise, this diagram protects your digital assets.

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox














![Top 10 Cloud Asset Management Software for Modern Businesses [2025 Updated]](https://assetloom.com/marketing/blog/cloud-asset-management-software.png)


























![IT Asset Lifecycle Management Policy Template [Free Download]](https://assetloom.com/marketing/blog/it-asset-lifecycle-management-policy-template.webp)