How to Track a Lost Laptop: A Guide for IT Asset Managers
Discover how to effectively track a lost laptop with asset tags, tracking software, and proven recovery strategies to secure your data and quickly locate missing devices.
How to track a lost laptop is a question many IT teams face more often than they’d like. A laptop goes missing, and suddenly there’s a scramble, checking with the user, digging through records, hoping it turns up. It’s stressful, and in many cases, it’s preventable.
For IT asset managers, keeping track of every device in the organization is already a tough job. When one disappears, the focus shifts quickly to damage control: protecting company data, reporting the loss, and figuring out what went wrong.
This guide is here to help you take control. We'll walk through why businesses keep losing devices, what to do when it happens, and how the right asset tracking system can make all the difference. By the end, you’ll be better equipped to protect your assets and prevent future losses.
Why Businesses Always Lose Laptops (and Other Assets)
Laptops get lost all the time. It happens in fast-paced offices, during remote work setups, or in the middle of a business trip. But the real issue isn’t just the device going missing, it’s the gaps in the system that allow it to happen in the first place.
One common reason is poor visibility. Without a centralized system that shows who has what, where it is, and when it was last seen, it’s easy for assets to slip through the cracks. Many teams still rely on spreadsheets or scattered records that are hard to keep updated.
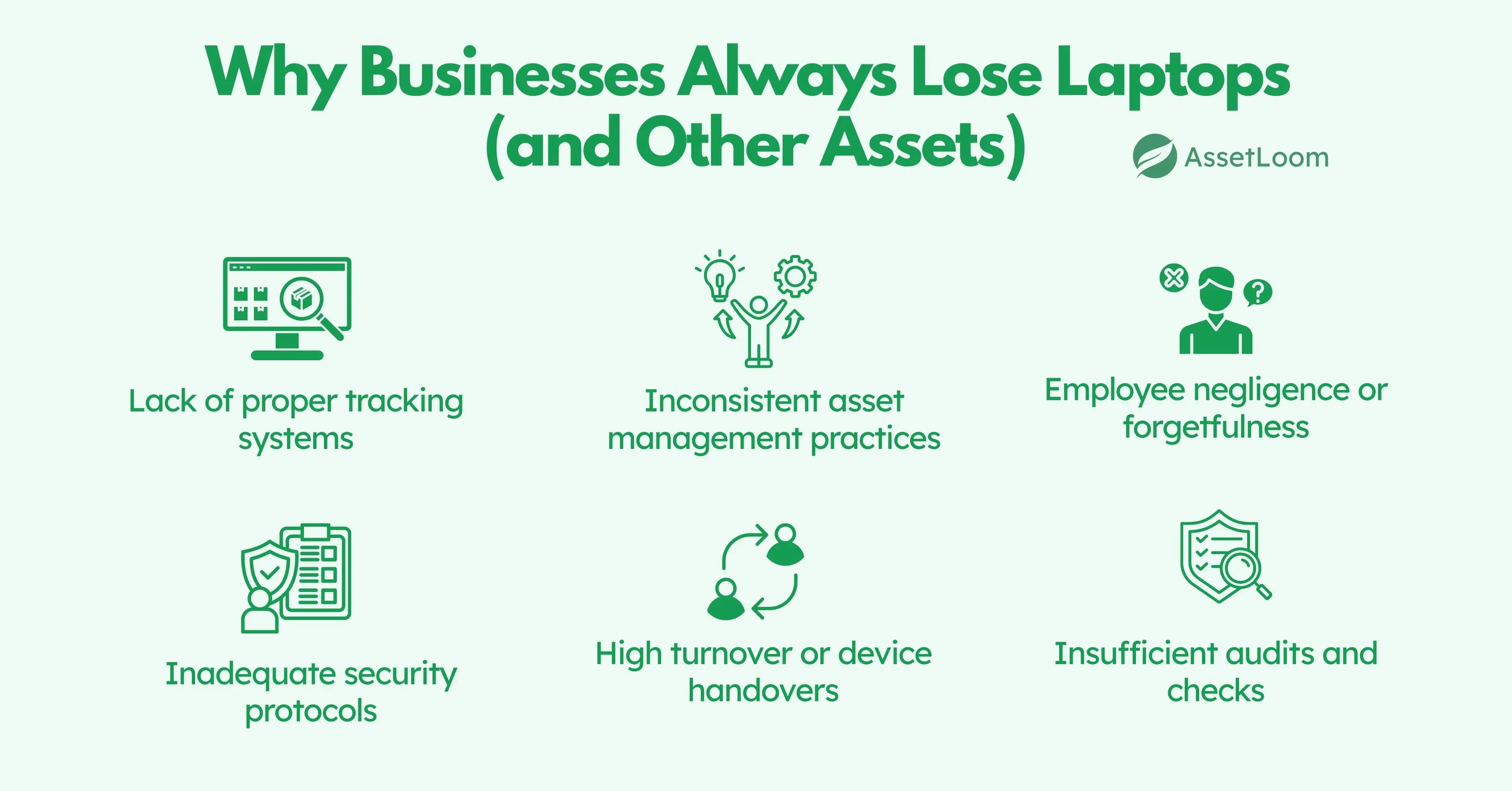
Another reason is the lack of formal check-in and check-out processes. When laptops are handed out casually or passed between departments without proper documentation, no one really knows where the asset is or who’s responsible for it.
Remote and hybrid work setups make this even harder. Devices are constantly moving between locations, and without good tracking practices, it becomes nearly impossible to stay updated in real time.
Some companies also overlook asset tagging. If a laptop isn’t clearly labeled with an asset ID or linked to a tracking system, recovering it after it’s lost becomes much harder. It might as well be just another generic device.
As ITAM expert Barb Rembiesa once said,
“You can’t manage what you don’t know you have.”
That’s exactly why having a clear, reliable system for managing assets isn’t just helpful it’s essential.
Immediate Checklist: What to Do When a Laptop is Lost
When a laptop goes missing, it’s easy to feel like you’re in a race against time. However, taking a calm, organized approach can help you secure your data, involve the right teams, and maximize your chances of recovering the device. Here’s a more detailed step-by-step guide on what to do when a laptop is lost:
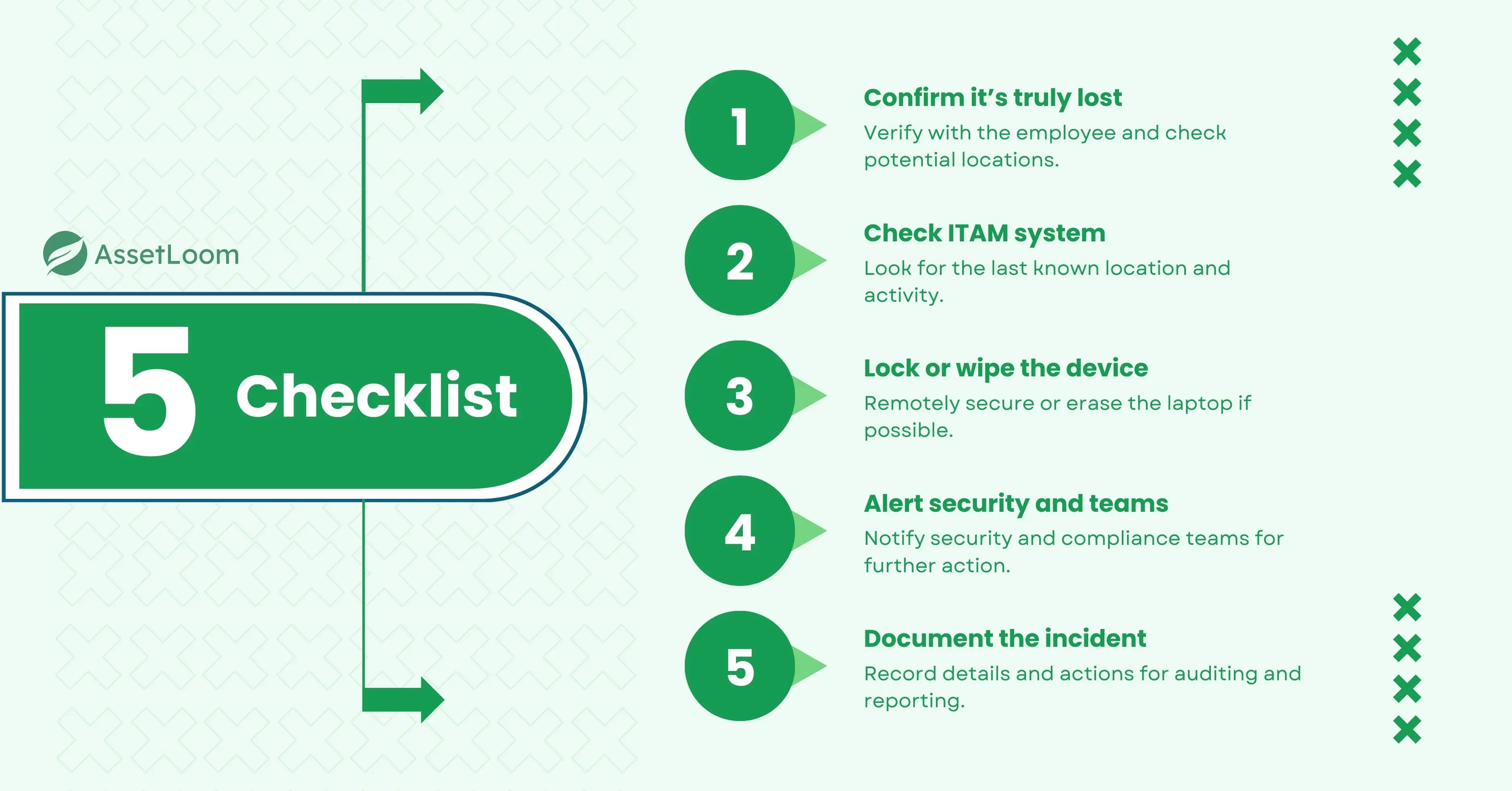
1. Confirm the Laptop is Truly Lost
Before jumping to conclusions, make sure the device is actually lost. Sometimes, employees might misplace the laptop or forget where they last left it. Check with the user to see if the laptop is in their possession or if they have any updates. Confirm whether the device is at a known location (office, meeting room, car, etc.) or if someone else in the team has it.
If you're still unable to locate it, proceed to the next steps. Time is of the essence, so don’t waste too much time on this step.
2. Check Your ITAM System for Last Known Location
Once you're sure the laptop is missing, head straight to your IT asset management system. This system should provide critical information, like the laptop’s last known location, user, and check-in history. Some ITAM systems integrate with mobile device management (MDM) or endpoint protection tools, so you can gather additional data on the device's activity.
For example, check if the laptop was last seen in the office, if it’s connected to the company’s Wi-Fi, or if any recent login or network activity can be traced. This can give you insight into the last known movement of the device.
3. Use Remote Lock or Wipe Features
If your organization uses a remote device management system (MDM) or has remote wiping capabilities, act quickly to lock the laptop. This will prevent unauthorized access to the company’s data and prevent the device from being tampered with.
Some ITAM systems also allow you to trigger a “lost mode” on the device, which can lock the screen, send a recovery message to the user, or track the laptop’s location in real-time if the device is still online. If you believe the laptop cannot be recovered and the risk is high, remotely wiping the device ensures that any sensitive or confidential data on it is deleted.
4. Notify Security and Compliance Teams
After locking the device and securing any sensitive data, it's important to alert your internal security team immediately. They will need to assess the situation, investigate whether the device was stolen or misplaced, and determine if there was any potential breach of security. In many cases, a stolen device can be a serious security threat that requires swift action.
Compliance teams should also be notified, particularly if the laptop contained sensitive customer data or proprietary company information. Different industries, like healthcare or finance, have strict regulations about data breaches. Depending on your organization’s policies, you may need to report the incident to regulatory authorities, especially if there’s a risk of a data leak.
Make sure to document every step and decision as you proceed. This will help protect your organization and ensure that proper steps are followed for both internal and external reporting.
5. Document the Incident and Actions Taken
Documentation is key in managing a lost laptop. As soon as possible, log all relevant details about the incident in your ITAM system. Record the following:
- The date and time the laptop was reported missing
- Who was using the laptop at the time it went missing
- The last known location and activity of the laptop (based on your ITAM system)
- Any actions taken, like locking, wiping, or reporting to compliance
- Communication with security and other departments involved
This documentation serves as an audit trail, providing transparency in case the situation needs to be reviewed later, either internally or for compliance purposes. It also helps with future investigations and can inform your team about potential gaps in your asset management processes.
By following these steps, you’ll be able to act quickly to minimize the potential damage caused by the loss, involve the right teams, and create a solid record of the incident. With the right systems in place, you can help protect your company’s sensitive data and improve your processes for managing lost assets in the future.
The Power of Laptop Asset Tags
When it comes to tracking and recovering lost laptops, asset tags are an essential tool in your IT Asset Management (ITAM) strategy. These small yet powerful identifiers can make all the difference in preventing loss and facilitating quick recovery when an asset goes missing.
Why are asset tags so important?
At their core, asset tags provide a physical link between the laptop and your IT asset records. They allow you to uniquely identify each device and track it throughout its lifecycle whether it's in use, in storage, or in transit.
Without an asset tag, it’s nearly impossible to know which laptop belongs to which employee, department, or office. In the event of a loss, asset tags can be the key to quickly identifying and tracking down the device, even if it’s miles away from its last known location.
Types of Asset Tags: Barcode, QR Code, and RFID
There are a few different types of asset tags you can use to track your laptops. The choice depends on your organization’s needs, the scale of your asset management, and the level of detail you require:
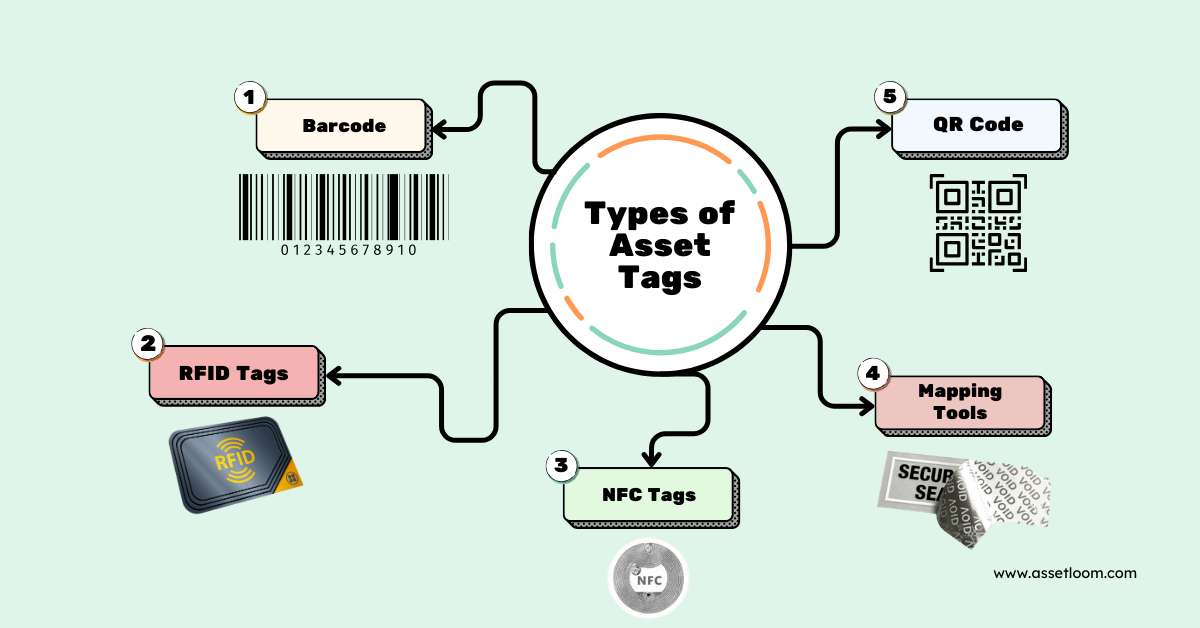
- Barcodes: Barcodes are a simple and cost-effective way to label assets. They can be scanned with a barcode reader to pull up details like the device’s owner, last known location, and purchase date. However, barcodes require a line of sight to be scanned, so they’re less useful for remote tracking.
- QR Codes: QR codes are similar to barcodes but offer more storage capacity. They can be scanned by smartphones or tablets, making them a more flexible option for mobile asset tracking. They can hold more data (e.g., model, serial number, warranty) and can link directly to your ITAM system.
- RFID (Radio Frequency Identification): RFID tags are the most advanced option and are perfect for environments where devices are often moved or stored in bulk. RFID tags allow for non-contact scanning, so you don’t need to have a direct line of sight to track the device. You can track multiple assets at once, making RFID ideal for large-scale operations.
Best Practices to Improve Laptop Asset Tags
Even the best asset tags won’t be effective if they’re not applied or maintained properly. Here are some best practices to get the most out of your asset tagging system:
- Use Tamper-Proof Labels: To ensure that the asset tags remain intact, use tamper-evident or tamper-proof labels. These labels will show visible signs of damage if anyone attempts to remove or alter them, adding an extra layer of security.
- Combine Physical and Digital IDs: Pair physical asset tags with digital records in your ITAM system. For example, each tag could have a unique barcode or QR code, and the corresponding digital entry could include device details, ownership, and location. This dual approach makes asset tracking more accurate and reliable.
- Standardize Your Tagging Process: Create a uniform asset tagging system across your organization. This ensures that all devices are tracked consistently, reducing confusion when assets change hands or locations. Make sure the process is clear and repeatable for employees at all levels.
- Regularly Audit Your Assets: Asset tags won’t be effective if they’re not checked regularly. Schedule regular audits to ensure that all laptops are tagged correctly, and make sure the tags are still visible and legible. These audits can also catch issues with asset movement or missing devices before they become a bigger problem.
- Include Clear Instructions on Tags: For devices that might be found by someone outside your company, include a message on the tag with clear instructions on how to return the laptop. You could add a toll-free number, email, or other contact info to make it easy for a finder to reach you.
The Benefits of Asset Tags in Preventing and Recovering Lost Laptops
Asset tags don’t just help with recovery they also play a crucial role in preventing laptop loss in the first place. By having a clear and consistent system for tagging all devices, employees are more likely to be mindful of their company laptops and more likely to return them when they’re done using them.
Additionally, if a laptop is stolen or lost, having a unique asset tag attached means it’s much easier to track the device back to your company, whether you’re using remote tracking features or working with law enforcement. Asset tags act as the digital fingerprint for each device, ensuring it can be traced and identified even in crowded environments.
Manage Everything with Asset Tracking Software
While asset tags are crucial for physically identifying and tracking laptops, the real magic happens when you integrate these tags with robust asset tracking software. This software serves as the backbone of your IT asset management (ITAM) system, giving you real-time visibility into the location, status, and lifecycle of every device in your organization.
Without the right software in place, managing assets especially laptops becomes a game of guesswork. You might know that a laptop exists, but if you don’t have detailed information about its usage, last check-in, or status, tracking it down when it’s lost can be a nightmare.
Benefits of Asset Tracking Software for Laptop Management
Here’s how asset tracking software transforms the way you manage laptops and other IT assets:
- Centralized Data: Asset tracking software keeps all the critical information about your laptops in one place. You can easily access data such as serial numbers, purchase dates, warranty information, and user details. This centralized approach helps eliminate the confusion that comes with scattered records or manual tracking methods like spreadsheets.
- Real-Time Location Tracking: If your software integrates with tools like mobile device management (MDM) or Wi-Fi tracking, you can get real-time data on where your laptops are and when they were last active. This allows you to track a device even if it’s offsite or in transit. Some systems can even give you a history of a laptop’s locations, making it easier to identify where it might have been lost.
- Automated Alerts: Asset tracking software can send automatic notifications if a laptop leaves a designated area (e.g., the office network), if it's overdue for maintenance, or if its warranty is about to expire. This reduces the chances of a device going missing without notice and ensures you stay on top of your IT asset lifecycle.
- Seamless Integrations: Modern asset tracking software often integrates with other business tools like enterprise resource planning (ERP) systems, helpdesk platforms, or compliance management systems. These integrations make managing your laptops and other IT assets more efficient and ensure your asset data is always up to date.
How Asset Tracking Software Helps Recover Lost Laptops
When a laptop goes missing, asset tracking software is your best friend in the recovery process. Here’s how it helps:
- Access to Historical Data: Many asset tracking systems provide a detailed history of each laptop, including past locations, activities, and user check-ins. This historical data can be invaluable when trying to track down a lost laptop. It helps you identify where the device was last seen, which can lead to a faster resolution.
- Remote Lock and Wipe: If your asset tracking software integrates with mobile device management (MDM) tools, you can remotely lock or wipe a laptop to prevent unauthorized access. This is especially important if the laptop contains sensitive or confidential information.
- Reporting and Audits: In case the laptop is lost or stolen, asset tracking software can generate reports and audits that track the device’s lifecycle. You can document the loss and report it to compliance or regulatory bodies if necessary. This makes the recovery process more organized and ensures all parties are informed.
Choosing the Right Asset Tracking Software for Your Organization
Not all asset tracking software is created equal. When selecting a solution, consider the following:
- Ease of Use: The software should be easy for your team to adopt and use daily. Look for platforms that have a simple interface and intuitive features, especially for employees who are less tech-savvy.
- Customization: Your organization’s needs may differ from others, so ensure the software allows for customization. For example, you might want to track specific laptop details like custom configurations, software licenses, or unique security features.
- Scalability: As your company grows, your asset management system should grow with it. Choose software that can scale to handle more assets, more locations, and more users without compromising on performance.
- Security Features: Since laptops often contain sensitive information, the software you choose should prioritize security. Look for solutions that offer encryption, multi-factor authentication, and other security measures to protect your data.
Integrating Asset Tracking Software with Laptop Asset Tags
To get the most out of your asset tracking software, integrate it with your laptop asset tags. This integration allows for automatic syncing between physical and digital records, which reduces human error and makes the tracking process seamless.
For instance, when an asset tag is scanned, the software can instantly pull up the device’s details such as its status, location, and user without requiring manual entry. This level of automation saves time and ensures that all your data is accurate and up to date.
Conclusion: Securing Your Laptops and IT Assets
The security and management of laptops are an essential part of any organization's IT asset management (ITAM) strategy. While losing a laptop is always a challenge, implementing the right systems and practices can help minimize the impact and even prevent the loss from happening in the first place.
From using asset tags and asset tracking software to developing clear security policies and conducting regular audits, a proactive approach to managing your devices is key. By combining these tools and strategies, you create a robust ITAM system that not only secures your laptops but also streamlines asset management and ensures that your devices are always accounted for.
Ultimately, preventing laptop loss and managing it effectively when it does happen comes down to maintaining control, using the right tools, and educating your team. By fostering a culture of responsibility and investing in the right technology, you’ll reduce the risks associated with lost laptops, protect your organization’s sensitive data, and improve your overall IT asset management practices.
With the right measures in place, your company can focus on growing and innovating without the constant worry of asset loss disrupting your operations.

Related Blogs
Subscribe for Expert Tips and Updates
Receive the latest news from AssetLoom, right in your inbox.


