IT Asset Management Policy Explained: How to Create with AI
Create an IT asset management policy with AI. Step-by-step guide, template, and best practices to streamline ITAM.
Without a clear IT asset management policy, even the most advanced IT teams struggle to keep up with today’s complex, fast-evolving tech environments. From laptops and SaaS subscriptions to cloud infrastructure and mobile devices, assets are multiplying—and so are the risks.
Untracked assets lead to security gaps, compliance issues, and unexpected costs. Shadow IT sneaks in. Ownership becomes unclear. And when audits hit, it’s a scramble.
The solution? A strong, scalable IT asset management policy—and AI can help you create one faster than ever.
In this post, we’ll explore what an IT asset management policy really is, why it’s essential, and how to use AI tools to build smarter, more adaptive policies that keep your asset ecosystem under control.
What is an IT Asset Management Policy?
An IT asset management policy is a formal document that defines how your organization tracks, manages, and governs its IT assets throughout their lifecycle—from acquisition to disposal.
It serves as a foundation for consistency, helping teams stay aligned on asset responsibilities, usage standards, and compliance requirements. Without it, IT operations can quickly become fragmented and reactive.
A typical IT asset management policy covers:
- Scope of assets: What counts as an IT asset (hardware, software, cloud services, etc.)
- Roles and responsibilities: Who owns what? Who’s accountable for updates, audits, and approvals?
- Lifecycle processes: Guidelines for procurement, deployment, maintenance, and decommissioning
- Usage standards: Policies on acceptable use, security, and access control
- Compliance and audits: Rules for ensuring regulatory and licensing compliance
Think of it as your playbook for asset governance. It provides clarity, reduces guesswork, and ensures every asset is tracked and managed efficiently—no matter how complex your environment becomes.
Detailed Outline for an IT Asset Management Policy
Whether you're drafting from scratch or improving an AI-generated version, having a clear outline ensures your IT asset management policy is thorough, practical, and aligned with industry standards like ISO/IEC 19770.
This outline provides a comprehensive structure for an IT Asset Management (ITAM) policy. The level of detail within each section can be adjusted based on the organization's size, complexity, and specific needs.
I. Introduction and Purpose
-
1.1 Purpose
- Define the purpose of the IT Asset Management (ITAM) Policy.
- Example: To establish guidelines for the effective management, tracking, and protection of IT assets to optimize their use, ensure compliance, and reduce risks.
-
1.2 Scope
- Specify the scope of the policy (e.g., applies to all IT assets, including hardware, software, and data, owned or managed by the organization).
- Include all departments, employees, contractors, and third parties interacting with IT assets.
-
1.3 Objectives
- Ensure accurate inventory tracking.
- Optimize asset utilization and lifecycle management.
- Ensure compliance with legal, regulatory, and contractual obligations.
- Mitigate risks related to security, data breaches, and asset misuse.
- Reduce costs through efficient procurement and maintenance practices.
II. Definitions
Define key terms used throughout the policy to ensure clarity and common understanding. Examples:
- IT Asset: Any hardware, software, cloud service, or virtual resource owned, leased, or managed by the organization.
- Configuration Item (CI): A component of IT infrastructure that is under the control of configuration management.
- Asset Owner: The individual or department responsible for the lifecycle and management of a specific IT asset.
- Custodian: The individual or department responsible for the physical security and day-to-day use of an IT asset.
- IT Asset Management System (ITAMS): The tool or system used to track and manage IT assets.
- Lifecycle Management: The stages an IT asset goes through from acquisition to disposal.
- BYOD (Bring Your Own Device): Policy regarding personally owned devices used for work purposes.
- Software License: Legal agreement governing the use of software.
III. Roles and Responsibilities
Clearly define the roles and responsibilities of individuals and departments involved in IT asset management. Examples:
-
IT Department/IT Asset Management Team:
- Developing and maintaining the ITAM policy and procedures.
- Managing the IT asset inventory and ITAMS.
- Conducting regular audits of IT assets.
- Tracking software licenses and ensuring compliance.
- Managing the acquisition, deployment, maintenance, and disposal of IT assets.
- Providing training and guidance on ITAM procedures.
-
Asset Owners:
- Ensuring proper use and security of assigned assets.
- Reporting any changes or issues related to their assets.
- Complying with licensing agreements.
- Participating in asset audits as required.
-
Custodians:
- Maintaining the physical security of assigned assets.
- Reporting any loss, theft, or damage to assets.
- Adhering to usage guidelines.
-
Finance Department:
- Managing budgets related to IT asset acquisition and maintenance.
- Tracking asset depreciation and financial reporting.
- Ensuring compliance with financial regulations related to IT assets.
-
Procurement Department:
- Adhering to ITAM policy during the acquisition of new IT assets.
- Maintaining records of purchase orders and vendor contracts.
- Negotiating favorable terms for IT asset acquisition and licensing.
-
Legal Department:
- Reviewing and approving IT asset-related contracts and licenses.
- Ensuring compliance with relevant laws and regulations.
-
Human Resources Department:
- Incorporating ITAM responsibilities into employee onboarding and offboarding processes (e.g., asset assignment and retrieval).
IV. IT Asset Lifecycle Management
Detail the processes and procedures for each stage of the IT asset lifecycle:
-
4.1 Planning and Acquisition:
- Defining requirements and specifications for new IT assets.
- Establishing procurement processes that align with the ITAM policy.
- Reviewing and approving purchase requests.
- Maintaining records of all acquisitions (purchase orders, invoices, contracts).
-
4**.2 Deployment and Implementation:**
- Standardized procedures for deploying and configuring new IT assets.
- Asset tagging and identification conventions.
- Recording asset details in the ITAMS upon deployment.
- User assignment and accountability.
-
4**.3 Usage and Maintenance:**
- Guidelines for the acceptable use of IT assets.
- Procedures for reporting and resolving asset-related issues.
- Maintenance schedules and responsibilities.
- Tracking asset location and movement.
- Software license management and compliance monitoring.
- Patch management and security updates.
-
4**.4 Retirement and Disposal:**
- Procedures for retiring and disposing of IT assets securely and in an environmentally responsible manner.
- Data sanitization and destruction methods.
- Proper documentation of asset disposal.
- Compliance with e-waste regulations.
V. IT Asset Inventory and Management System
-
5**.1 Inventory Requirements:**
- Mandatory data fields to be recorded for each IT asset (e.g., asset tag, serial number, model, manufacturer, purchase date, cost, location, user, software installed, license information, warranty details).
- Frequency and methods for conducting inventory audits (automated, manual, or a combination).
- Procedures for updating asset information in the ITAMS.
-
5**.2 IT Asset Management System (ITAMS) Usage:**
- Guidelines for accessing and using the ITAMS.
- Roles and permissions within the ITAMS.
- Procedures for data entry, modification, and reporting.
- Integration of the ITAMS with other relevant systems (e.g., procurement, service desk).
-
5**.3 Data Accuracy and Integrity:**
- Procedures for ensuring the accuracy and integrity of asset data.
- Regular data validation and reconciliation processes.
- Responsibility for data accuracy.
VI. Software Asset Management (SAM)
-
6**.1 Software Licensing:**
- Procedures for acquiring, managing, and tracking software licenses.
- Guidelines for different types of licenses (per user, per device, concurrent user, etc.).
- Procedures for ensuring compliance with software license agreements.
- Regular software license audits and reconciliation.
- Management of software subscriptions and renewals.
-
6**.2 Software Usage Monitoring:**
- Tools and techniques for monitoring software usage to optimize license utilization.
- Procedures for identifying and addressing underutilized or unauthorized software.
-
6**.3 Software Deployment and Standardization:**
- Guidelines for standardizing software deployments to simplify management and reduce costs.
- Procedures for managing software installations and removals.
VII. Security and Compliance
-
7**.1 Security of IT Assets:**
- Physical security measures for IT assets.
- Logical security controls (e.g., access controls, encryption) applied to IT assets.
- Procedures for reporting lost, stolen, or compromised assets.
- BYOD security requirements (if applicable).
-
7**.2 Regulatory Compliance:**
- Identification of relevant legal, regulatory, and contractual obligations related to IT assets.
- Procedures for ensuring compliance (e.g., data privacy, software licensing).
- Record-keeping requirements for compliance purposes.
-
7**.3 Auditing and Reporting:**
- Schedule and procedures for regular IT asset audits (internal and external).
- Reporting requirements for IT asset inventory, compliance, and cost.
- Metrics for measuring the effectiveness of the ITAM policy.
VIII. Policy Enforcement and Compliance
-
8**.1 Enforcement Mechanisms:**
- Clearly state the consequences of non-compliance with the policy.
- Identify who is responsible for enforcing the policy.
-
8**.2 Reporting Violations:**
- Procedures for reporting suspected violations of the policy.
- Protection for whistleblowers.
-
8**.3 Policy Review and Updates:**
- Schedule for periodic review and updates of the policy (e.g., annually or as needed).
- Process for proposing and approving policy changes.
- Communication of policy updates to relevant stakeholders.
IX. Exceptions to the Policy
Outline any specific exceptions to the policy and the process for requesting and approving exceptions. This should be kept to a minimum and clearly documented.
X. Contact Information
Provide contact information for the individuals or departments responsible for the ITAM policy and related inquiries.
XI. Policy Approval and Effective Date
Include signatures and dates of approval by relevant stakeholders (e.g., CIO, Legal Counsel, Senior Management).
State the effective date of the policy.
This detailed outline provides a solid foundation for developing a comprehensive IT Asset Management policy. Remember to tailor it to your organization's specific needs and ensure it is communicated effectively to all relevant personnel. Regularly review and update the policy to maintain its relevance and effectiveness.
Why Most Organizations Struggle Without One
Without a clear IT asset management policy, IT operations often run into avoidable problems—some of which can get costly, fast.
Here’s what typically goes wrong:
- No clear ownership: Assets are bought and used across departments, but no one knows who’s responsible for tracking or maintaining them. This leads to confusion, delays, and accountability gaps.
- Shadow IT and security risks: Employees install unapproved software or use unauthorized cloud tools. This opens the door to security vulnerabilities, data leaks, and compliance violations.
- Wasted spending: When assets aren’t tracked, it’s easy to lose sight of what you already have. Organizations end up paying for duplicate tools, unused licenses, or unreturned hardware.
- Poor lifecycle management: Without policies in place, assets aren’t properly maintained or retired. Outdated equipment can stay in circulation, slowing teams down and increasing support costs.
- Audit panic: Come audit time, teams scramble to gather records, verify ownership, or prove compliance—usually manually and under pressure.
In short, the absence of a policy leads to chaos, inefficiency, and unnecessary risk. That’s why creating and enforcing a smart IT asset management policy is so important—and that’s where AI can help.
How to create an IT Asset Management Policy with an AI System?
Traditionally, creating an IT asset management policy meant hours of research, manual writing, and navigating complex compliance standards. It was time-consuming—and often, the final policy sat unused because it was too generic or outdated.
That’s where AI comes in.
Modern AI systems like ChatGPT can now help IT teams draft, customize, and update IT asset management policies faster and more effectively than ever before.
How AI can help:
- Jumpstart the drafting process – AI can generate a solid first draft in minutes, based on your organization’s needs and industry standards.
- Customize for your environment – Whether you manage on-prem hardware, SaaS apps, or a hybrid setup, AI can adapt policy language to match.
- Ensure compliance alignment – AI tools can reference frameworks like ISO 19770 or ITIL to help align your policy with best practices.
- Evolve your policy as your assets change – AI can help keep policies up-to-date as your tech stack grows or regulations shift.
Key benefits of using AI for policy creation:
- Saves time – No need to start from scratch or spend weeks on revisions.
- Reduces errors – AI brings consistency and helps avoid gaps in coverage.
- Improves clarity – AI can simplify legal or technical language for broader understanding.
- Boosts adoption – A policy that’s clear and well-structured is more likely to be followed.
By combining your team’s expertise with AI’s speed and structure, you can create a policy that’s not just compliant—but practical, agile, and ready for real-world use.
Step-by-Step: Creating an IT Asset Management Policy with AI
Building a solid IT asset management policy doesn’t have to be overwhelming. With the help of AI tools, you can move faster while still creating a clear, customized, and effective policy.
Here’s a simple step-by-step process:
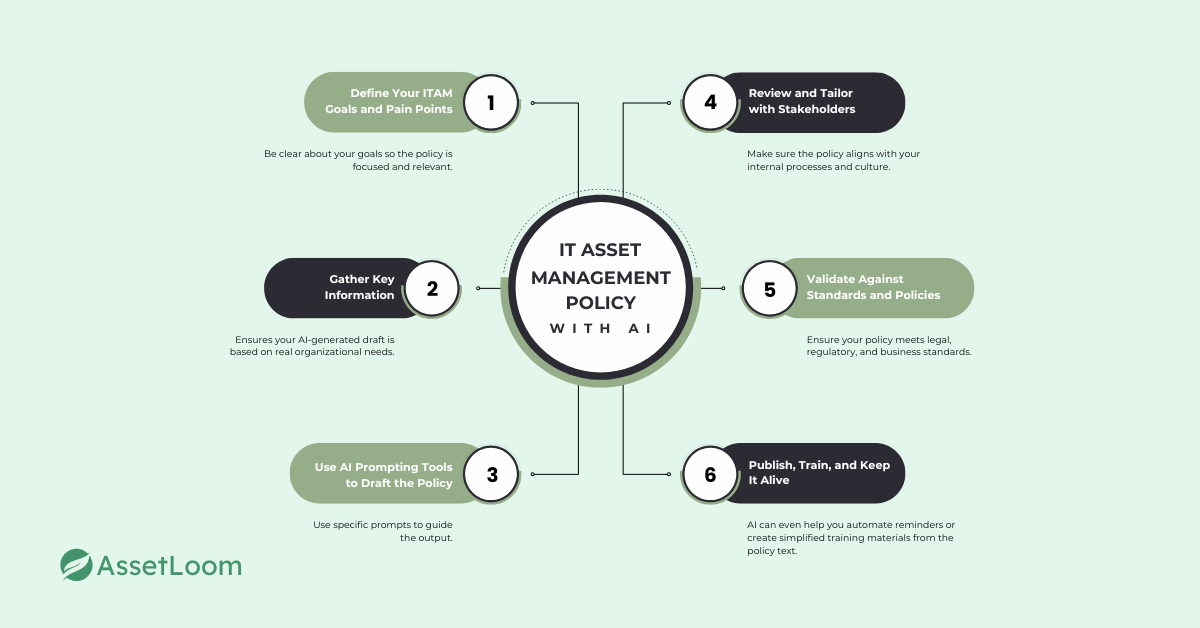
1. Define Your ITAM Goals and Pain Points
Start by identifying why you need this policy. Is it to reduce security risks? Improve cost control? Prepare for audits? Be clear about your goals so the policy is focused and relevant.
2. Gather Key Information
Before prompting an AI tool, collect:
- Types of assets you manage (hardware, software, cloud, BYOD)
- Compliance standards you follow (ISO, NIST, internal rules)
- Key roles and responsibilities
- Lifecycle processes (procurement, maintenance, disposal)
This ensures your AI-generated draft is based on real organizational needs.
3. Use AI Prompting Tools to Draft the Policy
AI tools like ChatGPT can generate policy documents quickly. Use specific prompts to guide the output.
Example prompt:
“Create an IT asset management policy for a mid-sized SaaS company that manages laptops, mobile devices, and cloud software. Include sections on roles, lifecycle management, security, and compliance with ISO 19770.”
Pro tip: The more context you give, the better the result. Include details like company size, asset types, or specific concerns.
4. Review and Tailor with Stakeholders
Use the AI-generated draft as a starting point, not a final version. Share it with IT leadership, security, procurement, and HR. Make sure it aligns with your internal processes and culture.
5. Validate Against Standards and Policies
Compare the draft with industry frameworks like:
- ISO/IEC 19770 (for ITAM structure and compliance)
- ITIL (for service management alignment)
- Internal policies (e.g., acceptable use, data protection)
Ensure your policy meets legal, regulatory, and business standards.
6. Publish, Train, and Keep It Alive
Once finalized:
- Distribute the policy to relevant teams
- Train staff on how to follow it
- Integrate with your ITAM/ITSM tools
- Set review cycles (quarterly or annually) to keep it current
AI can even help you automate reminders or create simplified training materials from the policy text.
With these steps, you’re not just ticking a compliance box—you’re building a living policy that grows with your organization.
Best Practices for Maintaining an Effective Policy
Creating an IT asset management policy is just the beginning. To stay relevant and useful, your policy needs ongoing attention. Here are the best practices to keep it active, accurate, and effective over time:
- Review Regularly: Update your policy at least once a year or when major changes occur (new assets, tools, or compliance needs).
- Match Real Processes: Make sure the policy reflects how your teams actually work. Involve IT, security, and procurement in updates.
- Keep It Simple and Accessible: Use clear language and share it in an easy-to-find place—like your ITSM portal or AssetLoom dashboard.
- Automate Where Possible: Use tools to handle asset tracking, license renewals, and lifecycle changes. AI can help keep things up to date.
- Train and Remind: Include the policy in onboarding, and send quick refreshers or updates during team meetings.
- Measure Impact: Track lost assets, compliance rates, and usage data to improve policy effectiveness over time.
When your IT asset management policy is current, visible, and tied to your day-to-day tools and processes, it becomes a powerful asset in itself—not just a document.
Conclusion
Creating an effective IT asset management policy doesn’t have to be slow or complicated—especially with the power of AI. By combining your team’s knowledge with AI tools, you can quickly draft, customize, and maintain a policy that keeps your organization secure, compliant, and cost-efficient.
The key is to treat your policy as a living document. With the right structure, stakeholder input, and support from ITAM tools, it becomes a foundation for better decision-making, smoother operations, and audit-ready governance.
Ready to turn your IT asset management policy into action? With AssetLoom, you can automate tracking, streamline lifecycle processes, and keep your policy up to date—faster and smarter.

Related Blogs
ITAM in General
Fixing Inventory Sync Issues Between ITAM and ITSM Tools

ITAM in General
The Hidden Costs of a Stolen Work Laptop & How to Prevent Them

Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom. right in your inbox